In today’s rapidly evolving, highly interconnected cyber ecosystems, attempting to produce that increase through fixed-capacity, on-premise infrastructures and data centers are infeasible. Cloud computing – whether through Amazon Web Services (AWS), Azure, or other providers – provides the flexibility, scalability, and affordability IT leaders need to generate greater value from their IT systems. However, securing a cloud deployment is different from securing an on-premises system. AWS cloud threat modeling is therefore needed to fully understand the unique threats involved with migrating applications to the AWS platform.
Learn How to Create a Basic AWS Cloud Threat Model
Watch this short video on how to create an AWS cloud threat model with ThreatModeler™.
March’s Threat Model of the Month
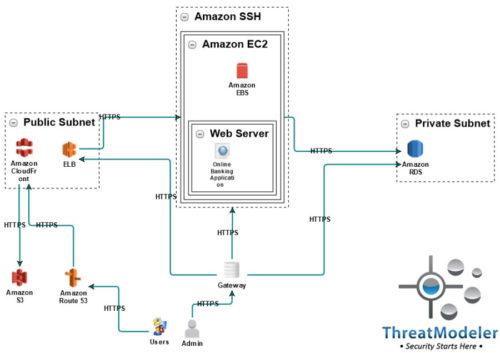
For the second installment in the Threat Model of the Month series, we are presenting a basic AWS web app hosting a threat model for the deployment of a critical or high-demand web application. Our AWS threat model illustrates a basic cloud-native architecture which can easily be expanded for additional cloud services or redundant systems.
Most cloud computing providers have a “shared responsibility” security model. In plain language, that means the cloud provider is responsible for the security OF the cloud. However, the computing client is responsible for security IN the cloud.
Customers are responsible for protecting their own digital content, as well as the platform, applications, systems, and networks they deploy in the cloud. The customer’s cloud security responsibility is essentially the same as they have for their on-premises systems, but it invariably requires understanding the unique threats involved with utilizing the cloud provider’s services.
Learn More: Benefits of Understanding Your Cloud Application Attack Surface
In this AWS cloud threat model, the client’s deployed web app resides on a virtual web server which is running on an AWS EC2 – or Elastic Computing Cloud – instance. In place of the traditional on-premises database, the EC2 communicates with an AWS relational database service on the back end.
Managing the incoming user traffic is a public subnet in which we have the Amazon content management system and static resource storage services – the CloudFront and S3 services, respectively. As part of the AWS recommended architecture, we also show an elastic load balancer which distributes the incoming load across as many, or as few, EC2 instances as may be appropriate for the incoming traffic level.
Why AWS Threat Modeling is Necessary For Cloud Security
Meeting today’s IT challenges as well as being strategically positioned for tomorrow’s opportunities, makes cloud computing a must-have rather than a nice-to-have. Whether organizations are considering deploying a single application to the cloud, migrating their datacenter, or creating a complete serverless architecture, their cloud environment becomes a part of the organization’s comprehensive attack surface. As such, organizations need cloud threat modeling to fully understand and effectively address the Cloud’s unique potential threats.
Request a demo to learn more about AWS cloud threat modeling with ThreatModeler™






