The rapid expansion of cloud computing capabilities and the Internet of Things has resulted in tremendous advances in cyber-physical systems. A cyber-physical system, or CPS, connects the virtual world with the physical world, allowing greater mobility and freedom for individuals who require interfacing with intelligent devices.
For the May Threat Model of the Month, we consider a cyber-physical system for healthcare. Such systems provide smart feedback and automated updates of digital patient data. CPSs also allow for continuous monitoring through biosensors and smart devices in healthcare environments. Healthcare cyber-physical support real-time acquisition of pertinent medical data for efficient, often life-saving decision-making. CPSs also make it possible for patients to live and recover in the comfort of more relaxed environments, such as their own home or an assisted living center, while still being continuously monitored. Regardless of where the patient is, medical assistance is informed with the patient’s real-time monitored data and access to the patient’s doctor or other specialists is immediately available.
Building a Healthcare Cyber-Physical System Threat Model
Improved Security with ThreatModeler™
Essential for any healthcare application or IT system will be the security of the patients’ Private Health Information or PHI. Because of the highly sensitive nature of PHI, the healthcare industry is subject to many regulations – including HIPPA and HITECH – intended for securing patient’s data. Private health information is highly monetizable by malicious parties, and the collateral damage to patients from a PHI data breach can be catastrophic. Thus it is very important to thoroughly study the potential threats and enumerate the mitigating security requirements for every healthcare application or IT system. It is especially important to properly secure healthcare cyber-physical systems because they are complex systems integrating applications, the cloud, devices, and people.
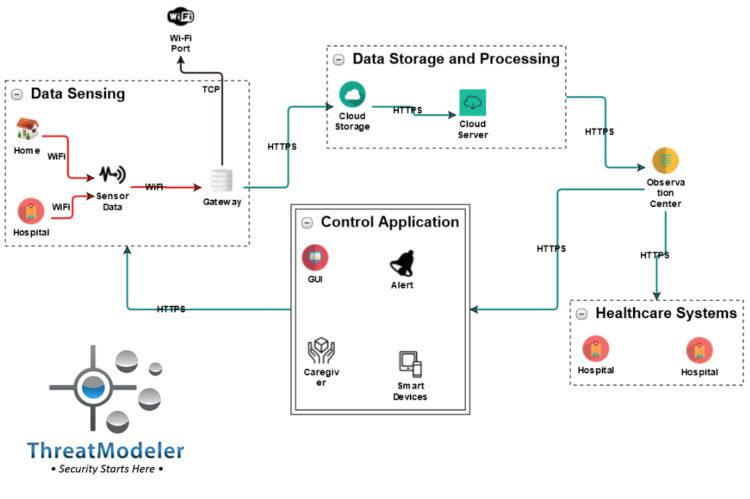
As shown on the threat model diagram below, from a high-level perspective, a basic healthcare CPS has five essential components:
- Data sensing and collection from patients, either in home or in hospital, from various sensors;
- Data storage and processing via cloud-based services;
- Observation center in case query processing triggers an alarm or flags for interactive response;
- Additional health care systems which may be necessary for consultancy or specialist interaction supporting the observation center clinicians; and
- A control application to actuate the necessary patient care.
Transmission, processing, or storage of patient PHI is involved in almost every aspect of a healthcare CPS. The threat model based on the above diagram – built in about 10 minutes by a non-security expert – identified 76 potential threats and 34 mitigating security requirements to protect that information and keep the healthcare system compliant with regulations. The summary threat report for this threat model may be downloaded here.
Schedule a demo to learn more about how efficiently ThreatModeler™ allows users to build threat models for complex systems like CPSs.