Penetration testing involves teams who conduct technical and process hacks. Web application penetration testing, for example, involves the enlistment of hackers who see how and where they can accomplish an infiltration. Within the software development lifecycle (SDLC), penetration testing is vital to discover vulnerabilities and gives teams across an organization an accurate measurement of an organization’s security posture. The cybersecurity posture of an organization refers to its overall strength in securing against outside threats to attack surface vulnerabilities.
Penetration testers will try to break into an application – whether in testing or production. Once completed, penetration testing provides the information and documentation to prove to regulatory bodies that an enterprise is taking steps to achieve a secure environment. Every pen test is different based on the individuals performing it, their approaches, mindsets, capabilities plus tools involved.
Why Are Penetration Tests Important?
Penetration tests not only send a message that an organization is doing what they can to ensure the security of their private and confidential data. It also helps DevSecOps teams to better understand the dynamic of hacks, including how bad actors can compromise an IT ecosystem’s attack surface.
Pen testing services help security teams to identify areas for improvement and prioritize threat mitigation strategies. Penetration testing can yield surprising results and can help organizations to better understand the different attack vectors that can compromise data. For example, within a web application security testing exercise, pen testers will find as many ways to attack the various parts of the application. This will provide SDLC teams with a vulnerability perspective that is more about the attacker’s point-of-view – think like a hacker, if you will.
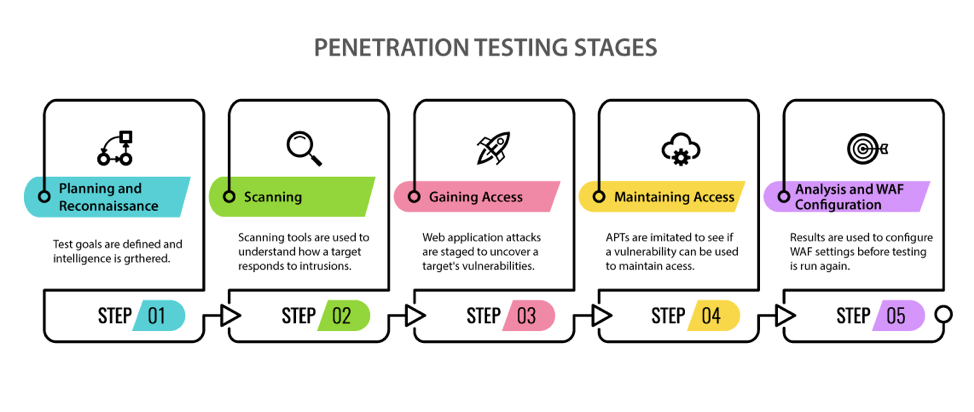
Diagram Courtesy of www.eccouncil.org
What are the Different Types of Penetration Testing?
There are three major types of penetration testing that occurs: black, white or gray. Your decision on which approach will depend on the amount of information you are willing to disclose to hackers about your environment.
Black Box Testing – with functional Black Box Testing, no implementation knowledge is necessary beforehand. Therefore, hackers infiltrate a system without knowing the design or implementation structure. Black box testing is done mostly by software testers.
White Box Testing – in structural White Box Testing, implementation understanding is necessary. White Box Testing occurs with knowledge about the design or implementation structure of an application or system beforehand. White box testing is accomplished mostly by software developers. White Box Testing is generally the most time consuming of all penetration testing activities.
Gray Box Testing – a combination of Black Box and White Box Testing, Gray Box Testing will yield some knowledge and understanding of the internal structure of a system, including its design and implementation structure, to a limited extent. Gray Box Testing is generally done from the end user’s perspective. It is not necessarily from the point-of-view of a programmer.
What Does a Real Penetration Test Look Like?
Penetration testing is expensive, despite the short amount of time it takes to complete it. An organization can only do it for so long before it gets expensive. Therefore, it is important for a company to scope the penetration testing project and define targets. However, pen testing paints a pretty clear picture if we filled our requirements correctly.
A 1-2 day engagement can be costly. However, the more in-depth the penetration testing, the more time you spend infiltrating the system, the more your security teams can find out what an application looks like under the hood. This includes the technology being used, the flow of the application, the attack points. The only improvement is you have a known quantity, you understand the pen test team and the capabilities they have.
Penetration testers should be able to identify vulnerabilities for which DevSecOps teams may not have accounted. The hackers involved in application penetration testing, for instance, will be able to provide training and feedback to developers. This way, DevSecOps won’t make the same mistakes again.
Penetration testers will generate comprehensive reports that speak about the overall threat landscape, including vulnerabilities. Depending on the boundaries you set, hackers who conduct penetration tests apply advanced techniques and can be very invasive to find system vulnerabilities. Penetration testing should be more of a validation of how correct your organization’s approach to security is in order to find out ways to improve.
How Threat Modeling Can Help the Security Penetration Testing Process
Pen testing is akin to conducting reconnaissance on the target. Did you think about everything? Are your security controls effective? If you bring threat modeling in, there will be a better focus on the discovery of potential threats. Threat modeling will be done first.
If you are doing pen testing you can use the threat model as a guide. With the findings of your pen testing, you can go in and ask the question: did you find areas of vulnerability that you did not find when you created the threat model? ThreatModeler enables you to put threats not previously identified to add it to the requirements. Therefore, ThreatModeler can add to pen test efficiency, adding more value for the dollars.
ThreatModeler is an automated platform that enables authorized users to build enterprise-wide threat models on which they can collaborate to prioritize security controls. Learn more about how ThreatModeler – with its scalability and integration with AWS and Azure cloud – can help your organization to improve its security posture, book a demo to speak to a ThreatModeler expert today.





