Within the context of information security, application threat modeling seeks to identify, understand and communicate threat information to security decision makers. Threat modeling can be used to secure system networks, applications, mobile, web, Internet of Things (IoT) embedded devices and more. In this article, we will explain how to create an effective threat model.
Threat modeling is a practice that shifts security as far to the left as possible. Threat modeling can occur as early as the planning stages within the software development life cycle (SDLC). Threat modeling lends itself to staying proactive instead of waiting until an incident occurs to react.
The process of threat modeling can save organizations on operational costs, while hardening application and infrastructure (making it more secure). Fortunately, while it is best to integrate threat modeling early in the stages, it is never too late to apply it along the SDLC. At any stage, you can gain a better understanding of relevant threats and security requirements needed.
Overview of the Threat Modeling Process
Threat modeling is relatively straightforward and typically done on process flow diagrams. IT architecture components are mapped out along with their communication nodes – connectors that indicate the flow of data in and out of components. Through the threat models, organizations can look at risk holistically and better understand their attack surface. Once understood, security teams can assess security controls to determine whether:
- Security is adequate
- More security controls are needed
- There are more than enough security controls, a reallocation of resources can happen
Threat Modeling Terminology
More and more, cyber threat modeling is becoming a priority process in the SDLC. There are three major terms that must be understood to get the most out of threat modeling.
Information asset – data that an organization maintains that is generally sensitive, confidential and/or proprietary. Information assets run the gamut within an enterprise. Examples include customer information, insider secrets and/or workflows. Information security is of utmost value to organizations. A breach of information can lead to regulatory compliance fines, unforeseen costs (for forensics and remediation) and reputational damage.
Attack Surface – the different points (attack vectors) that bad actors can use as entry ways to compromise data – either by adding malicious code or by stealing it outright. Hackers may exploit an attack surface by compromising vulnerabilities.
Security Control – the requirement implemented to mitigate (systematically reduce) threats. Security Controls may detect, counteract or otherwise reduce the likelihood of a threat happening.
Step 1: Assemble Your Teams
Bringing together the right team members is essential to making a threat modeling exercise successful. Assemble a cross-disciplinary team and include security personnel as part of the equation. The right formula will include developers/architects, operations and security – also known as DevSecOps. Other candidates include site reliability, business owners – team members who can be relied on for software development, testing and assurance, and delivery.
Restrictions should be set as far as who is authorized to access and modify threat models. Protective measures should be made to prevent unauthorized personnel don’t access, view or tamper with the information found on threat model diagrams.
Step 2: Pick Your Approach
There are a number of methodologies that you can use in order to build your threat model, including Octave, Trike and P.A.S.T.A. (Process for Attack Simulation Threat Analysis). We recommend V.A.S.T. (Visual, Agile, Simple Threat Modeling), for its ability to address the most DevSecOps needs. For example, with VAST, teams can:
- Identify relevant mitigating controls
- Implement security in the design and planning stage
- Automate key processes
- Ability to scale (up to thousands of threat models and more)
Step 3: Build Your Threat Model
According to the OWASP Threat Modeling Cheat Sheet, it is good to know what you are designing as far as the intended audience, structure and area of the IT infrastructure being mapped. Plan your scope, and consider breaking down complex infrastructures into smaller parts. It will be easier to manage and interpret. A completed threat model will serve as a use case and test case, detailing all the related components, connectors and functionality. You will also be able to identify all the internal and external actors and information flows.
Step 4: Evaluate Your Threat Model
Your organization’s threat models will enable you to understand and prioritize your data assets. It will also enable you to determine several factors, which, according to OWASP, include:
- System trust boundaries – to and within
- The actors who interact with the system
- Information flows (including to and within trust bounderies)
- Potential threats and vulnerabilities
- Threat agents that can exploit these vulnerabilities
- Exploitation impact
ThreatModeler Utilizes the V.A.S.T. Approach and Includes Intuitive Features
Threat modeling software offers features and functionality that can help to streamline threat modeling beyond the traditional white boarding approach. ThreatModeler is a leading platform that can provide the insights driven by updated threat intelligence. Programmers took the threat modeling activity and automated it, helping organizations to shave up to 85% off the time-cost needed to build a threat model. Additionally, threat modeler enables collaboration between authorized teams and integration with leading SDLC ticketing platforms to ensure threat mitigation is carried out.
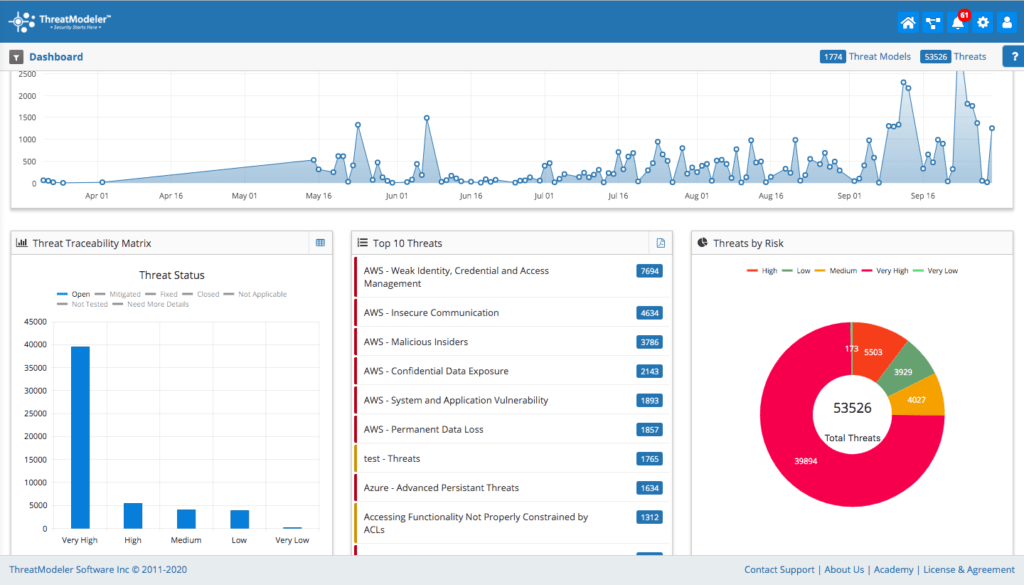
ThreatModeler helps to evaluate threats, vulnerability and risk by organizing threat information into a dashboard that organizes threat results based on priority. In addition to an executive summary, users gain a detailed report of identified threats, requirements, test cases, components, data exposure (of application or system being threat modeled and a listing of linked projects. Once created, users may add ThreatModeler projects to a Library, enabling architects to scale threat models across the entire organization.
ThreatModeler will enable organizations to conduct a holistic risk analysis and shift security left. It’s Intelligent Threat Engine provides you with the ability to threat model successfully with Web, mobile, IOT-embedded applications, AWS and Azure. We encourage you to request a demo of the award winning ThreatModeler platform.
Upcoming Webinar: How to Threat Model an AWS Microservice Architecture
On Thursday, October 3, 2019, ThreatModeler will host a webinar on How to Threat Model an AWS Microservice Architecture ThreatModeler is an Advanced Technology Partner and offers full integration with AWS Microservice threat intelligence libraries. Explore how threat modeling can identify threats unique to your system or application architecture.