As organizations experience a strong sense of uncertainty in the security of their systems, new approaches are required to improve the security of applications and prevent potential attacks early in the software development life cycle (SDLC). Threat modeling software provides a proactive approach to operational and application security of any organization.
Threat modeling is a critical step in the development of any application. Without it, your protection is in the dark. Let’s look at threat modeling in the medical and health insurance realm. What happens when you don’t have health insurance? Everything in life seems to move swimmingly until you are exposed to a potential risk. If you had been covered with health insurance since day one, your chances of ailing and breaking your bank would be significantly reduced.
Continuing with the health insurance parallel, low-coverage medical insurance may be considered “cheating” for many. Why? When emergencies take place, your health insurance company will help a little, but in the end, you might as well cover most expenses. The same thing happens when you are lacking protection for your applications. Enterprises need to make sure their assets are protected to save valuable time, effort, and money in the long run.
Threat Modeling Software vs. Threat Mapping: What’s the Difference?
Many people confuse threat modeling software with threat mapping. Threat mapping is the process of identifying threats and looking for feasible solutions to mitigate those threats. When building threat maps, security decision makers are predisposed to making errors due to the ambiguity of the maps.
While threat mapping is an approach to secure applications, it lacks automation and accuracy to deliver actionable outputs. From Excel sheets to Microsoft Word and even Microsoft Paint, a threat map can be built anywhere. The process of threat mapping is complicated, and in the long run, you’ll spend more time, money, and effort trying to protect your system with an unreliable approach. If we look at threat mapping by using the health insurance example, low-coverage insurance would represent threat mapping while the high-coverage insurance is your threat modeling software.
Learn More: Getting Started with Threat Modeling: How to Identify Your Mitigation Strategy
Advantages of Threat Modeling Over Threat Mapping
Threat modeling offers automation, integration, and collaboration in one platform. A threat modeling software builds proper threat models including an architecture diagram, threat library, web server, operating system layer, and the infrastructure of the system. When using an automated threat modeling software such as ThreatModeler, you can build the architecture diagram by using a template, a diagram wizard, or you can create one from scratch.
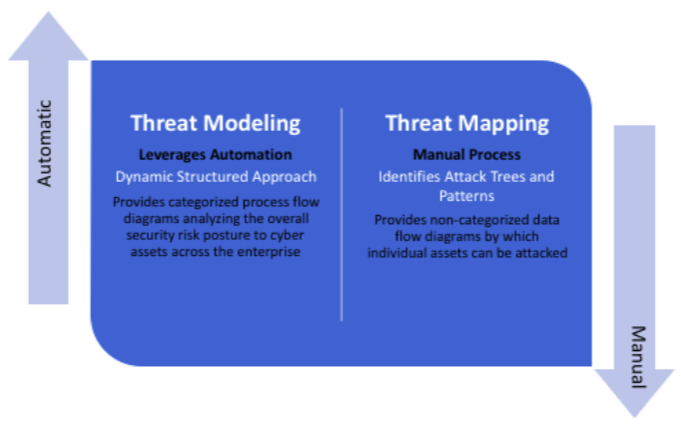
Threat mapping can compromise your application and its data, increasing the attack surface while introducing new threats, due to its feeble and vulnerable approach. Some of the advantages of building a threat modeling process include:
- Customized and extensive threat library
- Identification of components that may be impacted by potential threats
- An accurate and up-to-date risk profile
- Elimination of security issues in the design stage
- Prioritize testing efforts based on identified threats
- Production of actionable output
- Detailed mitigation strategies
- Leverage of real-time threat intelligence
ThreatModeler is an automated threat modeling solution that strengthens an enterprise’s SDLC by identifying, predicting and defining threats across all applications and devices in the operational IT stack. Security and DevOps teams are empowered to make proactive decisions from holistic views and data analytics of their attack surface, enabling enterprises to minimize their overall risk.
To learn more about how your organization can identify security threats during the SDLC for faster, smarter, more secure application production, request a free evaluation of the ThreatModeler platform or contact us to speak with an application threat modeling expert today.





