Demo blogs
Apr 18, 2025Build faster
RISK LESS
Intelligent threat modeling, built for the modern enterprise.

Secure your apps, from design to production
The standard in scalable threat modeling
Comprehensive coverage provides faster, non-disruptive identification and remediation of threats—from core to cloud to edge.
-

Generate models in minutes
-

Pinpoint risks in seconds
-

Mitigate threats with ease
How it works
Built on cutting-edge technologies, we empower organizations to maintain a constant view of threats, dynamically implement mitigation strategies, and unify security and DevOps teams—with unprecedented ease, precision, and scale.

Prioritize
Identify critical risks with built-in threat intelligence.
RESPOND
Deploy security controls with turnkey solutions.
SEE
Visualize infrastructures, architectures, and app environments.
A secure by design platform built for scale
Build faster and secure by design at every stage.
ThreatModeler
Secure Apps
by Design
IaC-Assist
Secure Code
to Cloud
CloudModeler
Secure Cloud Infrastructure

The ThreatModeler Intelligence Platform
Advanced
Automation
Adaptive
AI/ML
Copilot
Next-Gen
Frameworks
Expansive
Threat Libraries
Built-in
Compliance
Advanced Integrations
With the ThreatModeler platform, you get:
2,500+
security requirements
180+
compliance frameworks
1500+
threats
2900+
components
100+
protocols
With the ThreatModeler platform, you get:
2,500+
security requirements
180+
compliance frameworks
1500+
threats
2900+
components
100+
protocols

Proven solutions.
Proven results.
See how Charles Schwab protected their apps
and infrastructure while reducing the burden
on security and development teams by over 50%.
COMPANY SIZE
Enterprise
INDUSTRY
Finance
Trusted Partners


EBook
Ultimate Guide to Threat ModelingTake a proactive and strategic approach to identifying threats across your apps, infrastructure, and code

White Paper
Threat Modeling Benefits for the CISOFind out how you can impact every aspect of your organization with actionable security benefits
Let’s talk

Threat modeling done right
Spanning ThreatModeler, CloudModeler, and IaC-Assist, our intelligent capabilities unite cloud, product, and security teams to proactively minimize threats throughout your entire infrastructure at any scale.
Self-Service
Build models, diagrams, and mitigation plans with ease.
Comprehensive
Implement threat modeling across your entire portfolio.
Embedded
Minimize security risks as part of Cl/CD pipelines.
Compliant
Achieve compliance with built-in regulatory frameworks.
Build faster, secure faster
Import and model instantly
Build threat models from just about any source with built-in GenAI and ML insights.
Visualize and customize
Automatically map components and data flows, then customize models with user or Al-generated suggestions.
Identify and prioritize
Contextualize critical risks using up-to-date intelligence and an extensible threat library.
Implement and prevent
Mitigate risks with recommended security controls using intelligent path analysis.

Automated threat intelligence, at your fingertips
Intelligent Threat Engine (ITE)
Gain a holistic view of your risk by automatically correlating the latest threat intelligence and security requirements to your applications and infrastructure.
-
Decipher component and system-level threats
-
Reduce noise and false positives
-
Apply security controls using attack path analysis
Powered by ThreatModeler Copilot
Turn anything into a threat model
Rapidly iterate, anywhere in your journey
Access curated and personalized recommendations
Unify security and DevOps
ThreatModeler bridges the gap between security and development teams while promoting a more thoughtful, secure, and collaborative way to design and maintain applications.
For security teams
Automate threat modeling at scale and significantly reduce the time, effort, and resources needed for comprehensive risk assessments and mitigation.
• Mitigate threats on-premises, in the cloud, and at the edge
• Achieve secure-by-design application postures
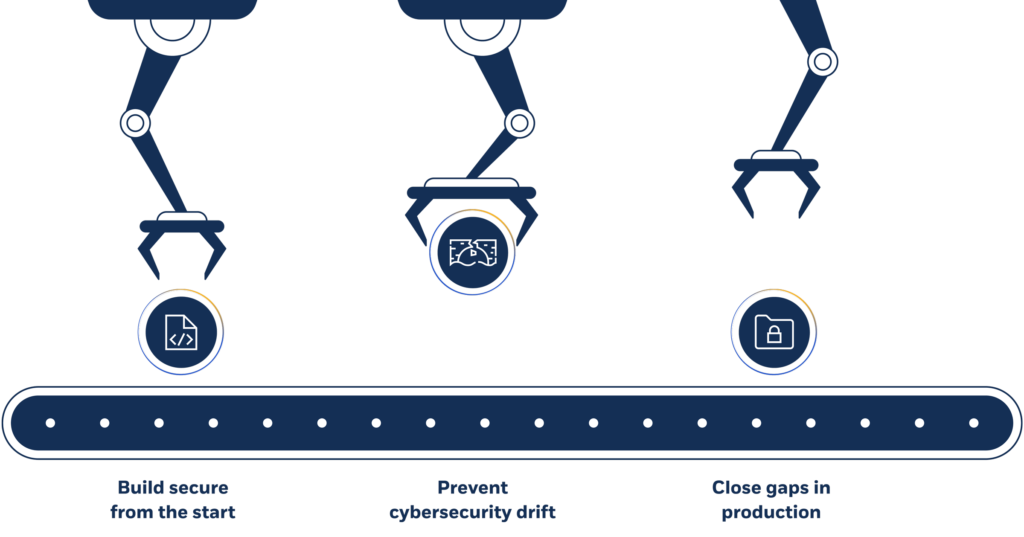
• Prevent security gaps and cybersecurity drift
For DevOps teams
Integrate threat modeling into CI/CD pipelines, address risks directly within development cycles, and reinforce security without disrupting the pace of innovation.
• Proactively minimize threats in development
• Validate designs and prevent surprises in production
• Embed threat modeling within software delivery models