Internet of Things (IoT) solutions are trending at an explosive rate, especially in the business world. With an exponential increase in devices that connect to the internet, businesses see huge benefits for communications and productivity. However, this can also leave systems and networks exposed to a growing number of new cyber threats. To help strengthen IoT application security, let’s discuss an IoT threat modeling example that can control the expansion of organizational attack surfaces.
Evolving Internet of Things Security Threats
A recent international study sponsored by the US Chamber of Commerce indicates that in just two years, as many as 85% of organizations will utilize IoT to add value to their operations.[1] By 2020, analysts predict the number of IoT devices globally to be between 20.4 and 60 billion.[2] Interconnected sensors, tags, devices, communication networks, and data are everywhere, adding value to organizations and convenience for consumers. However, without proper IoT cybersecurity, the rapid speed of adoption will leave organizations open to attacks.
IoT Threat Modeling Example: Virgin Atlantic
Consider Virgin Atlantic’s new fleet of Boeing 787 aircraft. Every single component of the aircraft is IoT enabled. According to David Bulman, Virgin Atlantic’s CIO, the value gained by the nearly 1/3 terabyte of data generated by each IoT aircraft during each flight is exceptionally high.[3] For example, point out Bulman, an engine with suboptimal in-flight operations is sending a constant stream of data to the ground staff. When the aircraft lands, engineers will be standing by, ready to fix whatever is wrong.
However, that level of connectivity in even a single aircraft – engines to flaps to landing gear and anything else that is connected to the 787 – represents a huge attack surface. Unless the entire IoT ecosystem is properly secured through proper IoT threat modeling, the expanded attack surface is a “playground” of opportunities for anyone wishing to compromise the safety and security of the flight.
Architectural Diagram of an Iot-Enabled Aircraft Ecosystem
Because IoT is an ecosystem, not just embedded devices, IoT threat modeling is necessary to analyze all security vulnerabilities across both data and physically controlled systems. Consider an architectural diagram of an IoT-enabled aircraft ecosystem in which the aircraft has just four connected devices:
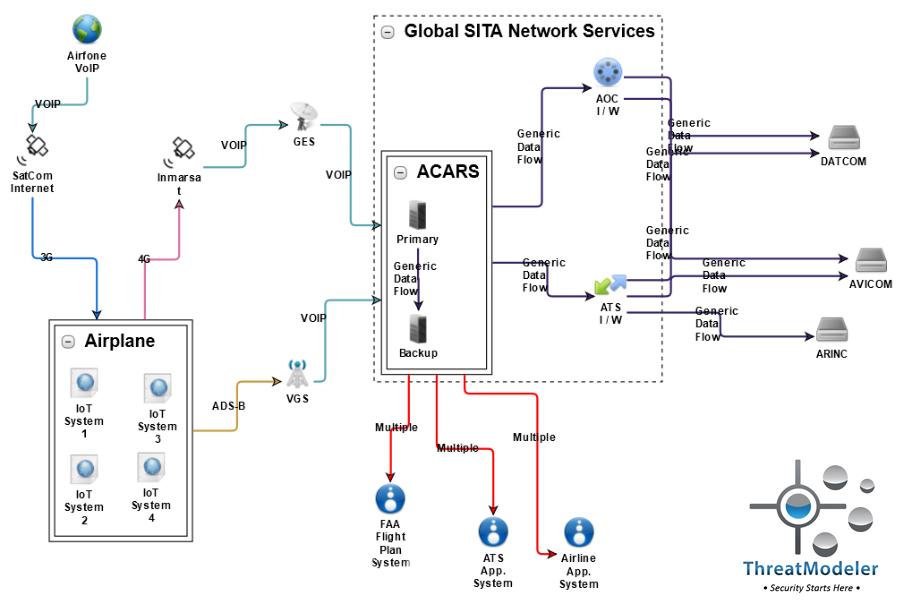
From this diagram, an IoT threat modeling example can be created. This excludes threats caused by the aircraft and including 57 potential threats. The aircraft without IoT devices adds only three more threats. However, the four IoT systems added to the aircraft – which could be for engines, flaps, landing gear, and the galley stove – add an incredible 218 threats to the attack surface. Without IoT threat modeling, the attack surface of a single IoT-immersed Boeing 787’s undoubtedly rivals that of any Fortune 500 enterprise’s entire IT system.
Learn more: Threat Modeling 101: How Can It Help My Business?
Why IoT Threat Modeling Matters for IoT Security
It is well known that IoT devices are generally lagging in terms of network and information security. This is either due to:
- Lax manufacturing standards
- Devices that do not have the computational horsepower or storage space to be secured
Even if one device is properly secured, unsecured devices can still exist in the organization’s ecosystem. This entirely bypasses the scope and reach of IT security teams and opening up entire networks to data breaches. Architecturally-based IoT threat modeling can reveal these IT security bypasses.
Without specific IoT security, an organization can easily lose control of their IoT ecosystem attack surface. Organizations can, for example, dictate and enforce policies that no personal smart devices are brought into the work environment.
All that care and monitoring can be thrown out the window if one employee logs into the IT system while working from home. While it is possible to prevent employees from bringing smart devices into the work environment, it would be difficult to manage visitors with IoT devices from entering the building. Securing the IoT ecosystem simply cannot be done by policy mandates.
IoT Regulations and Standards Also Fall Short
Some – including the US Chamber of Commerce[4] – are working to implement an international security standard for the IoT.[5] Standards and regulations are necessary and inevitable – however, their implementation is glacial compared to the speed at which the threat landscape evolves for commercial and industrial IoT.
The newly formed “Trusted IoT Alliance” proposes an implementation of blockchain security to secure the IoT.[6] Their goal is to create a “trusted IoT ecosystem with improved security and trust protocols.” However, blockchain is not a preventative security technology. It is a decentralized, distributed ledger. The Alliance’s proposal is to use blockchain – not as a means of shrinking the attack surface, but merely to create a tamper-resistant event log.
While this proposal does mitigate the risk of system logs being modified by attackers,[7] it can do nothing to prevent attacks or stop attacks in progress. A tamper-resistant security log is ideal for forensic purposes. But it has the same weaknesses as all security logs:
- A system event needs to trigger the logging process
- Security must then sort out the significant events from false-positive “noise.”
Security logs are of little help to the 143 million US adults whose critical information was loosed in the Equifax data breach. Nor will it comfort the crew and passengers of an IoT-immersed aircraft compromised by cyber-terrorists.
Architectural IoT Threat Modeling Example for IoT Threats
A recent McKinsey survey of enterprise security experts indicated that securing IoT is a top priority for 75% of organizations. Interestingly, though, only 16% of organizations are ready to implement IoT security.[8] The reason for the significant gap is simple – decision makers do not understand their IoT threats nor what to do about them.
An architecturally-based IoT threat modeling example provides the answers these decision makers need. By examining the IoT aircraft system threat model diagram, for example, the numerically greatest source of cyber threats to the aircraft – excluding consideration of the IoT systems for the moment – is the Airfone VOIP / SatComm Internet system. In this subsystem, the threat model identified 24 of the 60 total non-IoT threats. Examination of these threats, though, indicates that they primarily target the endpoint users – those individuals using their cell phone or laptops during a flight. For the safety of the aircraft, then, such threats are a low priority.
ThreatModeler’s architecturally-based IoT threat modeling can identify specific threats throughout the IoT ecosystem and how such threats impact the larger system. Considering the IoT aircraft system threat model again, the threats causing the most significant risk to the physical aircraft come from the embedded IoT systems. These systems directly are used to directly monitor and control critical aspects of the physical aircraft system. The specific threats identified from architecturally-based IoT threat modeling include:
- Action Spoofing
- Alteration of installed BIOS
- Device Hijack
- Denial of Service
- Faking the Data Source
- Insecure WiFi Channel
- Manipulating Writable Configuration Files
- Targeted Malware
- WiFi Jamming
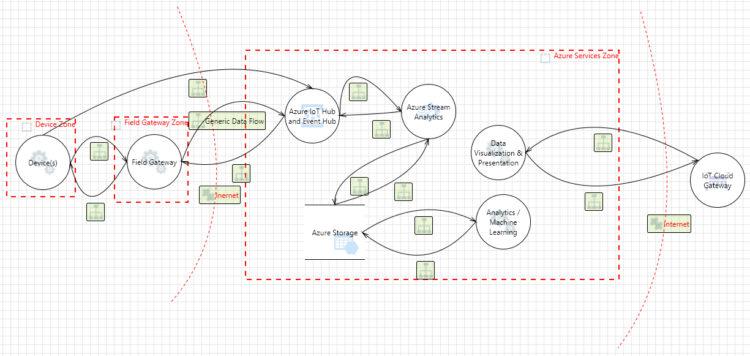
Insufficient Engineering-Based IoT Threat Modeling Example
Engineering-based threat modeling driven by data flow diagrams (DFD) –as exemplified by Microsoft’s Threat Modeling Tool (TMT) – is inadequate to help decision makers understand and mitigate IoT-related threats.
The above IoT threat modeling DFD was created per Microsoft’s example[9] with TMT using their newest Azure and IoT template. It identified 46 potential categorical threats, most of which revolve around the compromise of sensitive data. Information of such a generalized nature is virtually useless to helping organizations secure their IoT ecosystem – unless, of course, the organization is convinced that terrorists are interested in how many operational hours have transpired since the engine’s last scheduled maintenance.
If the airline’s decision makers depend on the outputs of Microsoft’s TMT threat model, they might conclude that the embedded devices on their 787 fleet do not come with serious threats to the safety of their crew and passengers. However, even the recent demonstrations of attackers’ ability to remotely compromise an IoT-immersed automobile[10] should serve as a clear indication that attackers could compromise their aircraft.
Engineering-based IoT threat modeling, whether built upon DFDs or checklists, cannot provide the specific analytical insights as can be gained from architecturally based IoT threat modeling for one simple reason: Threat modeling a cyber-physical ecosystem is beyond their scope. DFDs and checklists are designed only to identify potential categorical threats or “obvious” threats associated with single applications operating in isolation. Such a limited scope, though, is a far cry from the reality of an IoT ecosystem.
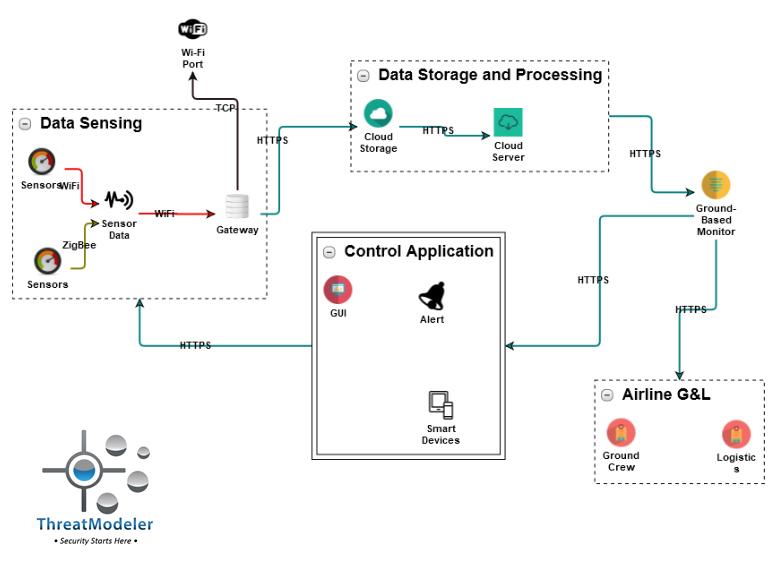
IoT Threat Modeling with ThreatModeler
However, by considering just one of the IoT systems included in the IoT aircraft threat model, the powerful outputs of ThreatModeler’s IoT threat modeling example can be seen. The architecturally-based process flow diagram, for IoT System 1, shown below and included as an architectural component in the “big picture” threat model, identified 75 potential threats.
Understanding that the above diagram is not a DFD, but an architecturally-based where do you see specific threats directly to the aircraft that could impact the lives and safety of those aboard?
To learn more about how ThreatModeler™ can help your organization build a scalable threat modeling process, book a demo to speak to a ThreatModeler expert today.
[1] Brown, Megan L, et.al. “The IoT Revolution and our Digital Security: Principles for IoT Security.” Wiley Rein, LLP. U.S. Chamber of Commerce: Washington D.C. 2017.
[2] Baker, Sarah. “Cybersecurity and the Internet of Things.” Applied Cybersecurity Strategy for Managers. Essec Business School: Clergy, France. July 1, 2016.
[3] Simmons, Clare. “How the Internet of Things is Transforming Business.” Global Intelligence for the CIO. Fujitsu: Minato, Tokyo, Japan. January 2015.
[4] Goovaerts, Diana. “US Chamber of Commerce calls for international IoT security standards.” Mobile World Live. GSM Association: London. September 19, 2017.
[5] “Why is an IoT Security Standard Needed.” IoT.Business.News: Le Cannet, France. September 19, 2017.
[6] Osborn, Charlie. “New alliance advocates the blockchain to improve IoT security, trust.” ZD Net. CBS Interactive: San Francisco. September 19, 2017.
[7] Cohen, Roi. “CyberArk Labs: Can Incident Response and Audit Teams Always Trust Windows Security Event Logs?” Cyber Ark. CyberArk Software Ltd: Newton. May 19, 2016.
[8] Bauer, Harald, et. al. “Six ways CEOs can Promote Cybersecurity in the IoT Age.” McKinsey & Company Internet of Things. McKinsey & Company: New York. August 2017.
[9] Diogenes, Yuri & Dominic Betts. “Internet of Things security architecture.” Microsoft Azure. Microsoft: Redmond. July 3, 2017.
[10] Greenburg, Andy. “The FBI Warns That Car Hacking Is a Real Risk.” Wired. Condé Nast: New York. March 17, 2016.





