Hackers Are Using Phishing Tactics to Feed on Coronavirus Fears
The recent coronavirus outbreak has triggered a global state of panic. Not only in the healthcare field, but also in the world of cybersecurity. With the virus frightening everyone worldwide, hackers are taking advantage of the fear factor by setting up fake websites purporting to sell products that will “cure” the disease. In addition, hackers are using social engineering to send fake emails, texts and post social media that try to convince targets to grant access to their personal information.
All this turbulence about the coronavirus epidemic has driven threat actors to rely on fears about the coronavirus to manipulate various global malware campaigns. Cybercriminals are spamming companies with malicious emails masked as precautions, that also predicate on financial detriment that could arise as the disease spreads.
Hackers are looking to manipulate the pervasive craving for news about the outbreak by using it as a phishing trap. The ongoing expansion of cyberattacks around the coronavirus through phishing emails propagate conspiracy theories of an unannounced cure. Cybersecurity experts are keeping an eye on the cutting-edge news and reports around the worldwide Coronavirus outbreak for malicious activity.
Examples of Coronavirus Phishing Attacks
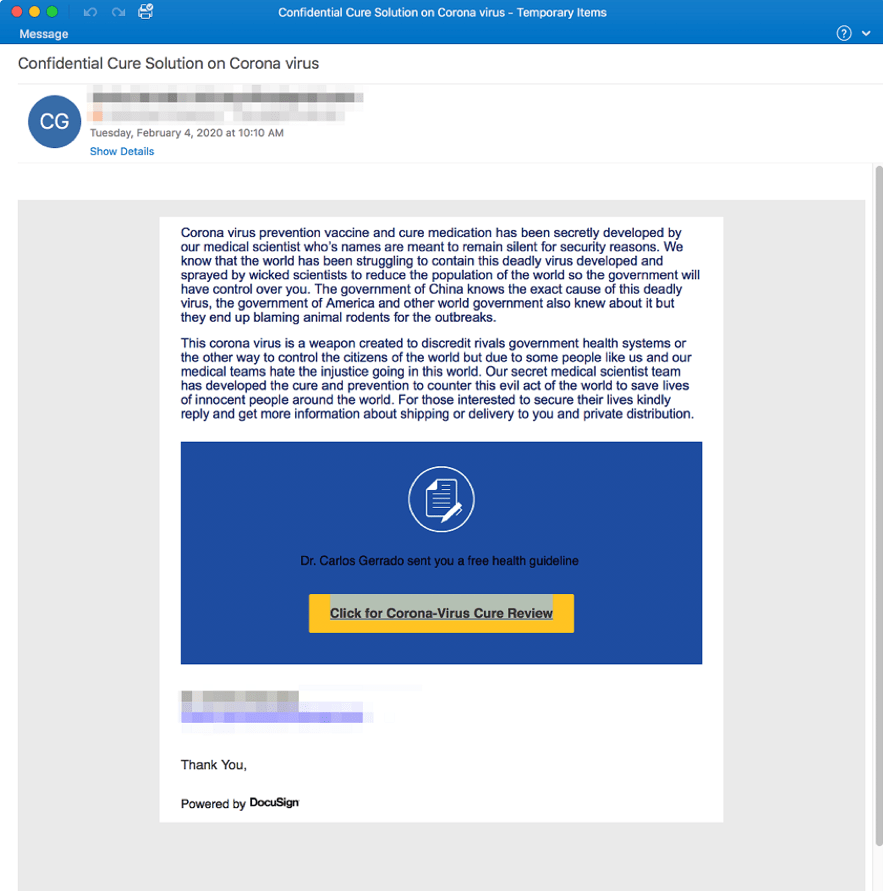
1. Coronavirus “Secret Cure” Phishing Email

2. Coronavirus “Safety Measures” Phishing Email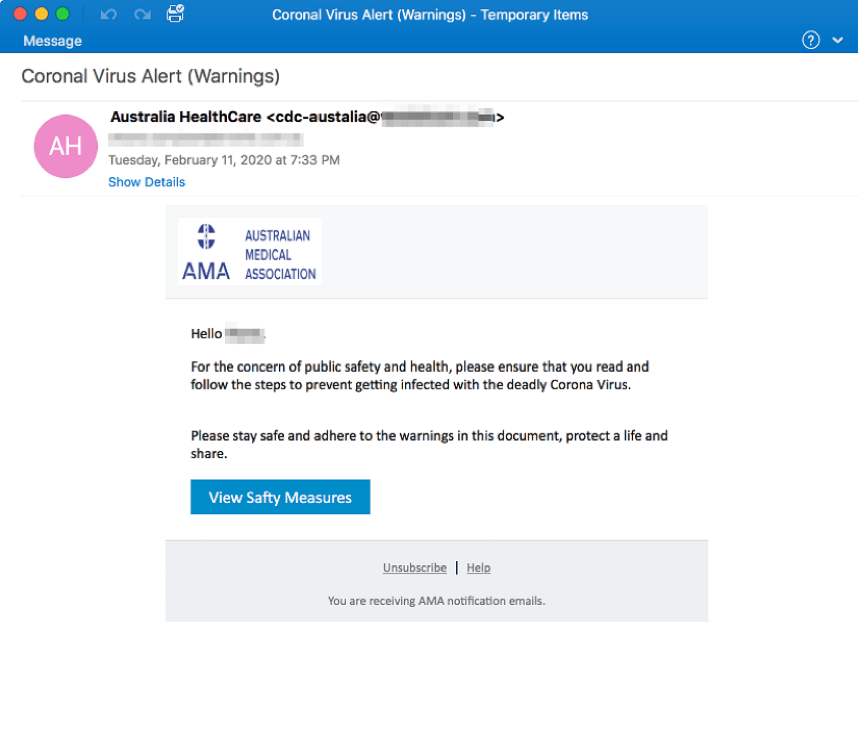
3. Coronavirus “Virus Alert” Phishing Email
Tips to Prevent a Phishing Attack
As threat modelers, we care about your privacy and security. We are always one step ahead of the game when it comes to protecting your security. Here are some tips to prevent a phishing attack:
- Authenticate the sender via email address. Verify the sender has an email address such as ‘person@threat.modeler’ If there is anything other than ‘threat.modeler’ after the ‘@’ symbol, this sender is not from ThreatModeler. ThreatModeler does not send email from addresses ending in ‘@threat.modeler.com’, ‘@threat.modeler.org’ or ‘@threat.modeler-safety.org’ for example. Don’t forget to right-click on the link to see what the actual sender address is. In even more sloppy phishing attacks, the email address won’t even resemble the name.
- Before you click any link, double-check it. Always double check that the link is a secure link, i.e. https, rather than the less secure http. We also recommend using Google Transparency Report, which examines input URLs for security.
- Before giving away any personal information, always verify the asker. Always consider why someone wants your information and if it is fitting. There is no reason someone would need your username and password to access public information. Furthermore, organizations will not ask you to divulge private information via email.
- Stay calm if you currently have personal information compromised. If you think you have given data such as your username or passwords to hackers, change the credentials on each site where you have used them right away. Report the data compromise to regulating authorities and the organization that owns the website.
Hackers Are Using Extortion to Convince Google Adwords (Now Ads) Users to Cough Up the Dough
In an aggressive move that is akin to ransomware, hackers are demanding that targets pay up in Bitcoin to prevent a flood of junk, direct bot generated traffic. Hackers say that bots have a 100% bounce rate ratio with thousands of rotating IPs. If the amount of inbound traffic crosses a threshold, Google will flag and suspend the account, creating downtime that can result in damages such as financial losses.
The amount of money demanded by the malicious actors is $5,000. In any form of ransomware, whether it be targeted or indiscriminate, hackers bet that at least some of those targeted will pay the ransom. In some cases, the amount paid to the actors will be far less than the amount lost in the event that the website goes down.
Google told Krebs on Security that the threat letters are clearly an act of sabotage. In their statement to the website, they spoke of protective measures implemented to prevent this form of extortion from going to fruition. “For example, we have detection mechanisms in place to proactively detect potential sabotage and take it into account in our enforcement systems.” For example, Google has a filter that prevents a majority of these types of emails from passing through.
Google’s definition of invalid traffic is pretty straightforward. Google says that, in regards to clicks and impressions, “Invalid traffic includes any clicks or impressions that may artificially inflate an advertiser’s costs or a publisher’s earnings. Invalid traffic covers intentionally fraudulent traffic as well as accidental clicks.”
Krebs on Security reported on the extortion just a few days ago, here is an example of the email.
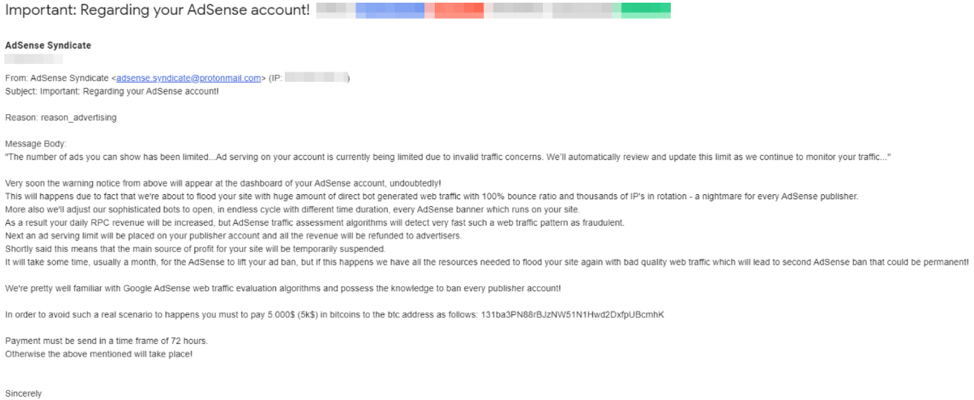
Threatmodeler Will Help You to Prevent Your Next Phishing or Ransomware Attack
ThreatModeler is a revolutionary platform that can help organizations to automatically scale across their entire IT ecosystem. With ThreatModeler’s integration with leading cloud provider AWS, and its cloud-ready content library, DevSecOps teams can detect, identify and predict threats. From servers, to web, to mobile to IoT-embedded systems, ThreatModeler helps enterprises to list out all the threats and vulnerabilities and determine the best mitigation strategy.
ThreatModeler also provides supporting reporting and documentation to conduct a holistic risk analysis, with an understanding of the different components and a baseline of understanding of the threats involved. For example, ThreatModeler helps organizations to think like a hacker to inform penetration testing. To learn more about how ThreatModeler™ can help your organization build a scalable threat modeling process, book a demo to speak to a ThreatModeler expert today.
Tech Accord Webinar Featuring ThreatModeler
Register now for an upcoming webinar presented by the Cybersecurity Tech Accord, which takes place on Wednesday, February 26, 2020 at 1pm ET. The webinar, presented by Alex Bauert, Sr. Director, Threat Intelligence at ThreatModeler, is titled “How to Achieve Secure CDLC Through Threat Modeling.” As more organizations migrate to the cloud, secure Cloud Development Life Cycle begins as early as the design and planning stages. We will explain the value of threat modeling to create a CDLC diagram to map out the attack surface, identify security threats and requirements, and strategize on threat mitigation. Our ThreatModeler experts will also highlight architecture pattern standards, and offer guidance for vulnerability management assessments, plus prioritization of remediation, resolution and mitigation. We hope that you can attend.






