A flat tire on your morning commute can leave you stranded for hours, and a broken cog in the factory can wreak havoc on the entire assembly line. The same is true for DevOps implementation. It is virtually impossible to realize the promised benefits of DevOps from a poor or immature implementation. However, ThreatModeler DevOps Edition can improve your DevOps implementation in seven ways.
DevOps is more than a buzzword or cultural concept. It has fast become a “must-have” for any organization serious about profitably producing secure software that delights customers. The number of organizations with active DevOps teams has increased 69% over the last three years, and not surprisingly.
The rapidly evolving technological landscape impacts every organization. IT systems once fulfilled the primary purpose of supporting the back office functions. Now, IT increasingly supports a dynamic and crucial exchange through which organizations interact with each of their external and internal key stakeholders.
Banks, for example, can no longer expect clients only to do business on-premises during regular banking hours when their competitors offer anywhere-24/7 access to the same functions through their web applications. For organizations across every sector, connectivity is no longer a matter of competitive advantage. It is a matter of marketplace relevance.
7 Ways to Improve your DevOps Implementation
This market pressure naturally pushes the demand for faster deployment of high-quality digital products in response to customer feedback. Increasingly organizations are discovering that integrating development and operations teams and automating their workflow with proper tooling provides significant increases in production throughput and quality.
DevOps creates a production environment through which organizations can – theoretically at least – move toward a continuous deployment model through iterative cycles of development sprint, testing, and release, client feedback, integrating feedback into the next development sprint
A significant shortfall with this model – one which impacts the entire DevOps process and its ability to deliver promised benefits – is that security is an end-of-process activity.
Nearly everyone agrees that security must be an integral part of a successful DevOps process.[2] However, in most organizations implementing DevOps, security is given far lower priority relative to speed and innovation. While existing DevOps practices can satisfy the short-term business imperative to get functional products to market, competitively successful organizations need to take a long-term view when it comes to product quality and customer delight.
Equifax’s recently publicized Experian security breach well illustrates how an “oversight” in security can have a material impact on an organization’s bottom line. Better and earlier integration of security will not only improve your DevOps implementation overall but will mitigate long-term concerns for customer and stakeholder satisfaction.
To that end, enterprise threat modeling with ThreatModeler™ yields seven ways to improve your DevOps implementation, thereby increasing productivity, customer satisfaction, profitability, and market share. This is the first part in a series that will examine ways to improve your DevOps implementation, which will yield increased benefits throughout the organization, through enterprise threat modeling.
1. Integrate Security Early in the DevOps Process
Enterprise threat modeling with ThreatModeler enables organizations to fully “left-shift” security to the project architectural whiteboarding stage.
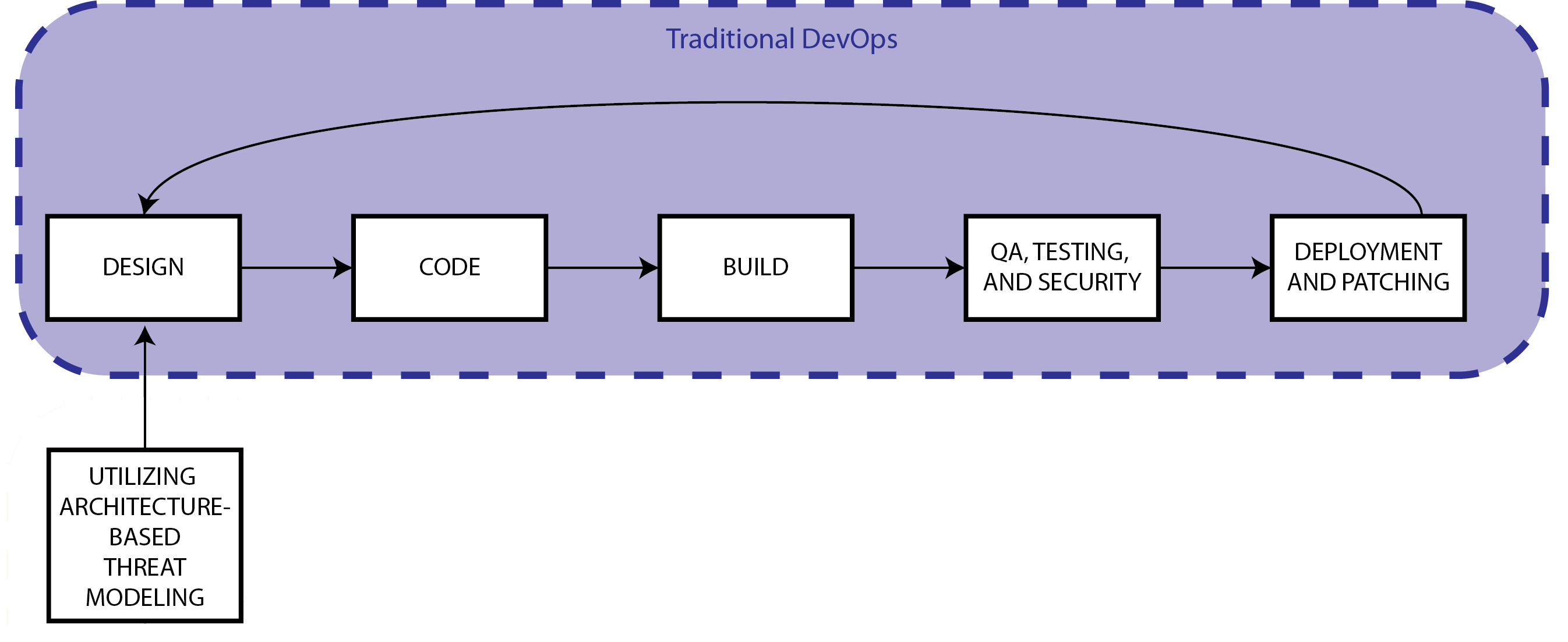
Creating architecturally-based process flow diagrams starts the process by which you can improve your DevOps implementation. When architects whiteboard their projects directly on the ThreatModeler diagramming canvas, they can accomplish two tasks simultaneously: First, they efficiently create consistent architectural diagrams from which DevOps teams can get to work and which can be easily shared with all stakeholders. Second – and very importantly – they also automatically end up creating detailed threat models with actionable outputs which the DevOps team can act on immediately, ensuring that security is “baked in” from the start.
Creating a process flow diagram in ThreatModeler is 3-step “drag-and-drop” easy:
- Start by locating the needed architectural components in the toolbox and drag them onto the canvas.
- Once all the project’s features, use-cases, and/or components are represented, the next step is to add the appropriate communication protocols.
- Finally, provide additional, project-specific properties to the placed components.
See how quickly and easily anyone can create a process flow diagram and automatically produce a detailed threat model that identifies 77 potential threats for this online banking application.
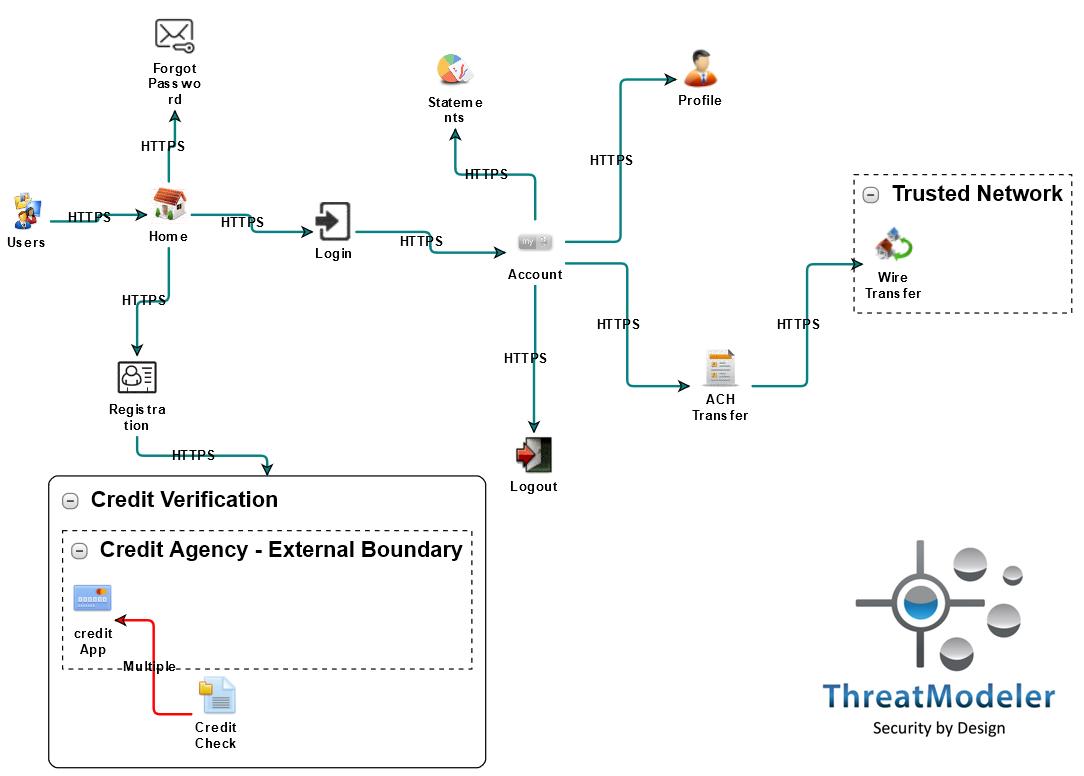
To learn more about how ThreatModeler can improve your DevOps Implementation, click here to schedule a live demo today!
[1] Forsgren, Nicole. “2017 State of DevOps Report.” DevOps Research and Assessment (DORA). Puppet: Portland. 2017.
[2] “Application Security and DevOps: What is the true state of security in DevOps?” Hewlett-Packard Enterprise Development LP: Palo Alto. October 2016.





