This is a recap of the “Automated Threat Modeling For Applications Using Avocado” webinar presented recently. To view the entire webinar (including a demo of the integration), click here.
For people who are practicing threat modeling on a day-to-day basis, or trying to adopt threat modeling within their enterprise, we all know the security by design strategy that many are embarking upon. There are several challenges in terms of how we effectively threat model, particularly given how many applications there are in an enterprise space. This article will cover several of those challenges.
Key personas we’ve encountered that are trying to adopt threat modeling and drive threat modeling as a hygiene within the organization each share a common thread of challenges.
Developers
One sentiment we hear is “I have too many developers. I don’t want them to be tied into threat modeling because today’s threat modeling requires a lot of manual work. We don’t have time for it because we have to deliver capabilities for our business. So, we don’t want to put our developers into doing this.”
Security
The security folks are overwhelmed because now the developers are not participating in threat modeling. And security can’t do it alone in a silo.
Operations
Likewise, the operations people face similar challenges. As the number of applications in an enterprise grows, threat modeling becomes a daunting task to manage.
CIOs
These obstacles are the primary reasons why people shy away from threat modeling as part of their daily work. In understanding the CIO’s investment strategy when it comes to threat modeling, one of the common answers is, “We have so many great tools in the industry.”
But the problem is not about the tools. It’s about the amount of time we spend, and the ROI to do something like this when you have a large application portfolio. With their current threat modeling practice, 10% of the ecosystem gets covered – typically the ones they know are the most critical applications.
From a threat vector perspective, the weakest link in the chain is one that probably gets exploited the most. But with their current threat modeling processes, they can’t say for certainty that they have addressed all the critical threat areas.
CISOs
CISOs, now empowered to make security decisions from an organization perspective, face the dilemma of building trust. CISOs need to instill the confidence in stakeholders that security teams are effectively and consistently delivering security to the organization. In order to do this, the CISO must understand what the applications are to understand application risk, not just the functions developed through the applications.
Wrong Threat Modeling Approach
Without an adequate, automated threat modeling tool powered by a comprehensive threat intelligence library, DevOps faces the risk of building imprecise threat models. A threat model should be a living, breathing document. If DevOps does not have a tool in place that automatically updates based on application and/or underlying infrastructure changes, they run the risk of working with an outdated threat model.
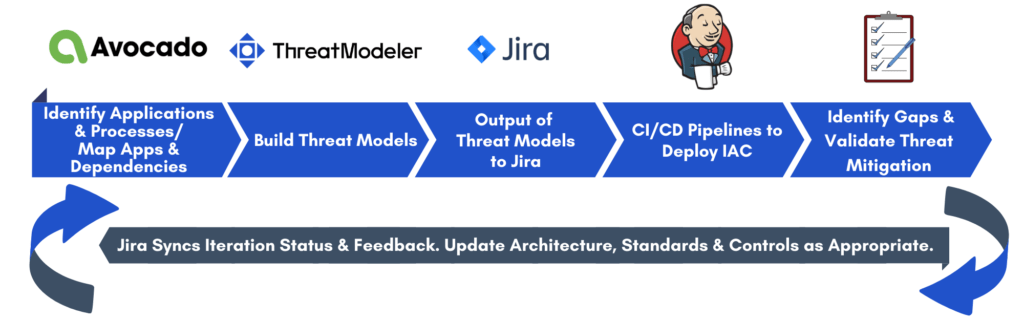
ThreatModeler and Avocado Delivers Unified Threat Modeling for AppSec and Cloud
Avocado and ThreatModeler have partnered up and built an automated threat modeling solution.
Avocado, is an application security company focused on securing applications using zero trust, and patented technologies such as beacons and machine learning. Avocado Reveal is a capability in the platform that provides deep application forensics on all application data flows happening in runtime without even modifying your application.
Read more about Avocado and ThreatModeler integration by clicking here.
Once deployed, Avocado plugins start discovering all the flows and once collected, feeds it into ThreatModeler. The ThreatModeler platform takes the synthesized, context-sensitive, application-relevant forensic metadata and automatically creates a threat model that’s highly relevant to the application. Since the generated threat models are application-centric and specific, the outputs are context sensitive, enabling DevOps to create a threat model that is very relevant to the application.
ThreatModeler brings in a lot of other capabilities. In ThreatModeler, you can take immediate action – prioritize your threats, prioritize your tasks, and push tickets into JIRA – with updates and reporting for all stakeholders. Mitigate all your threats in one shot or over time, continuously. With ThreatModeler, DevOps can integrate directly with cloud environments, such as Google, Azure, and AWS.
The merging of the two technologies enables DevOps to threat model whether it’s in the cloud or any other environment. Teams can marry cloud-based solutions to on-prem solutions and provide a full, broad-spectrum view of all the threats across an enterprise, irrespective of where the applications are running – whether in a private data center, or in the cloud.
Benefits of the ThreatModeler-Avocado Integration
CISOs
The benefits to the various personas become clear, particularly if you are a CISO. Now, since you have automated the whole threat modeling landscape – generating threats, gaining an understanding of where the threats (and potential threats) exist, the CISO better understands the risk posture, enabling him to prioritize security decision making and reduce cost. CISOs no longer focus on what is not relevant.
Developers
From a developer perspective, there are productivity benefits, increased security awareness, and driving accountability. Now, the developers can understand threat modeling, pull the needle out of the haystack and understand what’s actually happening within their application for specific threats.
Security Architects
Security architectures can enforce security by design and enforce architectural security and architecture governance over a set of applications across the enterprise.
Operations
From an operations perspective, it obviously helps to understand where to focus from an application perspective, in case there’s an issue. Operations can identify which application has an issue, act upon, and manage the change of those applications appropriately. All-in-all, a reduction in operation load occurs.
DevOps now has the ability to manage a large number of applications at scale. Instead of doing 20 applications, they can now threat model thousands of applications through automation. Threat modeling becomes more inclusive, while at the same time minimizing the number of people needed to do a threat model. Developers can be less involved but still make effective contributions to threat modeling, particularly when there are specifics in the development of the application where s/he needs to be more involved.
To learn more about how Avocado and ThreatModeler can secure your cloud and legacy systems at scale, click here to schedule a live demo with a threat modeling expert.