With Meltdown and Spectre, 2018 could set a new standard for the “year of the cyber-attack.” Getting on top of these critical vulnerabilities will require enterprise threat modeling. Meltdown and Spectre recently discovered hardware vulnerabilities affecting chips produced by Intel, AMD, ARM, and Qualcomm, expose affected devices to kernel attacks.
Almost everyone, from home computing gamers to Fortune 100 enterprises, will feel the impact of these vulnerabilities. Hardest hit may be large companies providing critical infrastructure such as transportation and healthcare as any downtime to address the issue may seriously impact the services provided.
ThreatModeler Releases Security Update for the new Vulnerabilities
Addressing the impact of these threats will be a significant undertaking for Fortune 1000 companies with potentially many thousands of machines affected. Organizations will need to understand quickly where their IT environment is impacted, where the patches can be implemented, and where security and performance demands will require hardware replacement.
The ThreatModeler Software team has been hard at work to deliver the latest threat intelligence updates to their customers, providing the needed visibility into the impact of these vulnerabilities and their associated threats across their entire organization.
The new threat intelligence updates will allow ThreatModeler™ users to determine where the vulnerabilities are relevant and to quantify any downstream impact with the click of a button. “This level of automation and visibility into emerging threats are significant differentiators for us,” said Mark Meyer, Chief Revenue Officer of ThreatModeler. “These are the reasons why ThreatModeler is increasingly relied upon by Fortune 1000 companies.”
“It is essential that organizations develop a full understanding, as quickly as possible, the relevance and impact of these vulnerabilities and how any related threats may affect their business,” added Archie Agarwal, Founder and CEO of ThreatModeler. “At least two attack strategies around Spectre have already developed in the wild. Seeing more is only a matter of time.”
As soon as ThreatModeler customers download the security update, their entire threat model portfolio will be automatically updated. As a result, organizations will have immediate visibility to the organizational impact, risks, and possible mitigating controls relevant to Meltdown and Spectre.
Understand the Impact of Meltdown and Spectre
Meltdown and Spectre are chip-level hardware vulnerabilities affecting the speculative execution commands of kernel software across nearly all operating systems. In a nutshell, this means that an attacker could access the contents of protected kernel memory including cryptographic keys, passwords, or any other sensitive data being processed.[1]
On a per-device basis, the vulnerabilities themselves are serious. The more significant issue, however, is the impact breadth. Affected chipsets are part of IoT systems, computing endpoints, infrastructures, and legacy systems. Cloud-based deployments are a particular concern. Though an attacker cannot directly access a virtual machine using Meltdown or Spectre, the vulnerabilities will allow attackers significant lateral mobility after accessing a local system.
“I don’t think we can yet pinpoint a particular industry that will be targeted more than others based on these vulnerabilities,” said Agarwal. “But based on recent attack history, any company in the ICS, Transportation, Healthcare, Retail, and Financial sectors – as well as companies with a large IoT footprint – need to do everything possible to understand the vulnerabilities and the potential threats involved fully.”
Threat Modeling vs. Threat Mapping: The Difference is Crucial
Understanding threats is a matter of degrees. An individual consumer, for example, only needs to understand that Meltdown and Spectre present a new set of threats and wait to receive any broadcast security patches and updates. A Fortune 1000 enterprise, on the other hand, with potentially multiple thousands of affected devices and petabytes or even exabytes of sensitive data to protect, requires a deeper understanding of impact and risk.
An improvement on consumer-level understanding comes from threat mapping. Threat mapping is, typically, a highly manual process by using data flow diagrams by which provide basic information regarding how certain assets may be attacked. Threat mapping is generally used only on an individual application basis, and then only considers that application in isolation. Applying threat mapping to situations beyond the scope of a single application quickly becomes too complicated.
Threat modeling, on the other hand, uses process flow diagrams to analyze the overall risk posture to cyber assets across the enterprise. It is through the threat modeling process that organizations are able to understand the full impact of specific threats and vulnerabilities from the point of attack initiation, through the infrastructure, to any of the exposed system assets.
A key differentiator in this respect between threat mapping and threat modeling is the latter includes analysis of application interactions, shared components, and 3rd party systems. Threat modeling provides enterprises with extensive IT environments to fully understand the relevance and impact of threats and vulnerabilities from attack surface to assets throughout their highly interconnected cyber ecosystem.
Automated Threat Modeling for Meltdown and Spectre
Consider a typical computing endpoint threat model created with the ThreatModeler Platform:
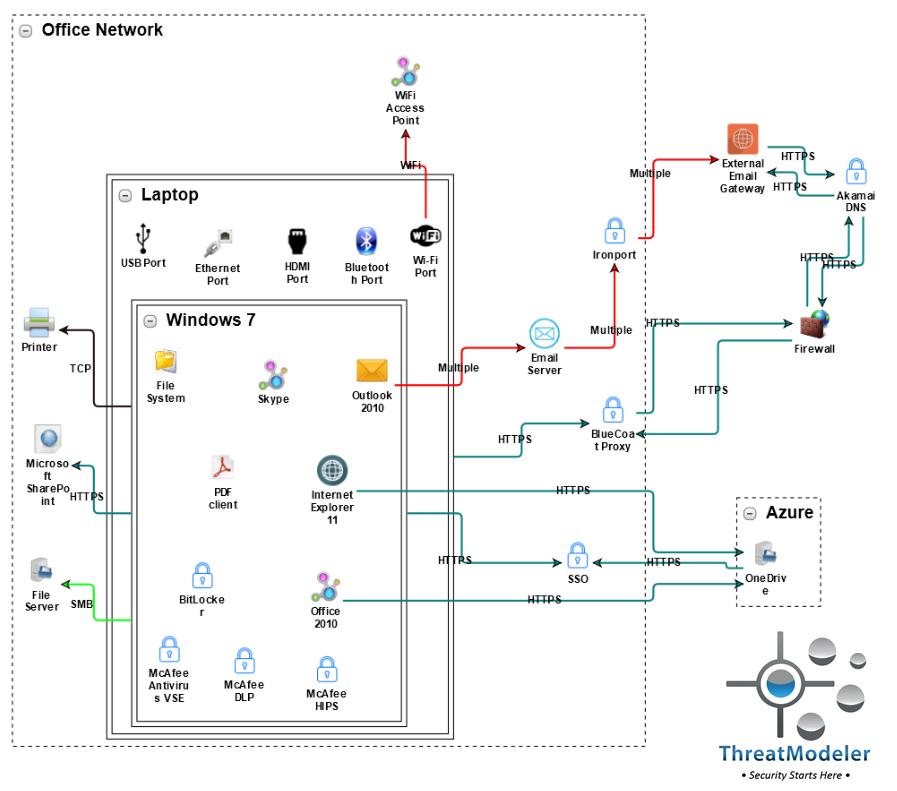
This threat model includes a Windows 7 laptop with a connection through a single sign-on to the Azure cloud, external email service, and connection to the organization’s file server and SharePoint.
As soon as the new threat intelligence update from ThreatModeler Software is downloaded into the organization’s ThreatModeler™ instance, the outputs of the above threat model will include the CVE definitions for Meltdown and Spectre, the potential threats and risks exposure from the vulnerabilities, and the relevant security controls. ThreatModeler’s automated threat modeling platform, however, goes much further than merely updating individual threat models.
Consider that in the enterprise environment, the laptop modeled above may be connected to the organization’s cloud-based or on-premises infrastructure. This can be modeled in ThreatModeler™ by including the above threat model into the banking operational threat model shown below:
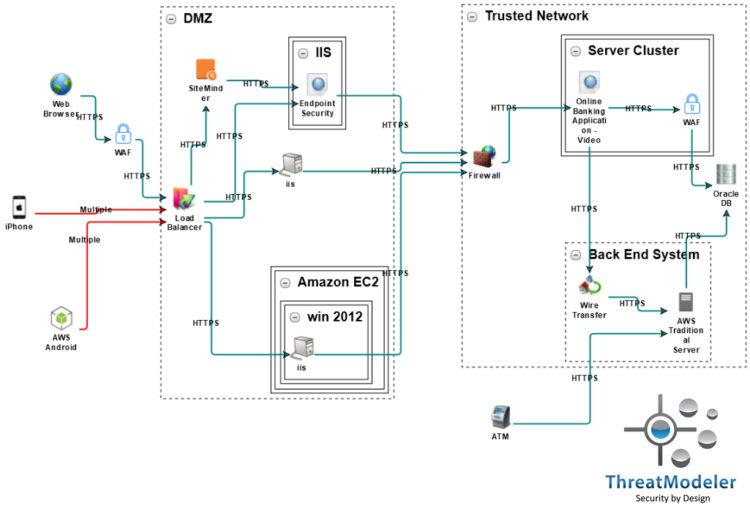
Learn how to make real-time threat intelligence actionable in your organization. Schedule a live ThreatModeler demo.
[1] Agarwal, Archie, “The Broad Impact of Intel Chip Issues.” Cheddar: New York. January 8, 2018.





