Reporters around the globe are writing and watching as IoT security takes another dark turn with a new botnet. The new beast, dubbed IoTroop – sometimes also referred to as Reaper – has the potential to dwarf the infamous Mirai botnet that crippled Dyn last year with a 990 Gbps DDoS attack.
IoTroop makes uses of some of the same code as Mirai, but goes about recruiting far more effectively. When Mirai hit Dyne, analysts estimate that 100,000 infected devices were employed. [1] To date, IoTroop has infected more than 2 million devices from at least one million organizations. [2]
IoTroop’s recruiting differences from Mirai stems from the former’s ability to capitalize on nine known vulnerabilities common to IoT devices. Of particular concern for the spread of the malware is IoTroop’s use of CVE-2017-8225. This vulnerability allows IoTroop access to the attacked devices’ .ini files which store user credentials.Bypassing device authentication can be accomplished by passing empty loginuse and loginpass parameters to the device. [ 3]
3]
While the vulnerability is predominantly found in IP cameras, it can also be used to attack Linux servers, Synology NAS devices, and MicroTik and TP-Link routers. The troubling news is that an estimated 60% of corporate networks worldwide contain at least one device that is susceptible to IoTroop’s list of targeted vulnerabilities.
The National Vulnerability Database lists CVE-2017-8225 as a critical vulnerability, with a calculated base score of 9.8 out of 10. The vulnerability is capable of causing a total loss of confidentiality, integrity, and availability of data and systems. Moreover, attacks utilizing the vulnerability do not require a high degree of expertise, skills, or resources; the attacks may be highly automated, and attackers can expect repeated success. However, the severity of the vulnerability is not the awful news.
What is genuinely concerning is that attacks using CVE-2017-8225 can be weaponized for significantly increase scalability. Already researchers have uncovered two scripts in use can be used to combine the CVE-2017-8225’s severity with the global reach of Shodan’s IoT device search capabilities.
The first script – a Shodan dork (query string) – dumps the IP address of any device susceptible to CVE-2017-8225, thus allowing IoTroop command and control servers to quickly and precisely identify a vast trove of devices for recruitment. The second script, used in the attack on each identified device, will dump the device’s credentials to IoTroop’s C&C servers. [4] The CVE-2017-8225 + Shodan attack efficiently neutralizes the IoT cyber security best practices steps of removing factory set credentials and providing your strong ones.
Why is IoT Security Always a Secondary Concern?
It does not take an industry specialist to understand that, on the whole, IoT security is lacking. Perhaps one could argue that Mirai caught the market off guard. However, using the Mirai code as a template, Persirai became a global threat only eight months later.
The Persirai botnet can be used to conduct a User Datagram Protocol via SSDP-based DDoS attack, which eliminates the need for IP address spoofing. Did we learn our lesson? It would seem not – only six months later, IoTroop has amassed a zombie-device army numbering in the millions, and it is still growing.
It is not that our collective technological acumen is insufficient to secure IoT ecosystems. IoT “things” – are so-called “smart” devices because they interact with web-based applications by connecting the device to the Internet through a gateway. We have been securing applications for decades. We can secure the cloud-based systems which deploy the applications. It is the devices themselves that are not secured. Securing the devices is not a technological problem, though, it is an economic problem.
Whenever a person makes a major purchase, whether to buy a home, a new car, or even a major appliance, certain decisions need to be made. Unless the buyer has unlimited financial resources, a significant part of that set of decisions involves prioritizing “must-have” features against those that are merely “nice-to-have.”
In a recent survey, 90% of respondents stated that the convenience of connected devices is valuable, whereas only 54% stated that security with said devices is also important. [5] Other market research, however, demonstrated that when the security issue is non-personal – such as when an IoT device is used for a DDoS attack – only 15% of the market remains concerned. [6]
When making purchasing decisions based on prioritized features, security takes a back seat to convenience almost every time. For IoT manufactures who are already working with narrow margins on commoditized offerings, this means rolling out “convenient” products at the lowest possible price. The downside of this “race to the bottom” is that security features – which require additional processing power and storage – have no place in the mass-produced, volume sales world of minimum viable products.[7]
According to Gartner’s estimates, there will be more than 20 billion connected “things” by 2020. [8] If only 100,000 “things” marched against Dyn in the massive DDoS attack last October, what will IoTroop be able to do with more than two million recruited devices? Where will we be in another three years at the current rate of new connected “things?”
Increasing IoT Security is Good Economics
The beautiful things – at least from a threat agent’s perspective – in utilizing IoTroop, Persirai, or Mirai for a DDoS attack is that it does not require a lot of resources or skills. Even a so-called script-kiddie can wield them effectively. However, just because the potential attack only requires the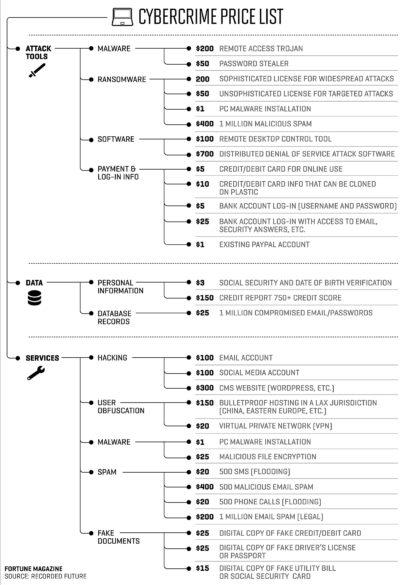 sophistication of an untrained kid is no reason to consider the threat as minor. Script-kiddies were blamed for using Mirai to bring down Dyn in 2016.[9]
sophistication of an untrained kid is no reason to consider the threat as minor. Script-kiddies were blamed for using Mirai to bring down Dyn in 2016.[9]
The motive for attacks resulting in data breaches are well-understood – the attackers want to use the stolen data to turn a profit. Interestingly, though, information is a low-priced Dark Web commodity.
The big money-maker for attackers – especially for those lacking the skills and of a state-sponsored group – is in tools for a targeted DDoS attack. The weaponized scale of IoTroop can be leveraged by attackers for either precision or wide-spread DDoS attacks as an on-demand service.
Furthermore, since IoTroop utilizes nine different vulnerabilities affecting as many as 60% of organizational networks worldwide, the threat of a loss of availability from a DDoS attack is not the only threat for which organizations need to prepare.
The utilized vulnerabilities can also be used, for example, to weasel into an organization’s IT system through an IoT device. Alternatively, IoTroop can be utilized as an anonymity network or distributed proxy. [10]
The potential threats are real. Even if a DDoS attack is not a significant organizational concern, the possibilities that can be realized by a zombie army of 2 million or more devices are many and significant. Considering that such threats will likely result in a total loss of availability for an organization’s customer base, a material or devastating loss of data confidentiality, or could enable serious and malicious modifications to components or data, [11] making IoT security a priority only makes economic sense.
Invest Economically in IoT Security
 The simple part of IoT security is convincing executives to make it a strategic organizational priority. More challenging, though, is finding a way to develop security economically, sustainably, with an ROI that wins executives’ approval.
The simple part of IoT security is convincing executives to make it a strategic organizational priority. More challenging, though, is finding a way to develop security economically, sustainably, with an ROI that wins executives’ approval.
Getting a handle on the organization’s IoT security is a significant task since each part of the ecosystem is subject to its own security considerations. Each part of the IoT system, then, needs to be understood in the context of the organization’s overall cybersecurity.
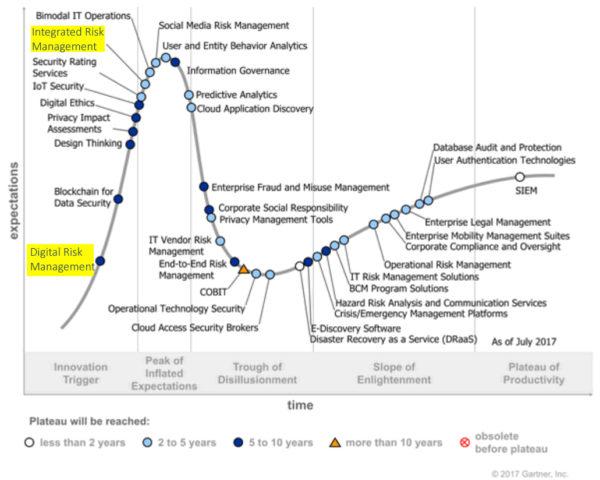
Gartner included ThreatModeler in their Hype Cycle for Application Security, 2017 as a part of the ASRTM category. Gartner noted that ThreatModeler automates “security requirements definition, risk assessment, and threat modeling,” with SDLC integration, which “can dynamically highlight potential security ramifications of functional requirements.”[12]
ThreatModeler, however, is a cybersecurity solution with far more capabilities that go far beyond AppSec tools. With ThreatModeler, organizations can create detailed and extensive threat models of their IoT systems….
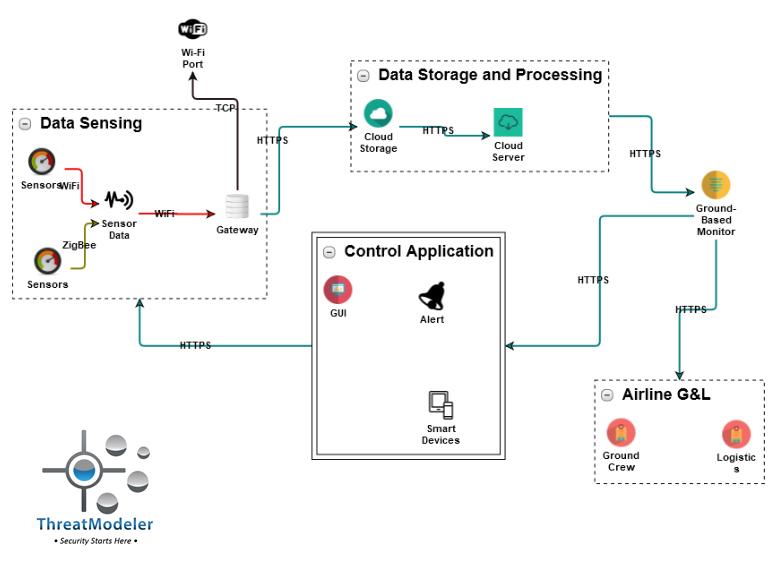
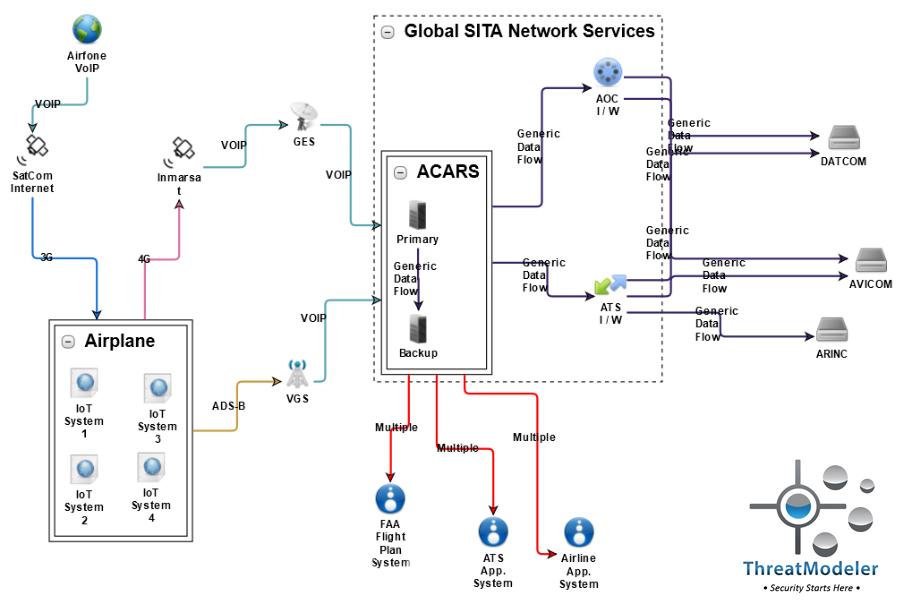
….and analyze the interactions of their IoT systems, such as may be necessary on an IoT-enabled aircraft,
….and study potential weakness in the IT system from an IoT-enabled attack, such as may occur against an organization’s sensitive data through a WiFi access point for endpoints:
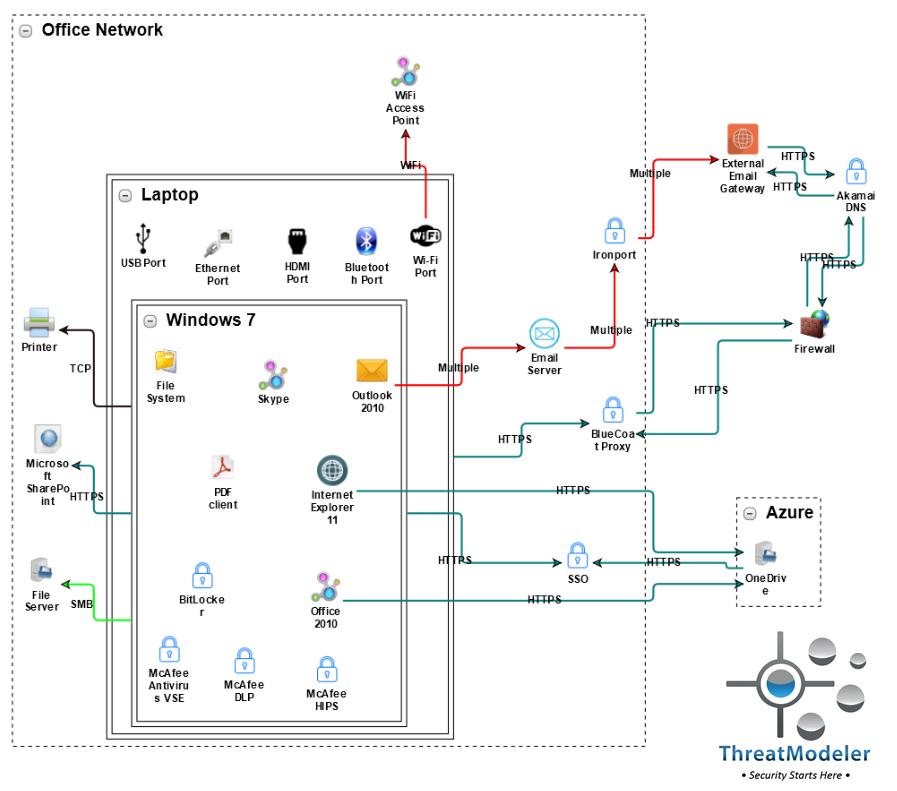
Through the analysis of individual IoT systems, how they interact and identifying potential weak spots to an IoT-based attack, organizations can create economical, holistic solutions to their IoT security.
Click here to schedule a live demo with a ThreatModeler expert today and learn how to develop an economical, sustainable approach to IoT security for your organization.
[1] Kan, Michael. “DDoS attack on Dyn came from 100,000 infected devices.” Computer World. IDG: Boston. October 26, 2016.
[2] Davis, Jessica. “Massive botnet quietly harvesting 2 million vulnerable IoT devices, report says.” Healthcare IT News. HIMSS Media: Chicago. October 26, 2017.
[3] “CVE-2017-8225 Detail.” National Vulnerability Database, Information Technology Laboratory. National Institute of Standards and Technology: Gaithersburg. April 25, 217.
[4] Spring, Tom. “Hackers Prepping IoTroop Botnet with Exploits.” Threatpost. The Kaspersky Lab Security News Service: Woburn. October 25, 2017.
[5] “The Impact of Trust on IoT.” Mobile Ecosystem Forum. Mobile Ecosystem Forum Ltd: London. April 2016.
[6] Meyer, David. “IoT convenience versus IoT risk – a thin line to tread?” Internet of Business. Vinelake Limited: Boston. June 14, 2017.
[7] Porup, J.M. “’Internet of Things’ Security is Hilariously Broken and Getting Worse.” ARS Technica. Condé Nast: New York. January 23, 2016.
[8] “Gartner Says 8.4 Billion Connected ‘Things’ Will Be in Use in 2017, Up 31 Percent From 2016.” Press Release. Gartner, Inc: Stamford. February 7, 2017.
[9] Lomas, Natasha. “Dyn DNS DDoS Likely the Work of Script-Kiddies, says Flashpoint.” TechCrunch. Verizon, Inc: Basking Ridge. October 26, 2016.
[10] Kebs, Brian. “Reaper: Calm Before the IoT Security Storm?” Krebs on Security. October 17, 2017.
[11] “Common Vulnerability Scoring System Calculator Version 3 – CVE-2017-8225.” National Vulnerability Database, Information Technology Laboratory. National Institute of Standards and Technology: Gaithersburg. April 25, 217.
[12] Tirosh, Ayal. “Hype Cycle for Application Security, 2017.” Gartner. Gartner, Inc: Stamford. July 28, 2017.





