Password security is no joke. It’s a security measure for the point of entry to personally identifiable information (PII), and confidential, sensitive information. The first thing anyone should know when creating an account is to never share their password. Cybercriminals are notorious for enlisting social engineering tactics to try and convince targets to reveal sensitive data such as passwords. This article will talk about five password attack types that you should know about and ways to protect against them.
81% of Password-Related Hacks Involve Stolen or Weak Passwords
One of the biggest mistakes when creating passwords is using the easy-to-guess password like admin123, 123456 or some other easy to input variation. Warnings are all over the place, including the internet, yet people succumb to password attacks all the time. According to the 2017 Data Breach Investigations Report from Verizon, 81% of data breaches involving hackers had to do with stolen and/or weak passwords.
Organizations that are aware of the security threats posed by password attacks are making an extra effort to create stronger passwords for their employees. One of the main reasons why “strong passwords” can be a hassle is their inability to be used at all times. They are pretty much hard to remember, especially when trying to access through your mobile devices.
Avoid Using Passwords that Are Easy to Recreate by Hackers
Some of the most frequent data breaches have led to organizations of all sizes to educate their employees when it comes to securing their data, especially when creating passwords. More and more businesses owners are taking extra measures to guarantee that their information is stored safely. Some tips for ensuring your passwords are good enough include having a password that:
- Is at least 12 characters long
- Includes a mix of numbers, symbols, capital letters, and lower-case letters
- Avoids using dictionary words or combinations of dictionary words
Even though most people do their best to follow the employers’ password security rules, there are still many who would rather use an easy-to-remember password. Password attacks can lead to a data breach, which may cause irreparable damage to an organization. To protecting data and mitigate against potential threats, organizations will also set policies. Policy examples include:
- Changing your password after a certain duration, such as after 60, 90 and 120 days
- Never writing down or emailing your password
Top 5 Password Attack Types
To help you understand just how hackers get access to your passwords, and how you can protect them, we’ve put together a list of the most popular password attack types used in the digital world as well as ways to secure your network and sensitive information. To that end, here’s a briefing of the most commonly used types of attacks.
Phishing
The most common way for hackers to obtain user’s passwords is by asking. Sending phishing emails leads the unwary reader to a falsified log in page with content related to the service the hacker wants to which the s/he wants to gain access. One example is a request to update your password, in an ironic twist. The website then scans their password and the hacker is free to use it and obtain any additional user data. To protect against phishing attacks:
Be wary of suspicious emails from unrecognized senders. Some ways to recognize phishing emails include:
- Unrecognized senders
- Typos in the email body
- Suspicious destination links (right click on the link to see the destination)
The below screen shot is an example of a phishing email:
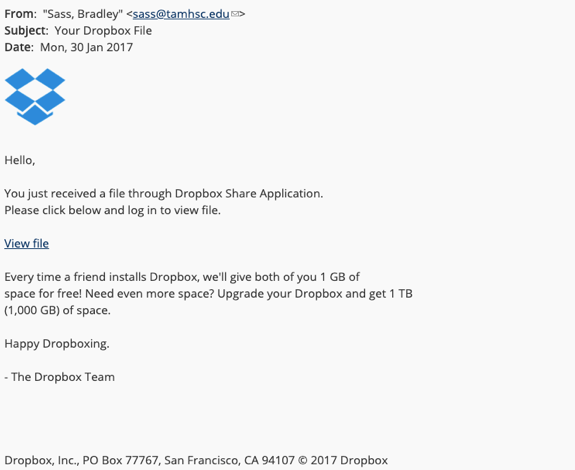
Dictionary Attack
Known as the dictionary attack, this is the most common type of password attack that uses a program featuring most user-friendly passwords. This method of cyberattack is similar to the brute force attack but in a less complex way. They are both characterized by cyberattackers blasting a script with guesses on possible accurate passwords.
Words put together such as date of birth and your dog’s name will not protect your account against the dictionary attack. This type of password attack can predict such passwords and hackers will access your system faster and more easily than you think.
Learn more about How to Secure your Organization from Dictionary Attacks and Brute Force Attacks here.
Brute Force Attack
The brute force attack is very similar to dictionary attack, but uses a more complex approach. With this type of attack, a hacker uses a program or software to log in with probable password combinations. If you think about it, having an easy-to-guess password is a common mistake, and hackers should be able to guess this very easily.
With similar features to the dictionary attack, the brute force attack is considered more sophisticated. Rather than using software with a common list of words, brute force attacks can uncover non-dictionary terms, such as alphanumeric combinations. This means passwords that include sequences such as “123” or “abc” are in danger of a brute force attack. Yet, this type of attack is usually reinforced by further computing power to reduce hacking time by allocating more digital resources to the task.
Keylogger Attack
In this type of password attack, a hacker uses a program to keep track of the trajectory of all of the user’s keystrokes. Once this is done, the hacker reviews everything the user has typed, documented by the program, and . The main difference between a keylogger attack and brute force or dictionary attack is that the key-logging program used is malware that must be installed onto the user’s device. Therefore, there is a degree of social engineering taking place.
The target generally is not aware that they are being monitored. In addition to passwords, a hacker using the keylogger method of attack can obtain any number of private data, including banking information, social security numbers, driver’s license numbers. The sky is the limit.
Creating stronger passwords doesn’t guarantee offering much shelter this type of attacks, which is why multi-factor authentication (MFA) is now a must-have for all enterprises. Other methods of protection include installing firewalls, keeping your applications updated (for patches and bug fixes) and updating your passwords.
Spidering
Sophisticated hackers have recognized that passwords used by professionals in a business setting are created with words that are associated with the company itself. Professional hackers have systematized this practice through spidering, the application of an automated process that crawls websites for words or phrases that may be used for passwords. The tech is just like the ones used by search engines to categorize keywords, and enables hackers to gather and organize lists of relevant passwords.
Securing Passwords in the Cloud
With the rise of organizations moving to the cloud, it is imperative that business owners set security controls to store passwords early in the cloud development lifecycle (CDLC). Like we stated previously, remembering passwords can be irritating. Most people usually take the stress-free path utilizing the same passwords as other accounts or just using easy-to-guess passwords. Finding the right solution to successfully secure your cloud infrastructure early in the CDLC is the best way to protect your password correctly.
ThreatModeler to Secure Your Cloud in the CDLC
ThreatModeler is an automated threat modeling solution that strengthens an enterprise’s cloud development lifecycle (CDLC) by identifying, predicting and providing threat mitigation requirements across all applications and devices in the operational IT stack. Security teams are empowered to make proactive decisions by providing them with holistic views and data analytics of the attack surface, enabling enterprises to minimize overall risk.
ThreatModeler can help DevOps teams to identify, prioritize and mitigate password-related threats by mapping them out on your attack surface (visually) and listing them as IT issues that need to be resolved. To learn more about how your organization can identify security threats during the SDLC for faster, smarter, more secure application production, request a demo of the ThreatModeler platform.
ThreatModeler at RSA Conference
For three decades, RSA Conference has provided a forum to discuss important news, information and issues related to cybersecurity. Join Team ThreatModeler at the RSA Conference 2020, where we are hosting a sponsored Booth #2068. Visit our Events page to learn more and to schedule a meeting in advance with one of our team members.





