Reduced car accidents and congestion, lower energy usage, increased mobility and access to essential and desired information, plus increased productivity are some of the oft-heralded benefits of the ever-expanding IoT-powered ecosystem. With all these new innovations, IoT cybersecurity is struggling to keep up with the pace.
The current level of IoT cybersecurity is generating a global risk that is garnering increased attention. In 2017, for example, there were nearly a billion more IoT devices than people on the planet. The size of the global connected device footprint is expected to proliferate to 20.4 billion by 2020. The burgeoning number of connected devices – both large and small – is creating an environment in which cyber attacks are reaching pandemic proportions.
For example, an IoT-enabled 100 Gbps DDoS attack was once considered exceptional. Thanks to the number of new devices, the frequency of such attack jumped by 140% in 2016 alone.[1] Moreover, attackers have recently raised the bar on the size of DDoS attacks by a factor of 17 thanks to a discovered vulnerability with Memchached-enabled servers.[2]
Attacker’s Perspective for IoT Cybersecurity
A targeted DDoS attack may not be something that touches the average family, but attacks on or through IoT devices can get personal. Consider an internet-connected automobile. The sensors, actuators, and other IoT devices themselves are just the tip of a massive cyber ecosystem iceberg. The full system includes cloud-based and traditional deployment environments, multiple interacting applications, interconnectivity with 3rd party systems, and potentially hundreds of millions of lines of code.
According to Chuck Brokish, Director of Automotive Business Development at Green Hills Software, increasing IoT cybersecurity by securing every line of code that goes into a connected automobile impractical.[3] As a result, the standard position of car manufacturers and their vendors is to secure only the “critical” components.
With a little know-how and a few off-the-shelf components, however, an attacker can infiltrate a connected automobile’s “less critical” systems and take over the breaks, engine, navigation, and other functions. The result, as researchers discovered, is that attackers could remotely strand the occupants or expose them to a severe accident.
Developing end-to-end IoT cybersecurity can be a complicated undertaking, whether for connected automobiles, aircraft, or a smart home. However, securing “critical” systems while overlooking those deemed “less critical” is an open invitation to innovative attackers.[4]
A broad problem in IoT cybersecurity is the tendency to look at applications and systems from a use-case perspective. Applications and systems are designed around business requirements and specific use-cases that will efficiently deliver the business requirements. The reality, though, is that attackers have very little concern or respect for the business-as-usual use case perspective. Their view is based on abuse-cases that take them from the attack surface to whatever end goal they have in mind.
Prioritize Security Resources
You cannot effectively secure everything, according to the legendary Prussian strategist Frederick the Great. However, neither can you prioritize your IoT cybersecurity strategy based on a use-case perspective. Skilled attackers do not waste resources storming the castle gate. They look for the innocuous drain at the base of the wall – the point that everyone else deemed a “non-critical” component.[5]
A breach is an inevitable conclusion once attackers enact an abuse-case is against the innocuous “drain.” IoT cybersecurity fails – broadly speaking – because we do not dynamically prioritize our resources based on the attackers’ perspective.
The issue is not to address Brokish’s complaint about “securing every line of code.” Rather, it is to develop a consistent end-to-end IoT cybersecurity policy, cost-effectively, with the highest ROI – and to develop and maintain that policy at the speed and scale of innovation. This is where automated enterprise threat modeling is mission-critical.
Threat modeling has long been part of the arsenal for securing new critical and high-risk applications. However, enterprise threat modeling expands the reach of threat modeling across the full cyber ecosystem – including IoT and embedded devices. Threat modeling will not specifically create or implement the security – it is not a defensive technology. What it does provide, however, is the actionable understanding needed to create a secure cyber environment – whether for an application, an enterprise IT system, or a connected automobile.
Threat Modeling a Connected Vehicle Ecosystem
Considering the cyber ecosystem of a connected automobile: an enterprise threat model may be built from an architecturally-based diagram:
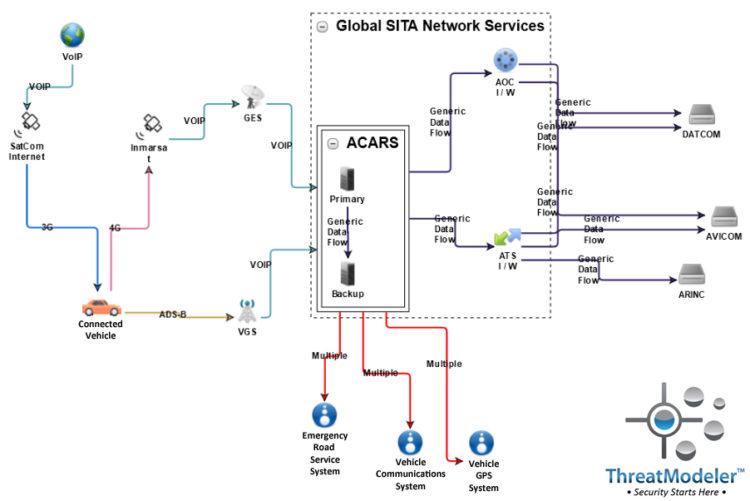
The diagram may be expanded to show the vehicle’s onboard connected devices as additional nested diagrams:
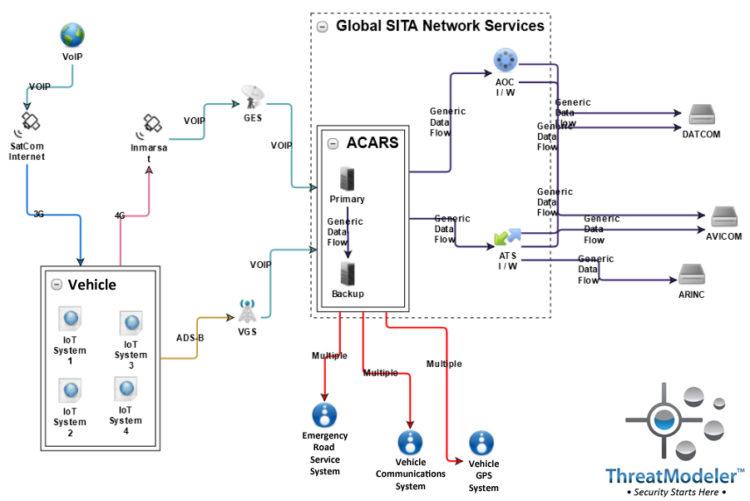
Each of the nested diagrams describing the vehicle’s onboard connected systems may be further expanded to show their detail. For example, the diagram for IoT System 1 shows another layer of the complexity of the IoT ecosystem being threat modeled:
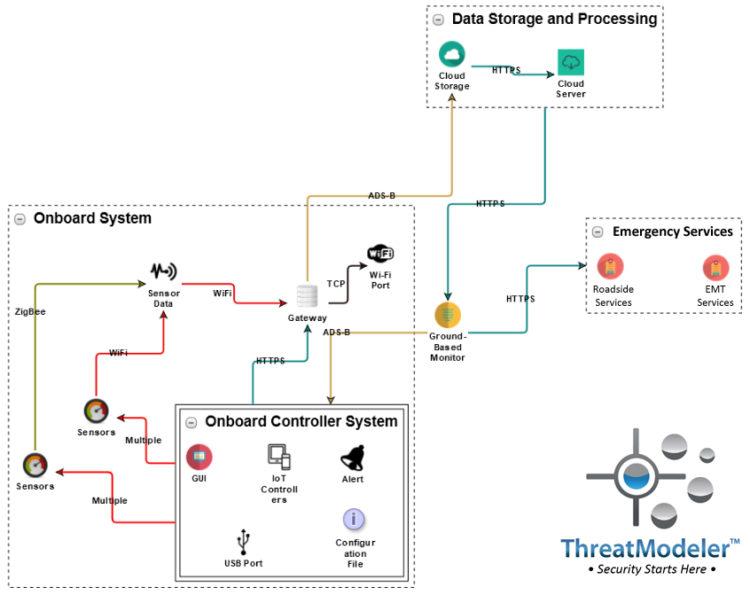
Securing then end IoT devices or the “hundreds of millions of lines of code” in a connected vehicle are misdirected uses of limited security resources. Moreover, even if it were possible to secure all the devices and related lines of code, tomorrow’s innovation will soon relegate our Herculean accomplishment to the archives of irrelevancy.
What’s needed is a “big picture” view of the connected vehicle’s full cyber ecosystem from the attacker’s perspective. The only way to achieve this – and thereby develop quantifiable and consistent end-to-end security – is through enterprise threat modeling.
Learn more about how automated enterprise threat modeling yields quantifiable, consistent, enterprise-wide security policy at the pace of innovation – click here to schedule a demo with a ThreatModeler expert.
[1] Collins, Aengus, etal. The Global Risks Report 2018, 13th Edition. World Economic Forum: Geneva. January, 2018.
[2] Tung, Liam. “New World Record DDoS Attack Hits 1.7Tbps Days after Landmark GitHub Outage.” ZDNet. CBS Interactive: San Francisco. March 6, 2018.
[3] “Can Cybersecurity Keep Pace with Connected Car Innovation?” International Telecommunication Union. United Nations: New York. March 9, 2018.
[4] Dawson, Chester. “Car’s Data Transmitter Can Be Hacked to Take Control, Firm Says.” The Wall Street Journal. Dow Jones & Company, Inc: New York. April 14, 2017.
[5] https://www.youtube.com/watch?v=qBiA8qaLxbI






