Intelligent Automation
Generate and update models from artifacts in minutes with automation that adapts as systems evolve.
Automated Threat Modeling is Now
Built for the cloud- and AI-connected enterprise.

Comprehensive coverage ensures faster, non-disruptive identification and remediation of threats — from applications to infrastructure to connected devices.

Identify critical risks with built-in threat intelligence.
Deploy security controls with turnkey solutions.
Visualize infrastructures, architectures, and app environments.
Generate and update models from artifacts in minutes with automation that adapts as systems evolve.
Maintain always-on visibility into residual and emerging risks so security keeps pace with modern development.
Receive context-aware recommendations that surface critical risks and guide security control placement.
Connect applications, infrastructure, and devices into a unified view of enterprise risk for clarity and confidence at scale.
Secure Apps
by Design
Secure Code
to Cloud
Secure Cloud Infrastructure

Advanced
Automation
Adaptive
AI/ML
AI Assistant
Next-Gen
Frameworks
Expansive
Threat Libraries
Built-in
Compliance
Advanced Integrations
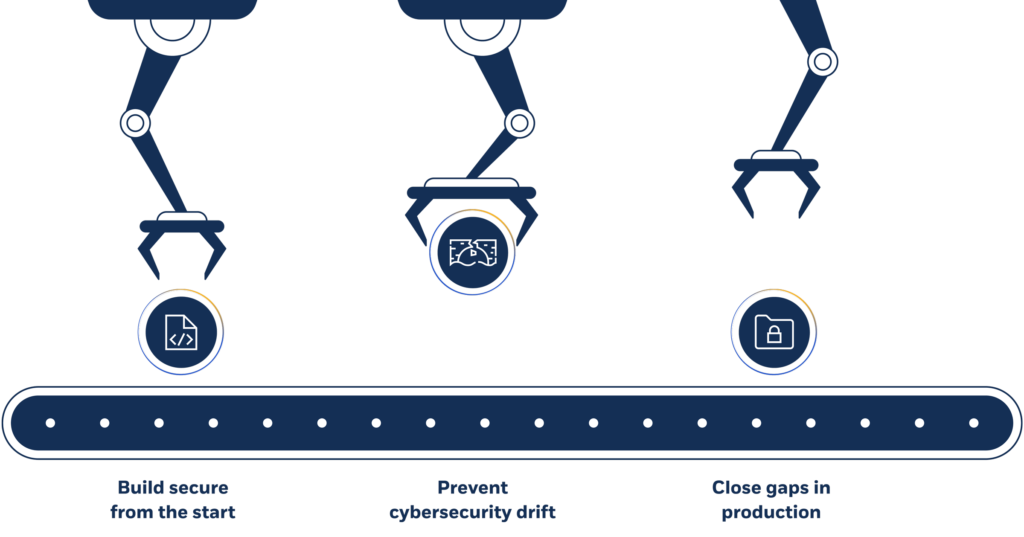
Remove roadblocks.
Automate threat modeling at scale and significantly reduce the time, effort, and resources needed for comprehensive risk assessments and mitigation.
Mitigate threats on premises, in the cloud, and at the edge with extensible threat library.
Achieve secure-by-design posture with architecture and design integration points.
Prevent security gaps and cybersecurity drift with continuous threat modeling.
Push security requirements directly into developer sprints with native integrations.
Innovate securely.
Integrate threat modeling into CI/CD pipelines, address risks directly within development cycles, and reinforce security without disrupting the pace of innovation.
Proactively mitigate threats during design and build with built-in threat intelligence.
Quickly validate designs during artifact import to prevent surprises in production.
Embed threat modeling within your agile software delivery toolchain.
Shift-left security with threat identification for Infrastructure as Code (IaC).
Safeguard the cloud.
Identify and address infrastructure risks from anywhere in your Cloud Development Life Cycle (CDLC).
Safeguard IaC with a developer-friendly plugin.
Create connected models with live cloud infrastructure for continuous risk identification and mitigation.
Achieve consistency with nested models, templates, and AI-assisted creation.
Automatically map top cloud threats and recommended security controls.
2,500+
security requirements
180+
compliance frameworks
1500+
threats
2900+
components
100+
protocols

See how Charles Schwab protected their apps
and infrastructure while reducing the burden
on security and development teams by over 50%.
COMPANY SIZE
Enterprise
INDUSTRY
Finance


EBook
Ultimate Guide to Threat ModelingTake a proactive and strategic approach to identifying threats across your apps, infrastructure, and code

White Paper
Threat Modeling Benefits for the CISOFind out how you can impact every aspect of your organization with actionable security benefits
