On Friday, September 20, 2019, the Cyber Tech Accord invited ThreatModeler to speak on its panel appearing at the 2nd Annual Cybersecurity Summit. Alex Bauert, CISSP, CSSLP – ThreatModeler’s Senior Director of Threat Research – sat alongside esteemed Tech Accord panel members to share ideas and information with attendees.
Alex remarked, “Threatmodeler is a member of the Cyber Tech Accord and was invited to attend a panel discussion at the 2nd annual CISA Cyber Security Summit. I had the privilege to attend the 2019 CISA Cyber Security Summit as a panelist for the Tech Accord Vulnerability Handling discussion. During our 45-minute presentation, we touched on a number of aspects of vulnerability handling, including responsible disclosure, standards and enforcement. I spoke to the benefits of responsible disclosure and how it relates to the software supply chain.”
Bug Bounty Hunters an Emerging Trend Discussed at the Annual Cybersecurity Summit
Another topic that came up is bug bounty hunters. A near-legitimate profession in the making, bug bounty hunters can make a good full-time living – or a substantial fortune. Bug bounty hunters spend their time in search of undetected bugs, flaws and vulnerabilities in software application.
These hidden bugs are sometimes known as zero-day. When hackers exploit a zero-day vulnerability, it is known as a zero-day exploit. A strong bug bounty hunter will be able to explain the issue as clearly as possible. Bug bounty hunters will make recommendations on how to patch the bugs or create workarounds to mitigate them.
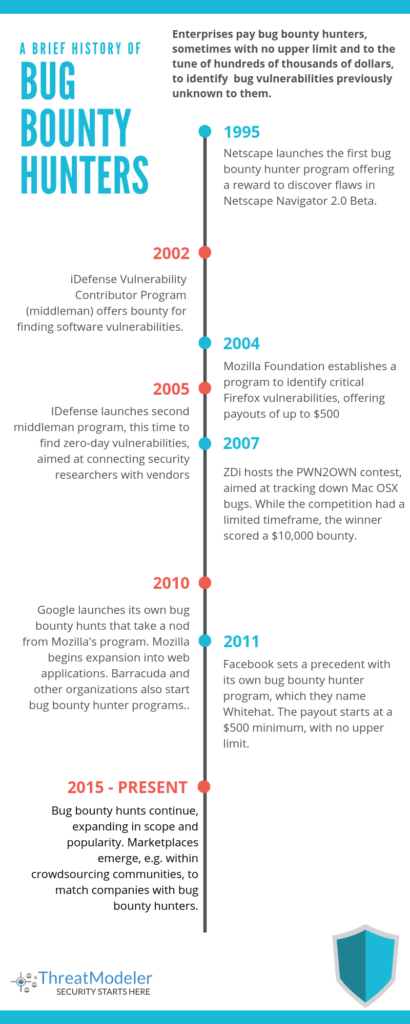
A Brief History of Bug Bounty Hunters
Bug bounty hunting started 20 years ago and, in recent years, has exploded in popularity. Nowadays, every organization worth its weight – including top technology companies – has a bug bounty hunter program in place. Big companies such as Google, Microsoft, Apple and Facebook have some sort of program in place, and call them Vulnerability Reward Programs (VRP).
The Pentagon has even issued its own government program, aptly titled Hack the Pentagon. Take a look at our bug bounty hunter timeline for a detailed exploration.
How Bug Bounty Hunter Programs Work
Organizations will formally invite bug bounty hunters to find and fix bugs. The reimbursement amount for finding vulnerabilities is based on the severity of the bug found. In typical cases, the payout can range from anywhere in the $1k – 30k range. Companies such as Facebook have set limitless payout structures for successfully finding bugs. In some cases, such as finding the next super bug, hackers are being paid six to seven figures.
What Makes a Good Bug Bounty Hunter?
Bug bounty hunters will have a certain level of technical competency, plus a curiosity to learn new things. An understanding of hacking will also help. No degree is needed, although a slew of training courses have cropped up. A bug bounty hunter needs to be persistent and aggressive. S/he needs to anticipate fluctuations in pay due to the lack of stable employment, or payout amount.
Dangers of Bug Bounty Hunters
There is some controversy tied to bug bounty hunters, due to the violative nature of their work. There are bug bounty hunters who act maliciously against a target, by taking their own initiative to target an organization’s information system. After a bug bounty hunter has compromised the data contained in their system, s/he can demand ransom to avoid a negative outcome. Examples of detrimental outcomes include posting sensitive, confidential data publicly or selling the data, e.g. to lists on the dark web.
The bug bounty hunter can potential bring damages to an organization’s reputation. Hackers can turn the public’s perception against an organization and cost them consumer trust, e.g. for not being able to identify and reduce the likelihood of violating customer data. An organization, therefore, stands to benefit from what the public would perceive as good behavior and public disclosure.
ThreatModeler Protects Organizations From Threats to Improve Transparency
Let’s look at real world scenario by reviewing the functionality of ThreatModeler’s platform. If there is component built with Apache Tomcat and information emerges on a reliable resource such as OWASP, WASC and CAPEC, that information is added to ThreatModeler’s Threat Intelligence Framework. Developers will pick the threat intelligence up, and build threat information – including security requirements into the solution’s Library.
ThreatModeler provides enterprises with visibility of the entire attack surface informed by its Threat Intelligence Framework. This helps an organization in addressing issues of transparency and disclosure involved with managing a technology stack. Once the vulnerability is found by a bug bounty hunter, does the organization release the information to vulnerability databases?
Disclosure matters, from a compliance and customer privacy level. If threats and known vulnerabilities are there, it’s important for security teams to address them, at the least by acknowledging and accepting them as a part of its risk appetite. Within the threat model, security requirements with patches are included.
ThreatModeler Delivers Visibility of An Organization’s Attack Surface
Data security is a big deal from a software development point of view, with vulnerability disclosure an important issue – especially with the software industry surging with growth.Most organizations are software consumers. What do customers want? A technology stack that is as protected from threats and vulnerabilities as possible.
How do you approach vulnerability disclosure? As far as business processes go, threat modeling helps organizations to dimensionalize their technology stack and better understand their attack surface. Threats are there, known vulnerabilities are there. ThreatModeler puts bugs in plain view within your IT infrastructure so security teams can make decisions about it. With a platform that helps you to visualize and understand your attack surface, you reduce the likelihood of unknown vulnerabilities.
Smart organizations want transparency in the procurement of software as far as the people and the organization behind it. This helps the CISO with their job, providing transparency for compliance sake – to internal policies and external regulating bodies.
Security teams want stack transparency, including knowledge about the vulnerabilities that are potentially bought into a software at release. Supply chain affects vulnerability and architects need to know what security threats exist when implementing software, and what security controls they need to put in place. ThreatModeler will help to inform architects on what threats and vulnerabilities they are putting into a code stack – and how to secure against them.
Throughout the supply chain, ThreatModeler can help organizations to establish and maintain transparency, including with third-party software vendors, by better understanding their entire IT ecosystem. Book a demo to speak to a ThreatModeler expert today.





