Everyone, it seems, is doing it – shifting cash outlay from capex to opex by migrating to the cloud. Those who make the leap to cloud computing see significant benefits. Migrating away from on-premises deployment environments, though, is not an idyllic yellow-brick road of scalability and cost savings. In addition to requiring a new way of doing things for the IT staff, cloud computing security, with its inherent highly interconnected ecosystem, comes with unique considerations.
This is particularly true for the media and entertainment industry where the attack surface is magnified by the sheer number of individuals making digital contributions and the dependence on third-party vendors, from original media acquisition to distribution and delivery.
Migrate to Cloud Computing Security
The media and entertainment industry is under intense market pressure from customers demanding more streaming, greater access over mobile devices, and anytime availability. Moreover, the media industry is seeing a significant shift in its revenue streams from traditional to internet-based sources.
As a result, media companies need to create more content, deliver it to market faster, while ensuring high quality throughout the process. The business realities in this changing environment demand that companies expand into a global digital marketplace where they will face additional competitive pressures – and yet they must still control their costs and find a way to focus on their core competencies.
Migrating to the cloud offers companies significant advantages in a highly competitive, demand-focused marketplace, including:
- Pay-as-you-go processing and storage to keep costs to a minimum;
- The capacity to dynamically scale computing and storage based on changing needs;
- Highly flexible output and data transfer capabilities that adjust with unpredictable customer demand;
- Increased agility, automation, and collaboration with vendors and partners to shorten the time to market for new content; and
- An instantaneous global availability without the need to commit to massive infrastructure builds
However, along with the numerous advantages to the cloud come certain new threats and risks associated with a highly interconnected cyber ecosystem and rapidly evolving cyber threats landscape. Media companies and workflows are attractive targets for both financially motived and state-sponsored attackers.
If the benefits of the cloud are to be fully realized and maintained, the media industry must migrate to cloud computing security. Securing a media production end-to-end requires taking a “big picture” view of the workflow and the required IT ecosystem. Because of the inherent complexity of producing media, gaining a “big picture” view of the end-to-end security picture requires enterprise threat modeling.
Understanding the End-to-End Workflow in the Cloud
From a high perspective, media production and distribution can be broken down into 8 major workloads:
- Content acquisition – including capturing source content, encoding, encrypting and transferring content;
- Post-production work – including visual and special effects, editing, and rendering;
- Digital asset management and archiving – to store the studio’s work including tagging content and adding metadata;
- Media supply – including moving the mastered content, quality control, and delivery to various outlets;
- Over the Top – a digital content outlet providing live feeds and streaming content. Most consumers are very familiar with this segment’s major players including Netflix, Amazon Video, and the BBC;
- Playout and Distribution – Another digital content outlet providing streaming via direct connect. Discovery Communications is an example of such an outlet.
- Digital Publishing – aggregation and streaming of published content; often used by digital magazines and newspapers; and
- Analytics – including the analysis of viewing data and social media feeds to predict user behavior and other outcomes.
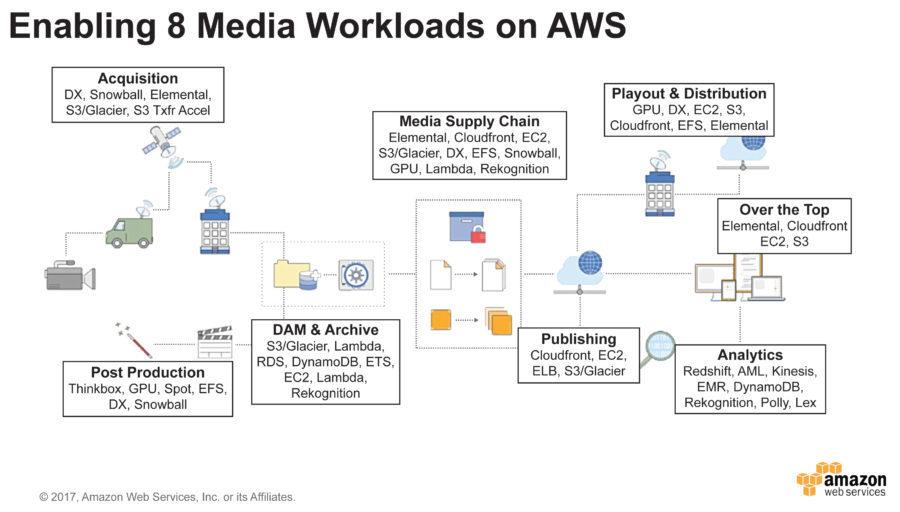
Threat Modeling for Cloud Computing Security
From the above high-level architectural diagram of the major media workflows, we can build an end-to-end threat model that will identify and prioritize the cloud computing security issues faced by the media and entertainment industry.
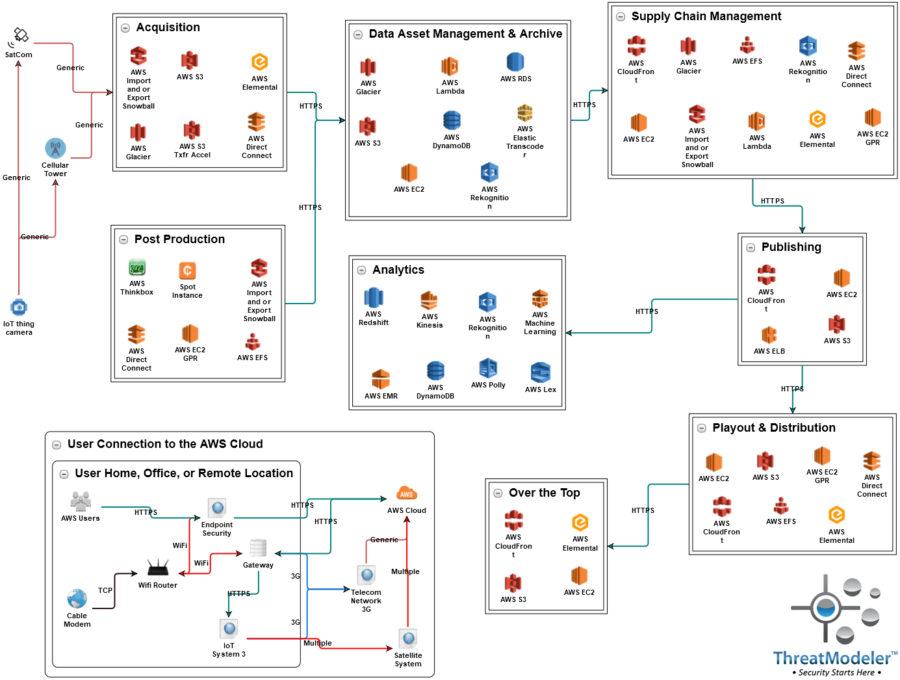
The above threat model identified 540 potential threats and 460 security requirements across the eight major media workflows when deployed to the cloud.
In this threat model, each container group (i.e. Acquisition, Post Production, and so forth) corresponds to one of the major media workflows identified in the AWS diagram. Each group is representative of an independent cloud deployment instance in as much as each workflow may be assigned to one or more independent third party vendors. The above threat model diagram shows the entire media workflow from original content acquisition at the upper left corner to distribution and analytics.
User connections are represented in the above threat model diagram with the User Connection group in the lower left corner. Connections to the any of the cloud deployments may be made through a user’s desktop or laptop computer or any number of IoT devices – each of which is represented by nested threat models. ThreatModeler allows for the inclusion of previously completed threat models as architectural components into any other threat model.
The computing endpoint may connect directly to the AWS cloud through the Internet. IoT devices may connect either through a telecom network or through a satellite connection – both of which are also represented by nested threat models.
In addition to the security issues of users connecting to the cloud, specific cloud computing security issues are identified by the AWS Cloud icon representing potential configurations of any one of the media workflow deployment environments.
If you would like to learn more about how enterprise threat modeling with ThreatModeler can help you develop better cloud computing security, then schedule a live demo today!






