The need to analyze endpoint security is becoming increasingly important for organizations. Layered network security defenses are difficult to penetrate. However, once inside the perimeter, legitimate users and adversaries alike have much more freedom of movement. Thus the growing preference for adversarial actors is to conscript the aid of careless or disgruntled insiders – even without their knowledge – to simply bypass the defensive perimeter and initiate the attack from the inside. The recent global Wanna Cry and Petya ransomware attacks and the Crash Override attack on the Ukrainian power grid share striking similarities: they are all malware-based attacks which initiate inside the trusted network through end-user activities such as opening an email attachment or downloading a file from the Internet.
For the July Threat Model of the Month, we created a threat model that captures malware-based and other threats to organizational endpoints and shows how easy it is to analyze endpoint security configurations with ThreatModeler™.
Once the endpoint user allows the initial malware payload to activate on the local machine it is often too late. Frequently the initial infectious script’s primary purpose is to open a backdoor on the computer or a network server through which additional malware components can be called and loaded. The additional components are designed to take advantage of known vulnerabilities and to exploit potential threats, allowing the remote hackers to automate their nefarious activities and pursue their goals with impunity.
Security teams understand that insiders are, and will likely continue to be, the weakest link in any organization’s cybersecurity. Despite countless hours of training and security seminars, it only takes one employee or contractor in a moment of curiosity or carelessness, to install an unknown USB drive to see what is on it, or to attach their mobile device to the office network to sync files, or to brows a malicious website or download an infected file. In most cases, though, the initial malware payload enters through users opening innocent-looking email attachments.
How to Analyze Endpoint Security
There are three general levels of security, each of which is included in the threat model diagram below:
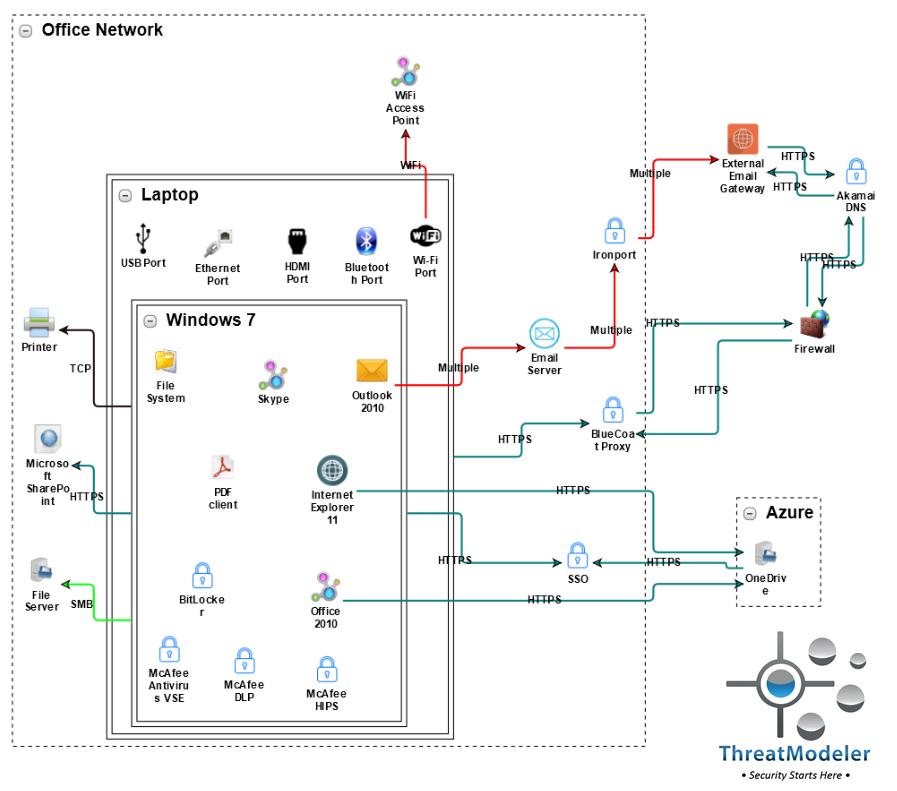
The first layer – illustrated by the Akamai DNS control and the Azure trust boundary – lay outside the organization’s network. This security layer is maintained by external service providers for the purpose of mitigating service disruptions and malicious redirections. Organizations have little to no influence on this security layer; it exists to protect the interests and reliability of the service providers.
The second level of security – the one which security and IT teams invest most of their resources – are those which form the organization’s defensive perimeter and internal trusted networks. These may include controls on the email server (i.e. IronPort) and Internet hub (i.e. Blue Coat Proxy), as well as a single sign-on component (shown above as SSO). Of course, security and IT teams need to find the proper balance between security and usability. Leaning too heavily on the security side may inhibit authorized users from performing their job functions, whereas too much user freedom is just asking for trouble.
The third level of security is often the most neglected, and is thus the favored adversarial entry point. Organizations can analyze endpoint security for effectiveness against specific threats. ThreatModeler allows users to conduct dynamic and detailed “what-if” comparisons of commercially available anti-malware bundles or other endpoint security controls in minutes, so leaders can determine the most effective endpoint security policies for their organization.
Furthermore, ThreatModeler allows security to quickly understand which specific threats – grouped by source and risk – remain unaffected by proposed or deployed security measures. Organizations can thereby take the appropriate measures to manage their residual risk based on the specific remaining threats.
The endpoint security analysis conducted through the above threat model identified a total of 212 potential threats across all three security levels, 143 of which are effectively mitigated by the deployed and contemplated compensating controls. The analysis could continue by choosing an alternative endpoint security control configuration and comparing the mitigation results.
The summary report for the above threat model is available for download here.
Schedule a demo to learn how easy it is to analyze endpoint security with ThreatModeler.






