Satellite systems are an indispensable part of our cyber ecosystem. We have depended on them almost as long as we depended on shared computing.[1] However, despite their ubiquitous nature and our level of dependence, we often disregard satellite security.
We depend on satellites for much of our global communications bandwidth. Without our satellite system, our terrestrial data networks and undersea cables are quickly overwhelmed. It is unlikely we would have a functional Internet. Most cell phones and mobile devices would become as useful for communication as bricks. And many places around the world would not have television or other services.[2]
Satellite Security for its Own Sake?
Satellite security is important in ways beyond convenient communication, though. Worldwide logistics, a functioning global supply chain, even personal transportation depends on satellites. GPS systems help with charting fuel-efficient routes and preventing accidents. Moreover, GPS systems provide synchronized timing for everything from power grids to the financial sector.
There are literally thousands of active satellites upon which we depend. The network serves as the central nervous system for the military, the economy, and science. Yet for our dependence, few people give satellite cybersecurity a second thought.
Much of satellite security focus on defense-in-depth designs with multiple system redundancies. Despite the design and redundancies, though, all satellites are subject to a universal weakness. They must communicate with ground stations through long-range telemetry. Often uplinks and downlinks are conducted through well-known, open telecom network security protocols such as TL1. Open protocols, along with the obvious treasure trove of data and information passed by satellites makes them very attractive to attackers.[3]
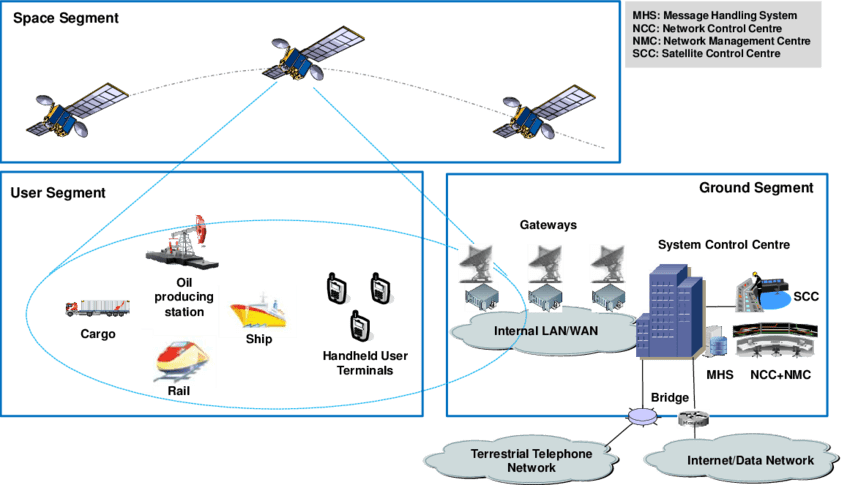
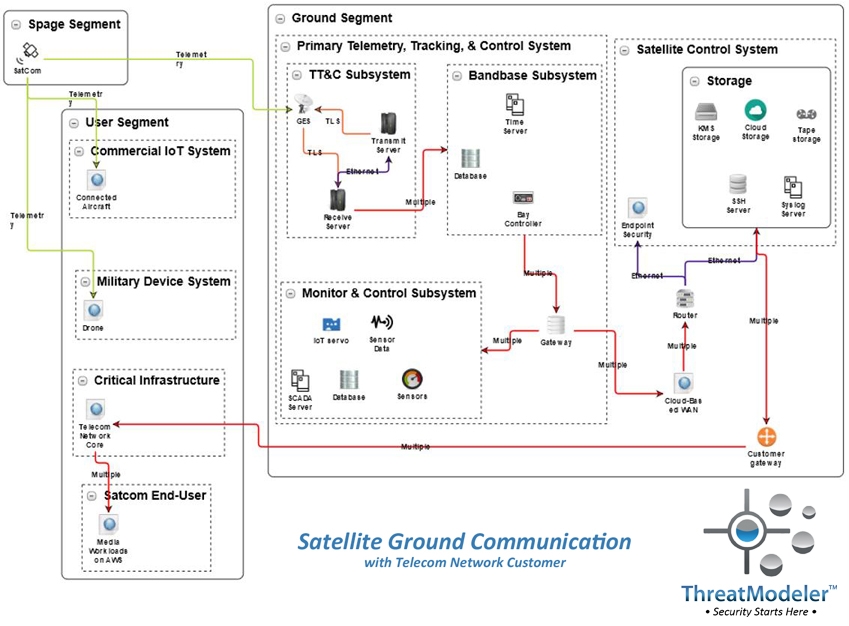
On a high-level, satellite systems are composed of three segments. The space segment includes the satellite, its payload, and the delivery vehicle. The user segment includes the telecom industry, an increasingly large array of connected devices and transportation vehicles, and a variety of data-dependent systems. The ground segment connects the space segment and the user segment and is the most vulnerable of the three.
Because of the crucial link provided by ground stations, they are subject to regulation by the Department of Defense. However, as most cybersecurity professionals know all too well, regulatory compliance does not equal adequate security.
Cyber Security is a Weak Spot for Satellite Systems
Demand for data transfer and global communications continues to grow. As a result, satellite systems are increasingly integrated with the Internet and other networks. Of course, with increased connectivity comes a growing attack surface – and increased risk for a cyber attack.
Satellite cybersecurity is hindered by “a multitude of weakness,” according to Major Stephen Bichler of the US Air Force. Introduced and overlooked during manufacture and construction, these weaknesses are “baked in” to satellite receivers, networks, and ground systems. According to Bichler, this means persistent cyber attacks are not only possible, they are probable.
Moreover, satellite ground systems are saturated with IoT devices and ICS to control massive antenna arrays and other equipment. The traditional “IT-OT” segmentation is now permeable, including connections from vendors and external communication systems. The IT-OT permeability and additional connectivity provide additional attack surface opportunities.[4]
Satellite Security is Important for Your Organization
So what’s the point? Most organizations have no direct control or responsibility for satellite cybersecurity. Why consider something external to the organization’s bailiwick?
Although there is considerable variance by industry vertical, overall about 73% of attackers are external to the organization.[5] Understanding where attackers originate provides insights into what their capabilities and motives. Without this understanding, defenders are working in the blind.
There are a variety of means, for instance, through which an attacker can send malicious traffic from one system to a connected system.[6] Once security has been bypassed, the attacker will be free to migrate laterally into any of the myriads of connected and downstream systems.
Satellite systems are a part of most organization’s extended cyber ecosystem. It is this same ecosystem from which nearly 3 out of 4 attackers arise. Understanding these attackers is necessary if organizations hope to mount a successful and effective end-to-end cyber defense. Today’s enterprises exist in a highly interconnected cyber ecosystem. Ignoring or overlooking attackers who may have the capability of infiltrating your organization starting from an infiltrated satellite ground station would be short-sighted.
Today’s organizations need to understand both the threats and the threat actors arising from their extended cyber ecosystem. The only way to gain this understanding, and the real-time situational visibility need to apply it, is through enterprise threat modeling.
Interested in learning more about threat modeling your extended cyber ecosystem? Click here to schedule a live demo with a ThreatModeler expert.
[1] Mercado, Jonathan Michael and Dale C Rowe. Cyber-Security, Aerospace, and Secure Satellite Communications – Evolving our Approach. American Society for Engineering Education: Washington DC. June 26, 2016.
[2] Dvorsky, George. “What would Happen if all our Satellites were Suddenly Destroyed?” Io9.com. Univision Communications: New York. June 4, 2015.
[3] Bichler, Stephen F. Mitigating Cyber Security Risk in Satellite Ground Systems. Maxwell Airforce Base: Alabama. April, 2015.
[4] Industrial Control System Threats. Dragos, Inc: Hanover. March 1, 2018.
[5] 2018 Date Breach Investigations Report, 11th Edition. Verizon, Inc: New York. April, 2018.
[6] Gibbs, Pierce. “Intrusion Detection Evasion Techniques and Case Studies.” SANS Institute: North Bethesda. January 17, 2017.