
Dec 7, 2017 | DevOps, Enterprise Threat Modeling
If there is such a thing as “traditional DevOps,” it is a two-dimensional beast. Consider, for example, the relatively simple two-dimensional graph shown below. Let development be represented on the vertical axis and operations be represented on the horizontal. Then...

Nov 29, 2017 | DevOps, Enterprise Threat Modeling
The next most popular conversation around DevOps has to do with where the bottleneck is currently at its worst, DevOps security. Throughout this series, How to Improve your DevOps Implementation, we have examined, how to improve the throughput by integrating security...

Nov 22, 2017 | DevOps, ThreatModeler
Organizations are becoming increasingly digital-driven, causing the business world to become highly interconnected. Relationships between organizations and their vendors, suppliers, and distributors are now remotely managed across global networks. Evolving customer...
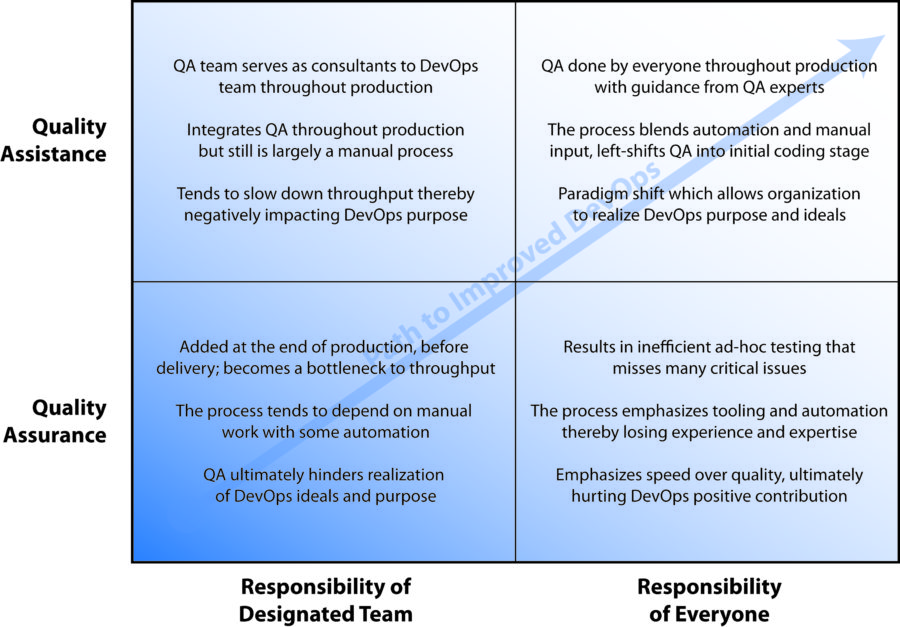
Oct 27, 2017 | DevOps, DevSecOps, Enterprise Threat Modeling
Throughout this series on How to Improve your DevOps Implementation, we have considered how organizations can left-shift security fully into the project design phase and how organizations can establish genuine cross-functional collaboration. In this 3rd of 7 parts, we...
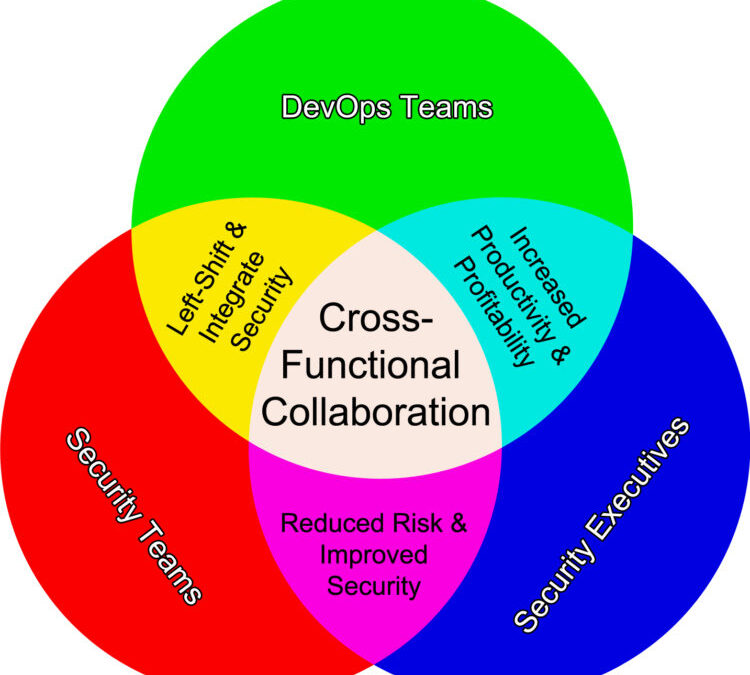
Oct 17, 2017 | DevOps, DevSecOps, Enterprise Threat Modeling
Organizations seeking to improve performance and their bottom line need look no further than improving their DevOps implementation. Based on survey results from more than 27,000 respondents over six years, organizational performance is directly correlated to how well...

Oct 5, 2017 | DevOps, DevSecOps, Threat Models, ThreatModeler
A flat tire on your morning commute can leave you stranded for hours, and a broken cog in the factory can wreak havoc on the entire assembly line. The same is true for DevOps implementation. It is virtually impossible to realize the promised benefits of DevOps from a...







