ThreatModeler® Introduces v7.0
Bringing AI, Real-Time Collaboration, and a raft of Customization and Enterprise features.
secure, by design
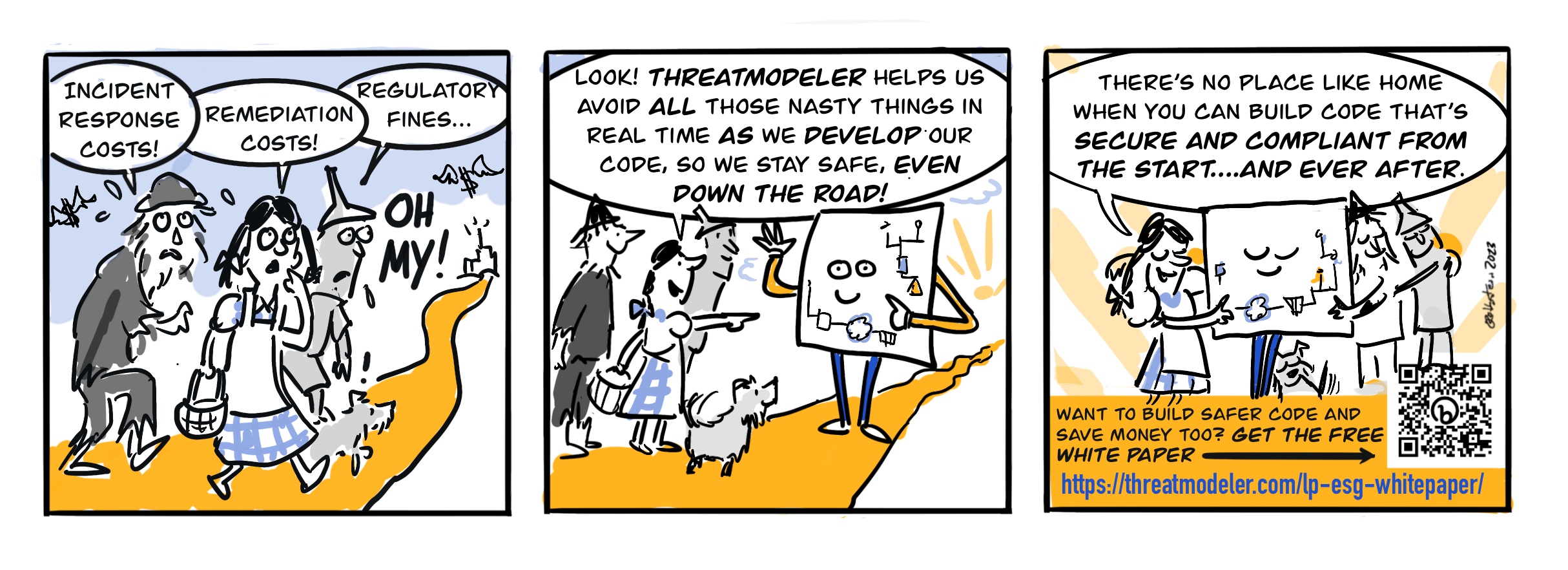
Watch how the ThreatModeler platform can securely design, build and validate from development through deployment — at a fraction of the time and cost tied to other tools.
OUR
PRODUCTS
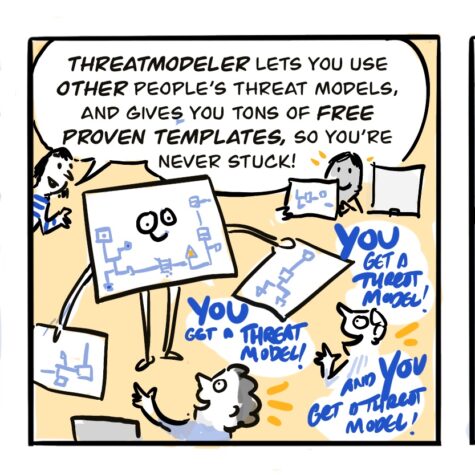
01 THREATMODELER
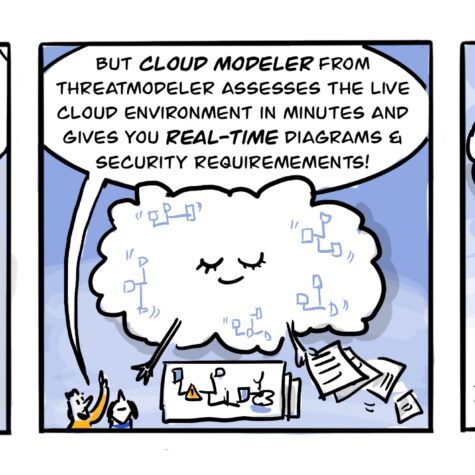
02 CLOUDMODELER
03 IaC ASSIST
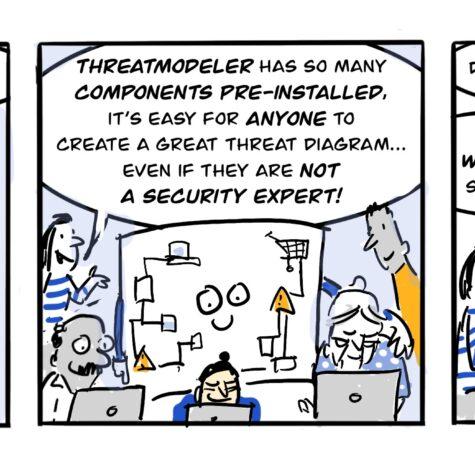
THREATMODELER SOLUTION CAPABILITIES
VISUAL & CONTINUOUS
The only platform to automatically, visually, and continuously detect design flaws.
CODE TO CLOUD
Faster, more secure enterprise cloud migration and deployment.
UP-TO-DATE, LESS EFFORT
Our Threat Research Center keeps threat intelligence current with constant research on emerging threats, compliance, and best practices.
FLEXIBLE
Works in cloud, mobile, IoT and throughout DevOps.
COMPLIANT (AT LAST)
Build compliance into the foundation of your infrastructure with built-in regulatory compliance frameworks.
POWERS IaC
Provides continuous visibility into undiscovered design flaws through infrastructure-as-code (IaC) in realtime.
WHO NEEDS THE
THREATMODELER SOLUTION

Software Architect

Management


Finance
Chief Information Security Officer
Threat maps to serve as a “Universal translator” for all departments to understand where they fit in, what others are dealing with, and how it all fits together.
WHO NEEDS THE
THREATMODELER SOLUTION

Software Architect

Management

Chief Information Officer

Finance
CODE-TO-CLOUD
“CloudModeler did not just empower our team with visibility into the threats facing our cloud infrastructure, it also enables us to push security to the left in our CDLC. The real-time capabilities of CloudModeler illustrated the interconnectivity of our product data, empowering us to determine how to secure our growing technology offerings most efficiently.”
— Abhishek Rath, Security Engineer, Sisense
— Abhishek Rath, Security Engineer, Sisense


“CloudModeler did not just empower our team with visibility into the threats facing our cloud infrastructure, it also enables us to push security to the left in our CDLC. The real-time capabilities of CloudModeler illustrated the interconnectivity of our product data, empowering us to determine how to secure our growing technology offerings most efficiently.”
— Abhishek Rath, Security Engineer, Sisense
— Abhishek Rath, Security Engineer, Sisense