Development teams and infrastructure teams need specialized threat modeling practices in order to optimize each of their unique security requirements. The VAST threat modeling methodology lists these two practices as application threat modeling and operational threat modeling, each delivering key business benefits to maximize business security efforts.
To paint a better picture of their differences, application threat modeling allows developers to prioritize and mitigate threats early on in the design phase of applications, before rolling them out to the public. This process has little use for infrastructure teams who don’t need to write code or create applications.
Instead, on an operational infrastructure level –servers, databases, load balancers, and other such infrastructure components– operational threat modeling helps these teams to mitigate inherent threats in the infrastructure of a business while aligning with business strategy and budgeting.
Let’s take a deeper dive into both types of threat modeling to gain a better understanding of their unique business benefits.
Application Threat Modeling
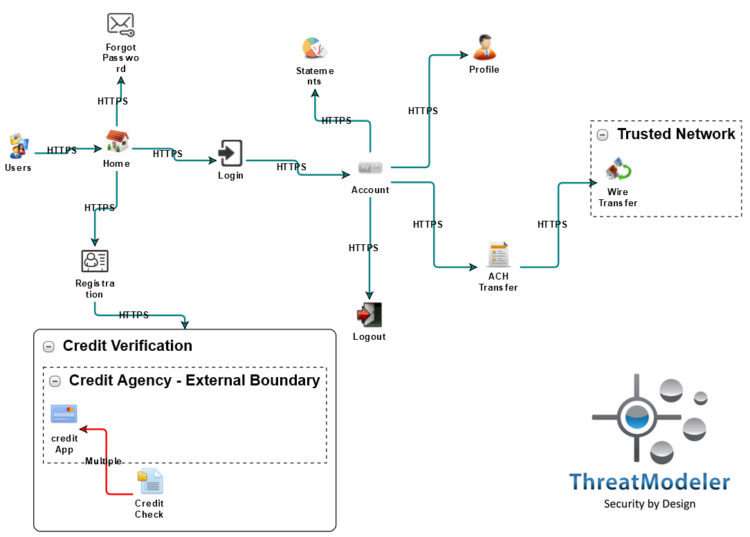
Application threat modeling should focus solely on the application for which it is created. The primary purpose is to:
- Identify the threats (OWASP Top 10, etc) that are pertinent to that application.
- To indicate how developers need to address those threats starting with the creation of a process flow diagram (PFD).
The PFD allows developers, security professionals, and other stakeholders to build and modify threat models as functional maps – a visual decomposition of an application in accordance with the way developers think about the coding process. Even without technical security expertise, PFD’s are clear and easy to understand for developers because they complement with the Agile methodology for development. This helps decrease the back and forth communication between security teams and developers, resulting in enhanced project efficiency and work productivity.
Development’s goal, of course, is to create functional products in the shortest possible time frame while still meeting the business requirements. Teams save valuable time and resources by not letting potential threats make it to vulnerable mitigation stages, which then become a bottleneck to production. These benefits become competitive advantages for early adopters of application threat modeling as more and more organizations continue to adopt the practice to secure development initiatives.
Operational Threat Modeling

Operational threat modeling allows organizations to visualize the “big picture” of its infrastructure risk profile and enhance the understanding of the full attack surface for key stakeholders. By utilizing operational threat modeling, organizational leaders are equipped to plan and prioritize infrastructure risk mitigation strategy.
The first step in operational threat modeling is to identify the operational environment, including shared components (i.e. SSO servers, encryption servers, database servers, and so forth). Next, every component’s attributes are considered to give additional context to the potential threats. For example, a database which has unrestricted admin access or large quantities of confidential data may have more potential threats than others. Finally, the potential threats and known common vulnerabilities (CVE), both internal and external, may be systematically identified and the relevant security controls enumerated.
Both Threat Modeling Types are Needed
Understanding how effective risk mitigation means different things to various departments within an organization can help businesses utilize the right threat modeling tools to minimize the entire organizational attack surface. Outdated threat modeling methodologies that use only one type of threat modeling throughout an organization is the equivalent of wearing a left-handed glove on both hands. The VAST methodology, on the other hand, effectively utilizes operational and application threat modeling to deliver effective processes for distinct security needs per department.
ThreatModeler is the #1 automated threat modeling platform, utilizing the VAST methodology to help organizations fortify their security strategy across departments. Easy to use, even without a security background, the ThreatModeler platform takes advantage of both application and operational threat modeling tools to deliver a holistic approach to security.
Want to see how operational and application threat modeling can increase productivity, lower costs, and mitigate threats to your business from the inside and out? Request a demo from our threat modeling experts today.

