Enterprise DevSecOps: the end-to-end infusion of security’s perspective within the existing enterprise DevOps environment. It is easy to talk about, and easy enough to write manifestos about it. However, practical implementation is far more challenging. To date, organizations have realized some success in implementing two of the three pillars upon which long-term business strategy is established.
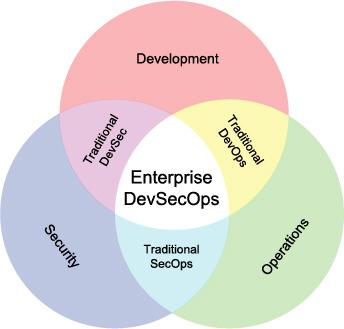
Integrating Agile development with operations produced a culture of collaboration, integration, and automation within IT. Traditional DevOps improves communication among all stakeholders while improving product quality and throughput.
The union of security and operations – SecOps – focuses on processes, tools, and shared accountability to ensure that the organization’s commitment to performance and uptime does sacrifice security or increase organizational risk. SecOps requires that both functions stay engaged in the process of secure performance and uptime, providing visibility to needed changes and the potential business and technological impact of those changes.
DevSec – the combination of development and security – is all about end-to-end security throughout the development process. In other words, the goal of DevSec is not to transform developers into security professionals, but to bring the concerns of security to the forefront of developers as they create code.
When DevSec, SecOps, and DevOps are united as DevSecOps, the traditional tension that exists between Agile developers, security, and operations is dispensed. All stakeholders, from those working through the various subject matter details to executives managing the overall business and technological strategies, are better aligned to more efficiently fulfill the business mandates.
Interestingly, the tools and processes needed to implement enterprise DevSecOps are the same as required for rolling out an enterprise threat modeling process.
Enterprise DevSecOps is an End-to-End Security Process
Combining DevSec’s focus on end-to-end security with SecOps’ focus on processes and tools that ensure the organization’s IT system is up and running without sacrificing security produces a focus on processes and tools that enable end-to-end security without compromising quality, runtime, or production throughput. The tool and process that enables such end-to-end security is enterprise threat modeling powered by ThreatModeler™.
Enterprise threat modeling is concerned with managing the organization’s overall risk through:
- Developing a thorough understanding of the organization’s unique attacker population,
- Evaluating the various assets and the level of exposure to the attacking population each asset has; and
- Analyzing the organization’s comprehensive attack surface to understand the possible ways by which attackers will initiate their attempts to access assets.
Since the threat landscape is continuously evolving with a plethora of new threats added to the cyber ecosystem daily, addressing these concerns requires a continuous, active process. As new threats are daily added, organizations need a dynamic, continuous process to determine exactly which threats are relevant to the organization, and what the potential technological and business impacts will be if relevant threats are realized. As the relevant threats are identified, and the potential impact is assessed, the organization’s process needs to press further to determine and prioritize the mitigating security controls and verifying test cases.
Enterprise threat modeling is a process by which organizations identify and understand the relevant threats faced by the organization, and by which they plan and prioritize the deployment of security resources to mitigate the likelihood of realizing those threats. ThreatModeler™ is the world’s first enterprise threat modeling platform that combines the end-to-end security focus of DevSec with SecOps’ focus on processes and tools, yielding a practical approach to rolling out enterprise DevSecOps in your organization.
To learn more about practical implementation of DevSecOps in your organization, schedule a demo today.