It’s just the beginning of 2020 and there have been a number of data breaches to raise browse and concern over the state of cybersecurity for the New Year.. The following is a brief summary of some of the most relevant cybersecurity breaches uncovered. From healthcare, to Microsoft to the financial industry, there has been suspicious activity and vulnerability mishaps occurring.
FDA Issues a Public Notice About Security Vulnerabilities in Medical Devices
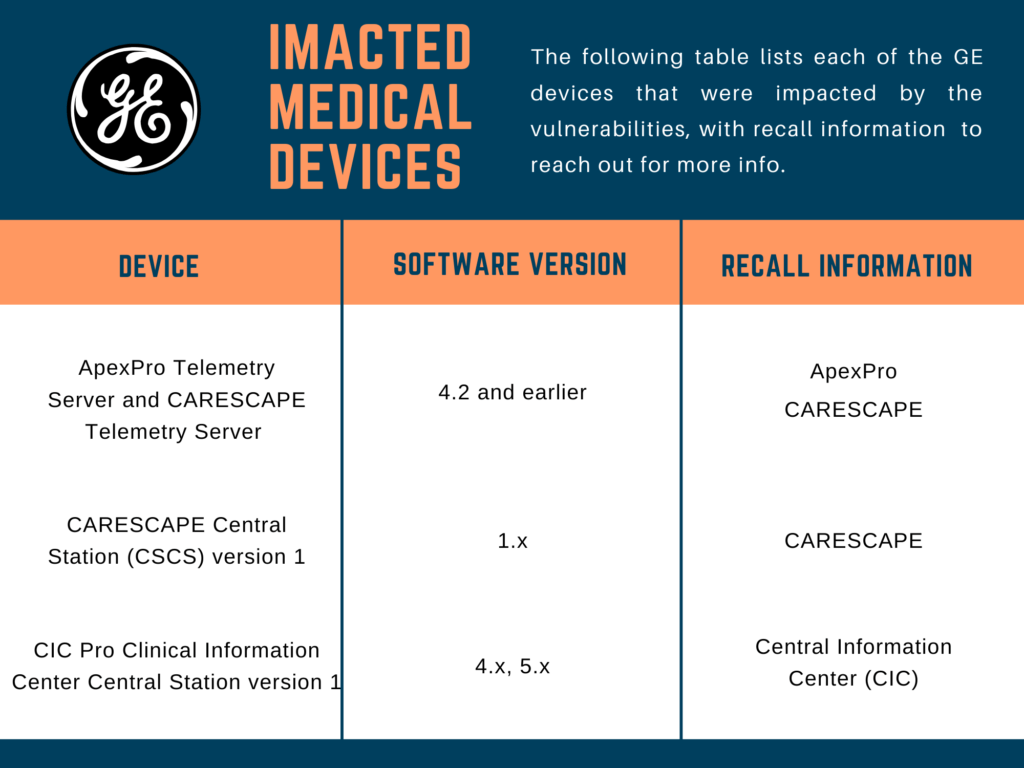
Towards the end of January, the Food and Drug Administration (FDA) issued a public notice to healthcare providers, facility personnel and customers warning about a vulnerability in General Electric healthcare equipment that monitors patient health. According to the release, “cybersecurity vulnerabilities in certain GE Healthcare Clinical Information Central Stations and Telemetry Servers may introduce risks to patients while being monitored.”
If left unmitigated, hackers can compromise and tamper with the device and cause injury – even death – to patients connected to the devices. Examples include:
- Silencing the alarms
- Causing false alarms
- Creating some other alarm-related disruption
A third-party cybersecurity firm discovered the vulnerability. The FDA included a table with the following information about product recalls, which GE issued on November 19, 2019 in an “Urgent Medical Device Correction” letter issued to raise consumer awareness:
GE is endeavoring to resolve the issue. In the meantime, GE recommends that facility owners:
- Separate the impacted devices from the hospital network
- Set restrictions on personnel who have access to the equipment
- Ensure passwords are secure, e.g., changes made to default passwords while securing internet traffic (e.g., firewalls).
FDA Making a Concerted Effort to Communicate Medical Device Cybersecurity Risk
The FDA is raising a red flag on cybersecurity issues related to medical devices. IT has become vested in communicating with healthcare facilities, doctors and patients to uncover risks tied to technology used for patient care.
Currently, there is a no perfect way for manufacturers to make bug fixes to medical devices without doing so manually. This disconnect makes it difficult for people using the device – whether they be a medical professional or patient – to make patch updates easily and in a timely manner needed to ensure patient safety.
The FDA said no “adverse events” that can be traced to the vulnerabilities have turned up. However, they urge people to report any issues consumers, facilities and other impacted people may have with the device via the MedWatch Voluntary Reporting Form, which is available to patients and medical providers.
Microsoft Breach Left 250 Million Data Records Exposed
After completing an investigation, on January 22, Microsoft announced a vulnerability that left 250 million data records exposed on an internal database utilized to support case analytics. The data spanned 14 years. Fortunately, the change to the network security group on the database (revealed by the investigation as having been made on December 5, 2019) did not impact data involved in Microsoft’s commercial cloud services.
As part of its standard practice, the company redacts personal information from its case analytics using automated tools. All but some data records would have had the personally identifiable information (PII) removed. Microsoft concluded that no foul play occurred and that the data breach did not affect most customers’ PII.
There were some records that would have left PII unredacted, such as when the information was in a non-standard format. Microsoft notified those customers who were compromised. When engineers were notified about the vulnerability, on December 31 they restricted access to the database. Further actions that Microsoft is taking include:
- Conducting audits of the network security rules
- Increasing scope increase on mechanisms that detect security rule misconfigurations and alert service teams
- Implementing additional redaction automation
UPS Involved in a Data Breach
A data breach involving phishing may have compromised the data of United Parcel Service (UPS) customers between September 29, 2019 and January 13, 2020, the company announced in a letter addressed to those who may have been impacted on January 21. The letter revealed how a hacker utilized a phishing cyberattacks to target and gain access to email accounts tied to UPS stores.
The company, which provides package delivery and supply chain management services around the globe, has since enlisted a third-party cybersecurity company to conduct a full investigation.
The American package delivery and supply chain management company with global customers responded by launching an investigation with the help of a third-party digital security firm to figure out what happened. By compromising email accounts, the hacker(s) in question made away with document data in emails sent to store locations that contained various levels of customer details. Less than 2%, or 100 stores, were impacted.
In the letter issued to customers, UPS explained how it is providing free credit monitoring and identity theft remediation services. “We take the privacy and security of your personal information very seriously and for this reason want you to understand what we are doing to address this issue and what steps you can take to protect yourself …”
PayPal and American Express Targeted By a Sophisticated Phishing Campaign
Two leading financial companies are being targeted with a phishing scam that goes after usernames and passwords. A cybersecurity firm that provides phishing protection and other services company reported the phishing scheme on January 21.
Amazon and Apple are previous targets of the phishing attack. On the dark web, a cybercrime entity named 16Shop began selling kits for less than $100, which would enable cybercriminals to fall prey on PayPal and American Express through phishing.
When activated, the kits resemble legal email marketing software that tracks clicks, controls content messaging based on segments, and controls other parameters, such as scheduling marketing campaigns. 16Shop also offered upgrades for the sophisticated cybercriminal software, so hackers can purchase features that closely resemble legitimate customer support. Additional features include templates and message automation. The kit upgrades make cyberattacks easier to deploy.
This form of cyberattack goes after the human element, relying on ransomware, phishing and other social engineering strategies to disarm the victim and infiltrate the attack surface. Targets should know that financial companies will never ask you to provide private, sensitive information via email. The emails used in these campaigns tend to have flaws, such as:
- Senders who are not recognized by the victim
- Typos in the subject line or message body
- Suspicious email address links.
As Cybercrime Escalates, Secure Your Attack Surface with ThreatModeler
As detailed above, all it takes is a slip up to have the PII of customers compromised. Increasingly, hackers are finding new and sophisticated ways to target victims, putting users in personal danger while causing severe damage to even the largest corporations. Don’t become the next casualty in the war against cybercrime.
Threat modeling is an activity that goes hand-in-hand with secure CI/CD. Threat modeling helps to identify attack surface threats, list them, prioritize them and implement proper security controls. Traditionally, threat modeling was a manual, at times ad hoc approach involving whiteboards, spreadsheets and process flow diagrams.
With ThreatModeler, the process flow diagrams remain, but automation and integration with the cloud, among other tools, has made threat modeling an approachable, collaborative process. Learn how ThreatModeler helps organizations to completely understand their IT ecosystem to proactively mitigate threats by booking a demo to speak to a ThreatModeler expert today.





