Many security professionals are die-hard Microsoft Threat Modeling Tool (TMT) fans. After all, it is free, and there are no limits from Microsoft on the number of users or threat models you are allowed to make. Moreover, perhaps most importantly – they have been using TMT since they were first introduced to threat modeling. TMT was initially designed for the slow-paced, documentation-heavy waterfall production environment popular in the early 2000s. However, a lot has changed as the DevOps culture-change has swept through the IT industry. Despite the “free” access to TMT provided by Microsoft, organizations would do well to consider whether or not they are getting the threat modeling outputs needed to meet the increasingly challenging cybersecurity[1] issues of today’s fast-paced DevOps environments.
Case in point: Following TMT’s lead, every threat modeling tool on the market can provide a list of potential threats for an application in isolation. However, applications today rarely operate in isolation. If the purpose of threat modeling is to help defenders see their applications and IT environment from the perspective of probable attackers, then it makes no sense to analyze an application as if it is the only application running on a system. Attackers see applications in a highly interactive cyber ecosystem in which applications interact with one another, there are a variety of shared components and 3rd party systems, not to mention an ever expanding array of cloud based deployment environments and in increasing plethora of IoT and mobile devices connecting to and interacting with a variety of IT systems.
One simple example of IoT devices connecting to an organization’s cyber environment is a remote employee’s smart home. The proliferation of IoT devices in homes – despite their well-known weak security – should be a cause for organizational security teams and CISOs.[2] With the right equipment – inexpensively available at many electronics stores, a broad range of smart home devices can be successfully converted into attacker “portals” to the home’s WiFi system. From there, even an attacker with only moderate skills can navigate through the remote employee’s home network and, with only a small amount of effort, waltz into the organization’s IT system as a credentialed user. At that point you can forget about trust boundaries – the attacker is already inside the gates!
Smart homes and other so-called Shadow IT are here to stay.[3] Furthermore, they materially contribute to an organization’s overall attack surface. Therefore, we created a smart home threat model in both TMT and ThreatModeler so that security professionals and others can decide for themselves if their choice of tool is giving them the threat modeling outputs needed to face their evolving cybersecurity challenges.
Threat Modeling a Smart Home with TMT
The smart home threat model was created in TMT, based on the following data flow diagram:
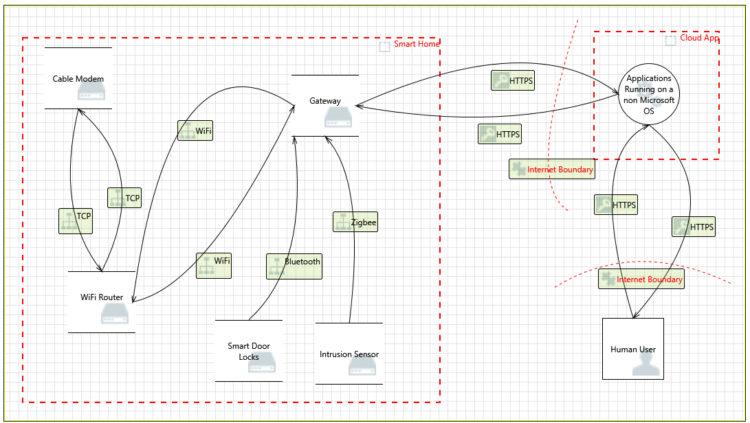
It took an independent security expert about an hour to create this data flow diagram in TMT. The threat report generated by TMT identified 36 threats. A sample of the threat report demonstrates the outputs TMT produces:
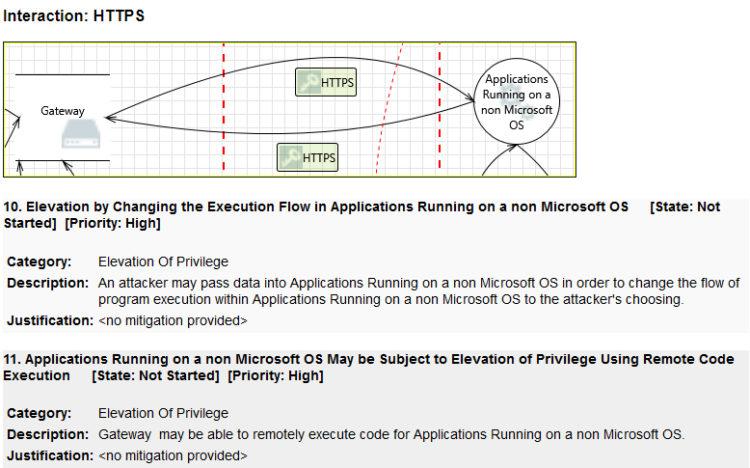
While the above may communicate well enough to security subject matter experts, it is doubtful that these are the threat modeling outputs needed by the DevOps team that will be required to implement the appropriate mitigating controls. For the DevOps team to implement the mitigating controls, security will need to communicate exactly what the source of the identified threats are, the specific threats to be mitigated, and the particular mitigating controls. Security will also need to provide the relevant test cases to the QA team so the implemented controls may be verified. In the old waterfall production environment, where a project might take six months or longer to create and document fully, security could keep up with the communication demands. Timely communicating the threat modeling outputs needed to a sprinting agile DevOps team using this same process, however, will be an impossibility. By the time security completes the threat model, the DevOps team will have completed two other projects, and the threat modeled project will be getting a security exemption so it can get deployed.
Get the Threat Modeling Outputs Needed
The same security expert created an equivalent smart home threat model with ThreatModeler™ based on the following process flow diagram:
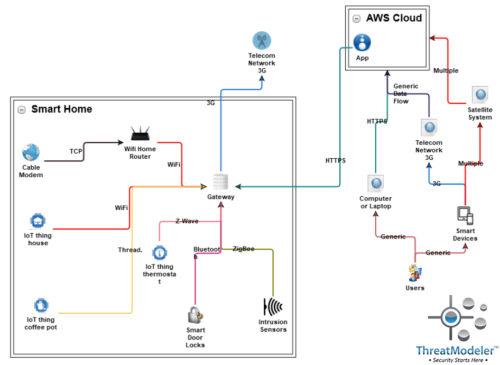
It took the security expert about fifteen minutes to create this diagram. However, included in that time was the generation of 142 specific threat modeling outputs needed by the DevOps team – including 46 relevant mitigating controls and 39 verifying test cases. A sample of ThreatModeler’s automated output is included below:
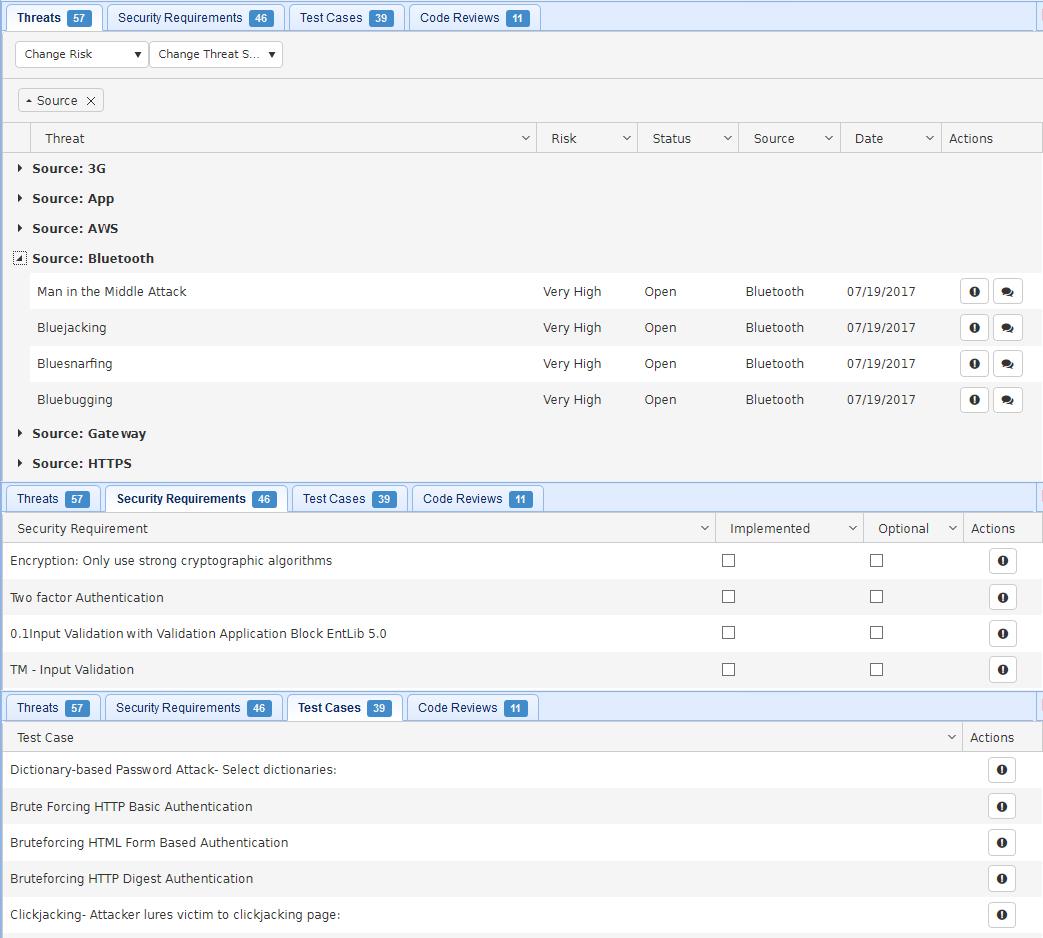
DevOps and QA teams can click on the Action buttons for each security requirement or test case to get a detailed description of how to implement or test the selected item. All stakeholders can click the threats Action button to get a detailed description of the specific threat. Furthermore, threats can be sorted by source – as shown – or by any combination or order of the column headings (threat, risk, status, and so forth).
Compared to independent side-by-side trials by a security subject matter expert, ThreatModeler allows for the faster creation of visual diagrams, greater threat modeling automation, and generation of specific outputs the DevOps team can put into action during their initial sprint. If these are the efficiencies and threat modeling outputs needed by your security and DevOps teams, you may want to consider that ThreatModeler is the best tool for your organization.
To learn more how you can get the efficiencies and threat modeling outputs needed, click here and schedule a demo.
[1] Oltsik, Jon. “Cybersecurity Operations More Difficult than it was 2 Years Ago.” CSO. IDG: Boston. July 17, 2017.
[2] Bonderude, David. “IoT Warning: FBI Says More Devices Equal Bigger Attack Surface.” Security Intelligence. IBM: Armonk. September 15, 2015.
[3] Rockwell, Mark. “IoT Cybersecurity a Hot Topic of White House Advisor.” FWC. 1105 Media, Inc: McLean. July 11, 2017.





