In our previous articles comparing ThreatModeler™ and Microsoft Threat Modeling Tool (Microsoft TMT), we considered the tools from an AppSec perspective and the CISO’s perspective. In this installment, we compare the capacity of each to provide outputs based on realistic threat modeling of a modern enterprise IT environment as embodied by an online banking application running within the bank’s deployment environment(s).
Realistic Threat Modeling of Modern IT Environments
The validity of modeling outputs – whether one is working with a business financial pro forma, solving a mechanical engineering problem, or creating a threat model – depends entirely on how well the model represents the dynamic nuances of the real system. For example, almost anyone can create a static set of business financials – which will be valid for precisely one particular circumstance described by the pro forma assumptions.
The chances, though, of a dynamic business environment filled with competitors, regulatory changes, supply chain challenges, and the interactions of real people settling into that one specific circumstance described by static assumptions are next to zero. The net result is the static financial pro forma can be an “interesting exercise,” but it is virtually worthless for generating actionable outputs.
The same applies to any modeling. Actionable outputs are the result of accurately modeling reality. Hence, when comparing threat modeling methodologies, it is essential to evaluate each tool’s capacity for realistic threat modeling of the complexities and the full scope of the cyber environment. After all, getting it wrong with cybersecurity can have devastating consequences for the organization.
Learn about VAST threat modeling: Threat Modeling Methodologies: What is VAST?
The Online Banking Application Threat Models Used for Comparison
To create the best possible comparison between ThreatModeler™ and Microsoft TMT, an independent security expert generated an online banking application threat model using both tools. Every effort was made to create comparable threat models – with the understanding, of course, that ThreatModeler™ and Microsoft TMT are very different tools.
The Microsoft TMT threat model was based on the following data flow diagram (DFD):
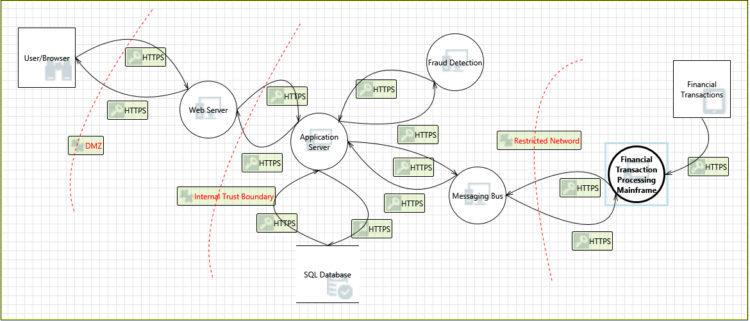
As would be expected, the Threat Modeling Tool DFD captured how the online application caused data to flow through the various infrastructure components. However, DFDs by design only provide a high-level, abstraction of a modeled system. The DFD cannot, therefore, capture the particular source of any threat. DevOps team members working on this project will likely require direct input from security team members to pinpoint where security controls should be implemented.
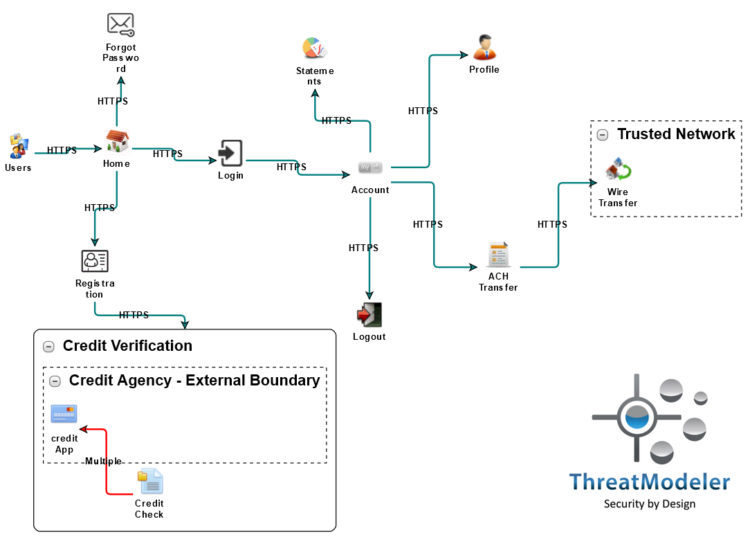
The ThreatModeler™ threat model was based on the following architectural diagram. Note, this is a diagram of a hybrid infrastructure. The online banking application is precisely modeled as a nested threat model within the server cluster inside the trusted network. Microsoft TMT’s threat model includes a single component for fraud detection, whereas the ThreatModeler™ diagram has a second nested threat model – SiteMinder – which is a shared component throughout the organization’s IT environment.
Head to Head Comparison of ThreatModeler™ and Microsoft TMT
The architecturally based visual diagram built in ThreatModeler™ provides more realistic threat modeling of the modern IT environment based on general capabilities of each tool, the specific capacity of each tool to represent the modern IT environment based on those capabilities, and the outputs generated by each tool:
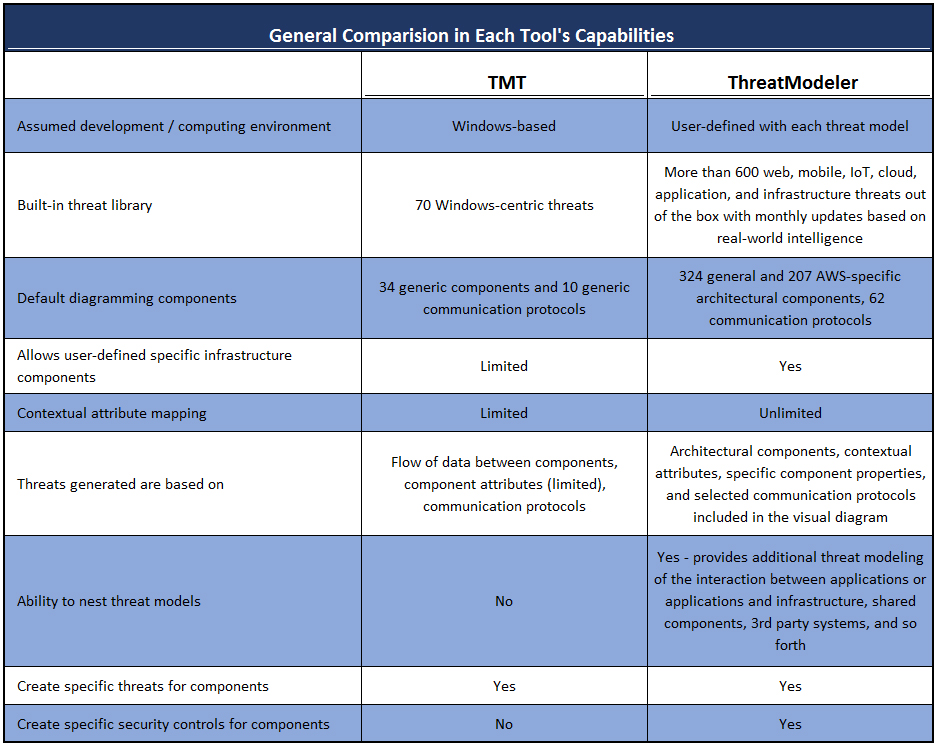
As can be seen by comparing the general capacities of each threat modeling tool, if the system under consideration is Windows-based, both tools can provide realistic threat modeling of the environment. However, outside a Windows development environment, Microsoft TMT’s capacity to provide actionable outputs becomes severely limited compared to ThreatModeler™.
The differences between Microsoft TMT and ThreatModeler™ in their respective capacities to real threat model an enterprise IT environment is further illustrated by the threat models created by the independent security expert:
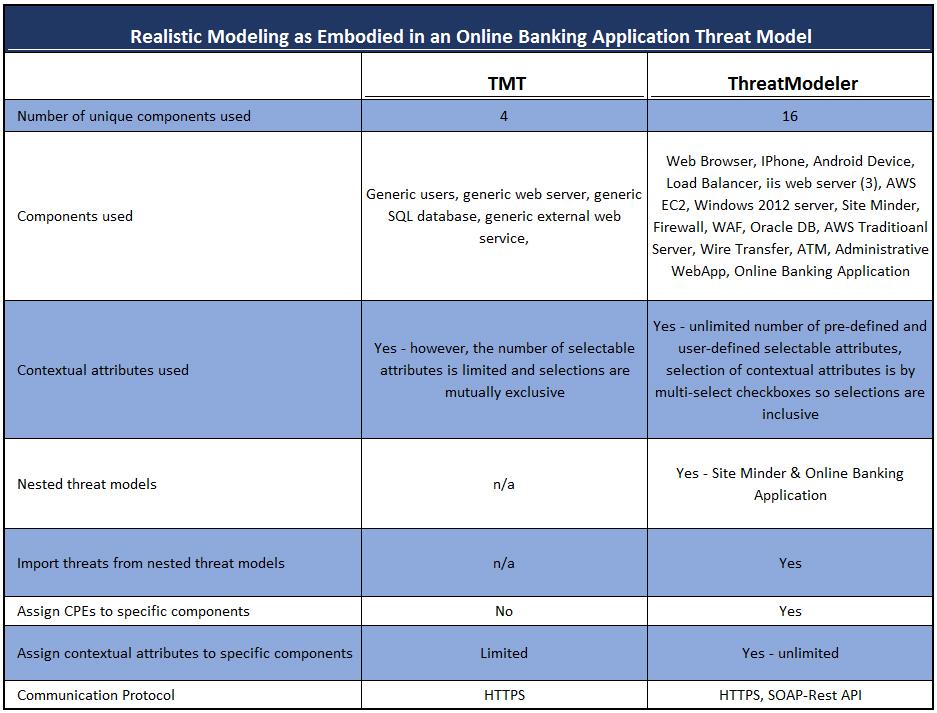
The ThreatModeler™ architectural diagramming provides a much finer granularity and specificity in components – yielding much more realistic threat modeling of the IT environment. Furthermore, the threats identified by ThreatModeler™ are based on the architectural components placed and the contextual attributes and properties selected for each component. Users – including DevOps team members – can therefore quickly trace threats to their source and know which security requirements to implement for each part of the project without direct input from security team members.
Finally, we can compare the outputs of Microsoft TMT and ThreatModeler™:
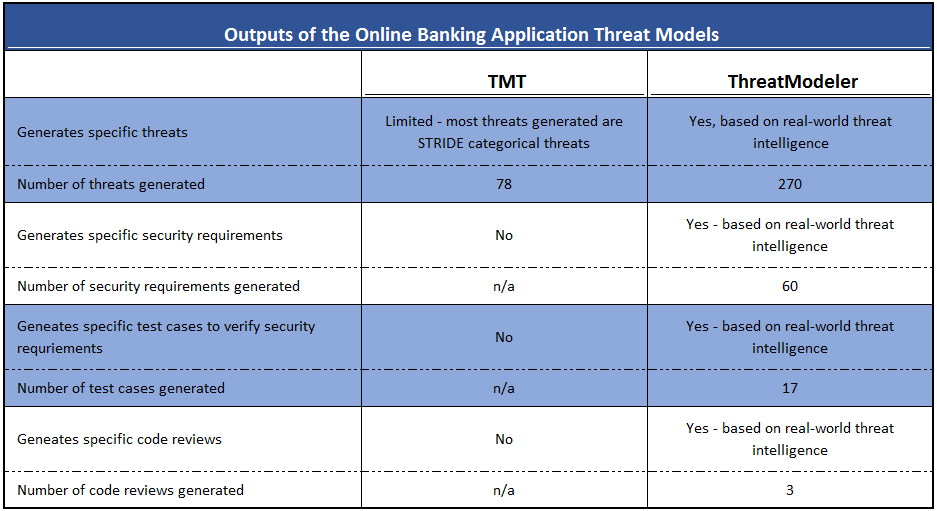
ThreatModeler™, in addition to identifying more than three times as many specific threats based on real-world intelligence rather than general categories, also
- Enumerates and discusses specific security requirements;
- Provides the contextual attributes assigned to each component;
- Identifies the source of each threat; and
- Provides specific details about each threat identified.
ThreatModeler™ Provides the Realistic Threat Modeling you Need
Threat modeling is a highly complex analysis, considering sophisticated applications within advanced deployment environments where applications interact, components are shared, and 3rd party systems are present. If that were not enough, the threat landscape evolves daily with new potential threats added continuously.
The value of the outputs provided by a threat modeling software is inherently tied to the tool’s capacity to generate realistic modeling of this dynamic environment. ThreatModeler’s architecturally-based approach creates the most realistic threat model possible of applications, mobile and IoT devices, industrial control and cyber-physical systems, and on-premises and cloud-based deployment environments – and provides contextually-sensitive modeling of the interactions that may exist between any of these.
Getting consistent, concrete, actionable threat modeling outputs to secure today’s increasingly complex IT ecosystems requires threat modeling with ThreatModeler™.
Want to learn more about how ThreatModeler™ provides realistic threat modeling of modern IT ecosystems?






