Blog
Explore our latest blogs, where we cover everything from software security and threat modeling to compliance and risk management – covering the topics that matter to you.
Why CISOs Implement Enterprise Threat Modeling
Threat modeling for critical and high-risk application security has been a mainstay of software development for nearly a decade. The immediate...
Improving DevOps: Including Legacy Systems
If there is such a thing as “traditional DevOps,” it is a two-dimensional beast. Consider, for example, the relatively simple two-dimensional graph...
Improving DevOps Security: Shifting Security Right
The next most popular conversation around DevOps has to do with where the bottleneck is currently at its worst, DevOps security. Throughout this...
DevOps Transformational Leadership
Organizations are becoming increasingly digital-driven, causing the business world to become highly interconnected. Relationships between...
Improving DevOps with Operational Visibility
DevOps creates an environment which may be systemically flawed, in part due to a lack of operational visibility into application post-deployment...
IoT Security is an Economic Issue
Reporters around the globe are writing and watching as IoT security takes another dark turn with a new botnet. The new beast, dubbed IoTroop –...
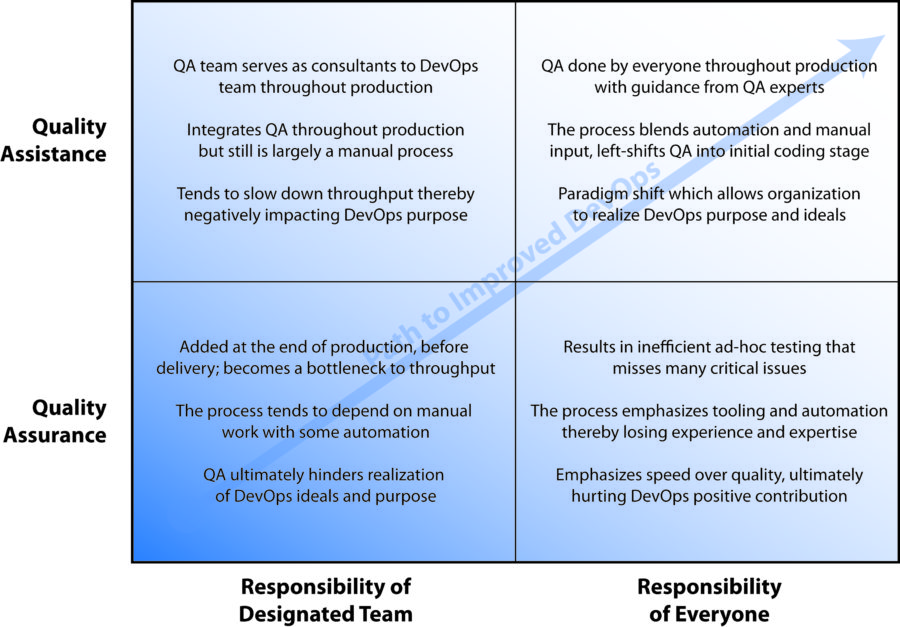
How to Improve DevOps Quality Assurance
Throughout this series on How to Improve your DevOps Implementation, we have considered how organizations can left-shift security fully into the...
How to Create Cross-Functional Collaboration
Organizations seeking to improve performance and their bottom line need look no further than improving their DevOps implementation. Based on survey...
How to Improve your DevOps Implementation
A flat tire on your morning commute can leave you stranded for hours, and a broken cog in the factory can wreak havoc on the entire assembly line. The...