By Nikunj Nagalia, VP of Solutions Architecture
Amidst the tumultuous year of 2023, 23andMe found itself ensnared in a harrowing breach, compromising the sanctity of its fortified defenses and laying bare the personal data of nearly 7 million users. This cyber siege breached the ramparts of users’ privacy, exposing a treasure trove of sensitive Personal Health Information (PHI) like DNA profiles, ancestral lineage, and familial trees, alongside the Personally Identifiable Information (PII) of names, usernames, and addresses. Executed with precision, the attackers wielded a credential stuffing attack, exploiting credentials of approximately 14,000 users to launch an unrelenting onslaught of login attempts, masquerading as legitimate users in their relentless quest for data plunder.
In the aftermath of the breach, a critical directive was issued to all users:
- Reinforce passwords with complexity and diversity.
- Activate Multi-Factor Authentication (MFA) for an additional layer of security.
- Commit to bolstering defenses through heightened monitoring, robust logging mechanisms, and strategic reinforcements.
As we delve into the depths of this breach, several pressing questions demand answers:
- Given the highly sensitive nature of 23andMe’s data, why did regulatory oversight seemingly fail to safeguard it?
- In light of the critical imperative to protect such sensitive data, what preventative measures could have thwarted this breach and shielded the information from exposure?
It’s no secret that users often resort to password reuse for B2C services, not out of negligence, but for sheer convenience. However, exploiting this human tendency, attackers capitalize on compiling databases of commonly used usernames and passwords, leveraging them across various platforms. This prompts a critical inquiry:
- Despite the awareness that attackers possess such credential databases, why was all user information readily accessible upon login?
- Moreover, what monitoring mechanisms were implemented to detect and report suspicious login activity?
To dissect these questions and offer a strategic solution to this pressing issue, let’s delve into the following factors:
- The breached data directly impacts 23andMe’s core operations, with ancestry DNA assessments forming the crux of its B2C revenue stream.
- Operating globally, 23andMe’s services transcend geographic boundaries, magnifying the repercussions of any breach on its extensive user base.
- The breached data interconnects, forming a complex web of interrelated DNA profiles. Thus, a breach affecting one user has the potential to compromise the security of others, even those not directly targeted.
- The identification of a singular attacker group hints at a systematic data extraction method, potentially facilitated through programmatic means like APIs.
- 23andMe’s migration to AWS underscores its reliance on cloud infrastructure for data storage and processing.
Addressing the breach demands a multifaceted approach encompassing not only technical fortifications but also strategic realignment and proactive risk mitigation measures. Now, let’s pose some critical inquiries:
- Did the company’s leadership overlook the crucial task of defining the asset—user data?
- If identified, was a specific value assigned to this asset, reflecting its importance and sensitivity?
- Was there a clear strategy delineated for safeguarding data privacy and protection?
- How effectively did the company translate its overarching business strategy into actionable technical requirements and security policies?
Now, let’s delve into a simplified architectural overview:
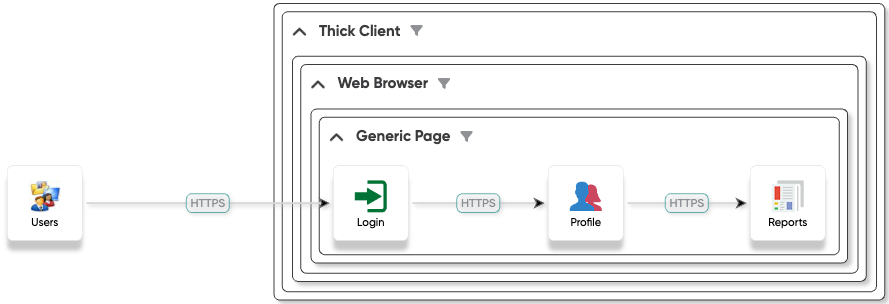
The breach occurred through the exploitation of leaked credentials, enabling the attacker to assume a legitimate user’s identity and gain access to their personal report. While shifting responsibility to individual users may seem plausible, it’s inadequate for an organization reliant on safeguarding data. A fundamental shift in strategy is imperative, demanding a reevaluation of existing approaches.
Crafting a comprehensive strategy entails:
- Identifying and valuing crucial assets, assigning a monetary value to revenue-generating or supporting entities.
- Implementing a layered defense strategy to understand potential threats, including known attacker groups and insider threats, and mapping potential attack paths.
- Adhering to industry standards and regulatory requirements as benchmarks for implementing minimum security measures.
- Transitioning from a traditional Software Development Life Cycle (SDLC) to a Secure Software Development Life Cycle (SSDLC), integrating proactive measures like threat modeling and reactive measures like robust logging and monitoring systems.
Embracing these components enables organizations to construct a robust defense posture capable of mitigating a wide range of cyber threats. The earlier diagram serves as a basic threat model, offering insights into vulnerabilities such as sensitive data exposure through credential stuffing attacks.
As additional context, the 23andMe cyberattack in 2023 served as a wake-up call, highlighting the vulnerabilities inherent in modern digital ecosystems and underscoring the critical importance of proactive cybersecurity measures, such as threat modeling, in safeguarding sensitive user data.
Credits:
- Data Breach at 23andMe Affects 6.9 Million Profiles, Company Says
- Hackers got nearly 7 million people’s data from 23andMe. The firm blamed users in ‘very dumb’ move
###





