Faster Starts
Accelerate model creation with AI-powered imports and intelligent cloud mapping that keep pace with complex architectures.
Stay up-to-date with
Simplified AI.
Governed. Protective. Practical.
ThreatModeler 7.5 marks a meaningful shift in how AI is applied across the platform, integrating AI in deliberate, controlled ways that align with established threat modeling practices.
The result is simpler adoption and clearer governance, with AI assistance that fits naturally into existing workflows and supports secure-by-design practices at scale.

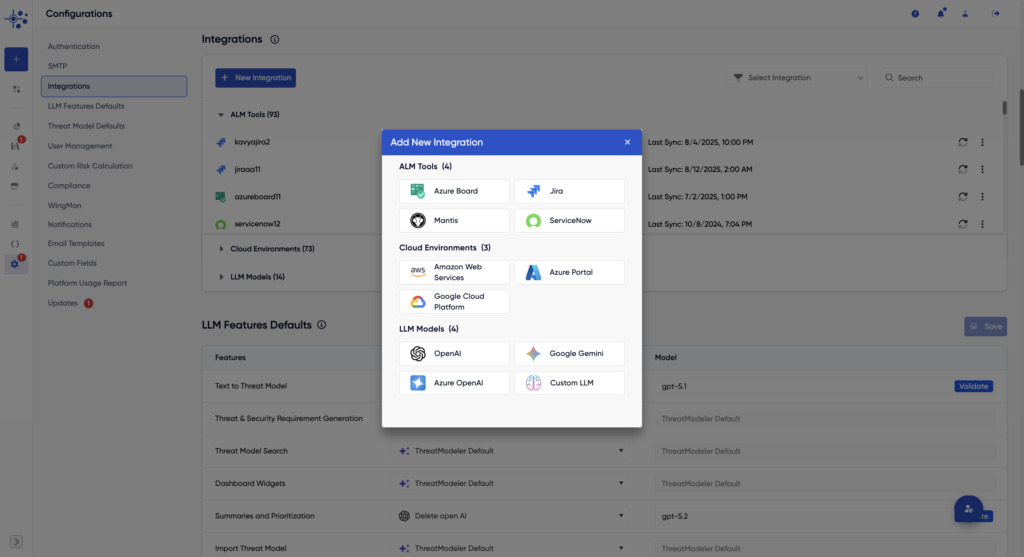
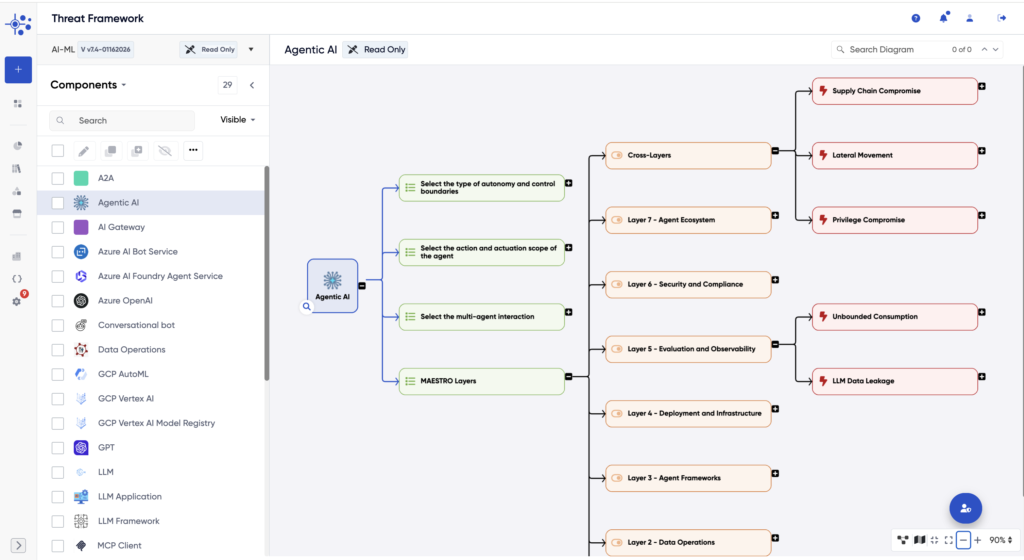
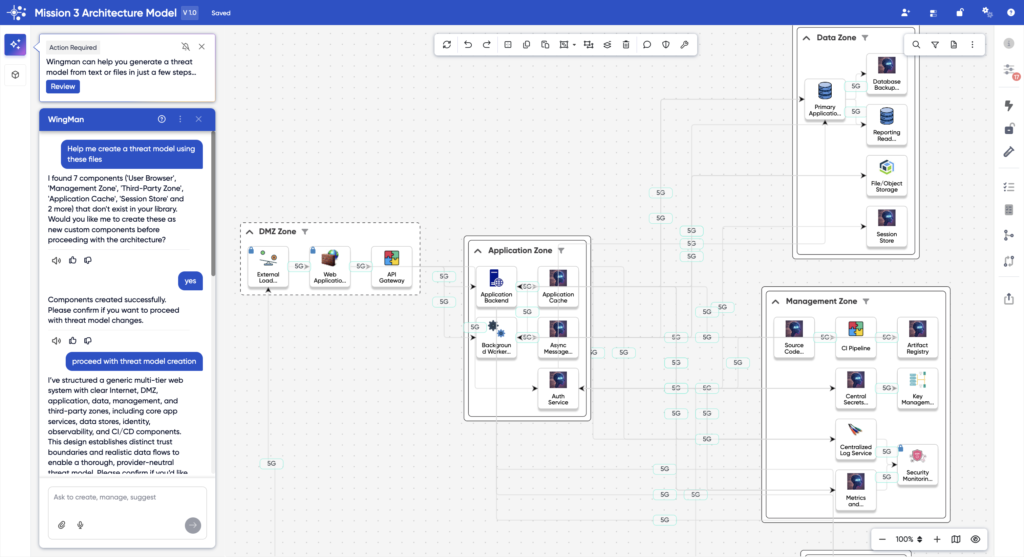
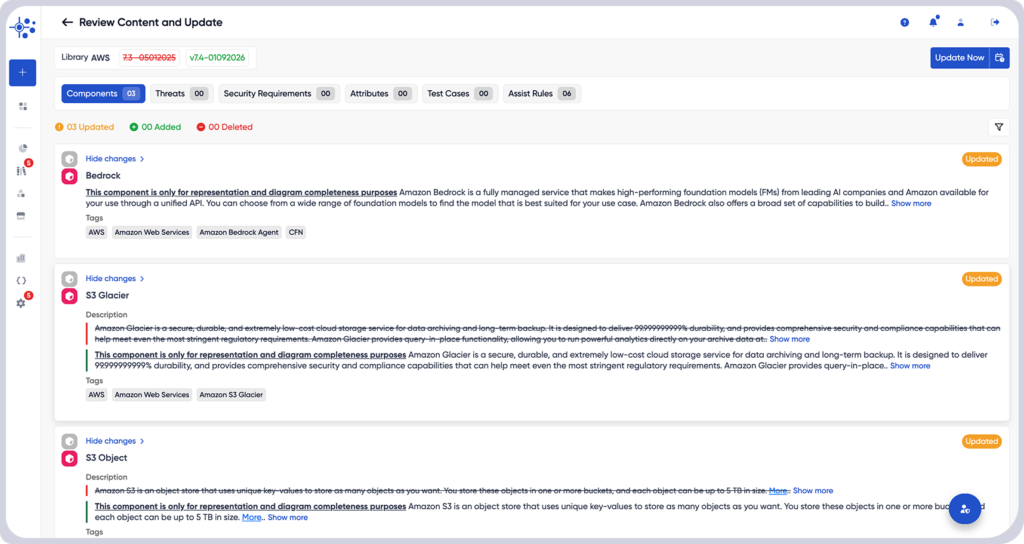
Maintain compliance and consistency with enhanced context-based rules.
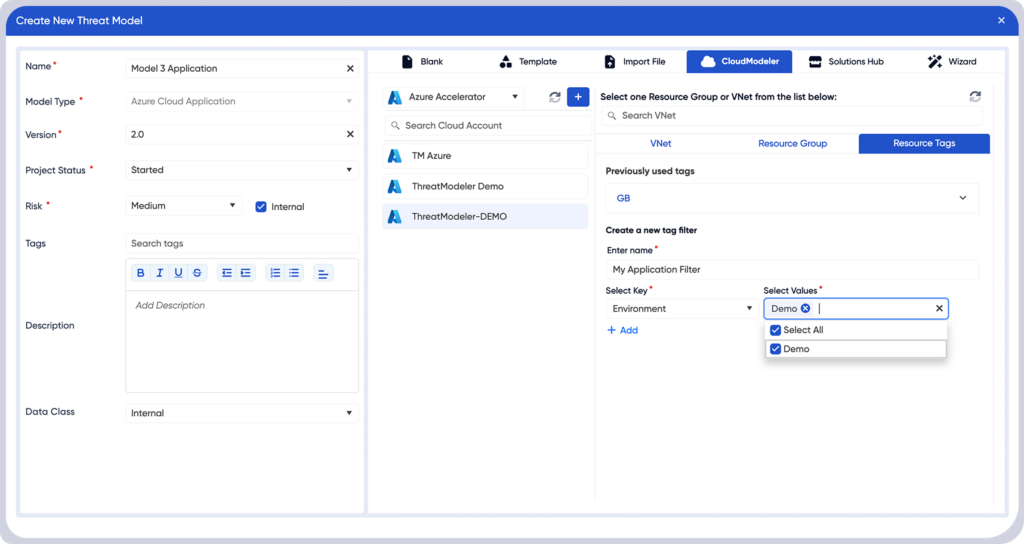
Accelerate model creation with AI-powered imports and intelligent cloud mapping that keep pace with complex architectures.
Continuously adapt to evolving risks with dynamic insights into AI-driven development and multi-cloud environments.
Focus on what matters most with attack path visualization and residual risk analysis that guide remediation decisions.
Bridge the gap between security and development with collaboration tools, executive-ready reporting, and compliance coverage across 180+ frameworks.
Find case studies, data sheets, white papers, and more threat modeling resources.
